In this first article, I’m going to introduce the French start-up Moabi, specialized in IoT Firmware Security, located in Paris, to be found at https://moabi.com
Moabi has received the 2019 prize for the most innovative startup at “Les assises de la sécurité et des systèmes d’information”, a Cybersecurity symposium held in Monaco every year in October
So, what do they have on offer ? Moabi has developed an innovative Reverse Engineering SaaS platform, dedicated to IoT binaries / embedded software, that is able to analyse the binary “on the fly”, with an all in one toolset. What is great is the ability to perform several types of static analysis and symbolic execution (the following being only a short list of the key features). You just need to upload your executables on the platform and you are good to go
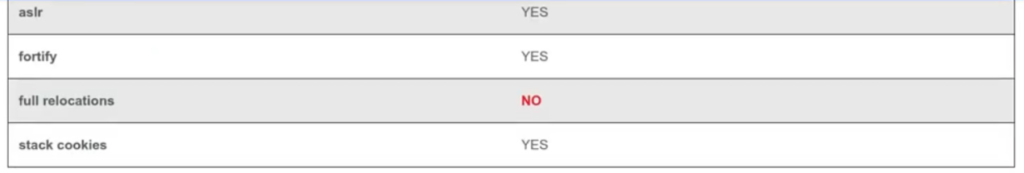
ASLR protection
Address space layout randomization (ASLR) is a memory-protection process for operating systems that guards against buffer overflow attacks by randomizing the location where system executables are loaded into memory
The success of many cyberattacks, particularly zero-day exploits, relies on the hacker’s ability to know or guess the position of processes and functions in memory. ASLR is able to put adress space targets in unpredictable locations. If an attacker attempts to exploit an incorrect address space location, the target application will crash, stopping the attack and alerting the system
Moabi platform detects the ASLR protection implementation, together with other protections
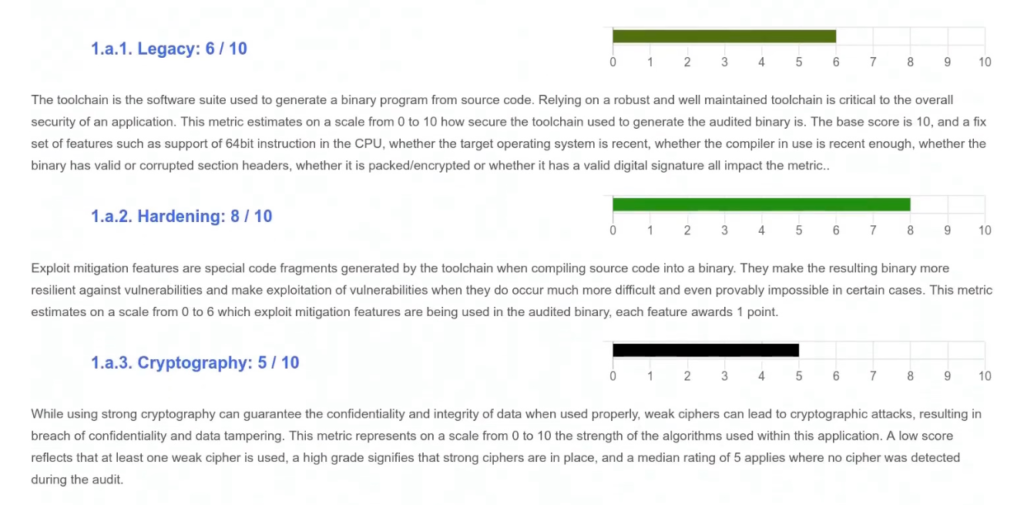
Cryptography
The toolset is going to detect the common cryptographic cyphers and their implementation, hence being able to assess the robustness of the cryptographic protection
Symbolic execution | taint checking
The package will analyse the executable using symbolic execution, taint checking, among others, and be able to detect common vulnerabilites CVE and implementation weaknesses in the code against standard coding norms
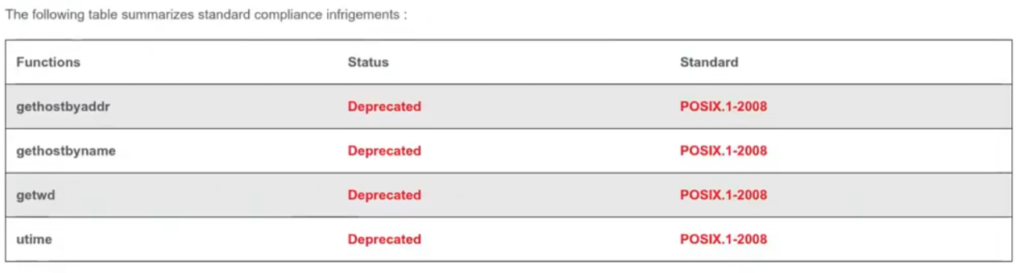
Static analysis, also called static code analysis, is a method of computer program debugging that is done by examining the code without executing the program. The process provides an understanding of the code structure, and can help to ensure that the code adheres to industry standards
Symbolic execution is a means of analyzing a program to determine what inputs cause each part of a program to execute. An interpreter follows the program, assuming symbolic values for inputs rather than obtaining actual inputs as normal execution of the program would. It thus arrives at expressions in terms of those symbols for expressions and variables in the program, and constraints in terms of those symbols for the possible outcomes of each conditional branch
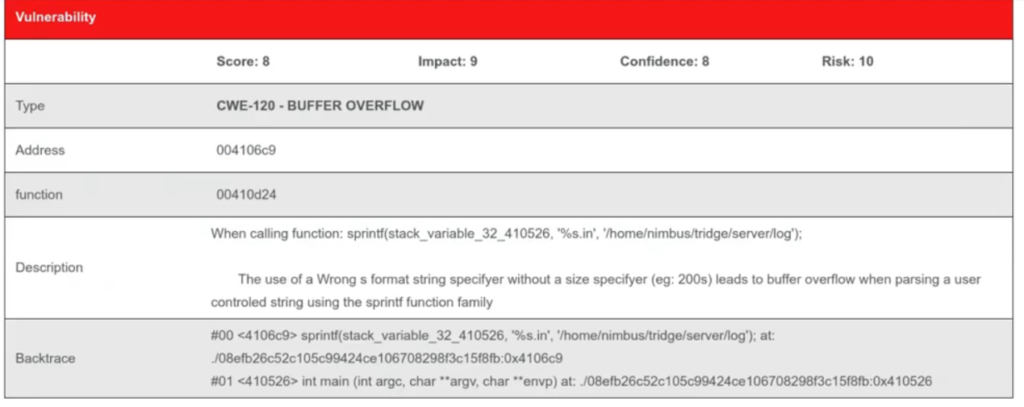
The concept behind taint checking is that any variable that can be modified by an outside user (for example a variable set by a field in a web form) poses a potential security risk. If that variable is used in an expression that sets a second variable, that second variable is now also suspicious. The taint checking tool can then proceed variable by variable forming a list of variables which are potentially influenced by outside input. If any of these variables is used to execute dangerous commands (such as direct commands to a SQL database or the host computer OS), the taint checker warns that the program is using a potentially dangerous tainted variable
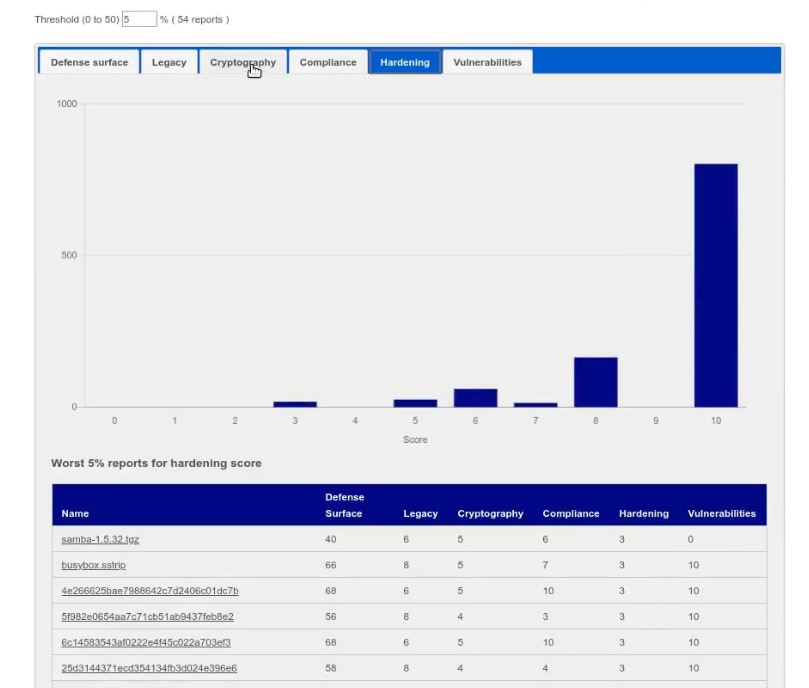
Risk assessment
At the end of the analysis process, the platform will generate a user friendly risk assessment with a global rating and by categories
The company has been co-founded by a famous French Security researcher, Jonathan Brossard (@endrazine on Twitter), with a strong background in Assembly, Reverse Engineering and speaker at several security conventions such as Defcon and Blackhat. He is the editor of the Witchcraft Compiler Collection WCC, a collection of compilation tools to perform binary “black magic” on the GNU/Linux and other POSIX platforms https://github.com/endrazine/wcc/blob/master/doc/presentations/Jonathan_Brossard_Witchract_Compiler_Collection_Defcon24_2016.pdf

Moabi has the famous Automotive car company Renault among its first customers, allowing them to assess a broad range of embedded software products. Moabi offer is of interest for many businesses such as drone, IoT, military, Industry 4.0. The introduction of the 5G norm will accelerate the expansion of IoT and push customers to increase the security of their embedded software. A very good opportunity for Moabi !
It’s definitely a good platform for any business who does not have the source code but wants to assess the overall security of the binary package (such as the OEMs versus the IoT sub suppliers), or a software editor who wants to qualify his software using an independant assessment
