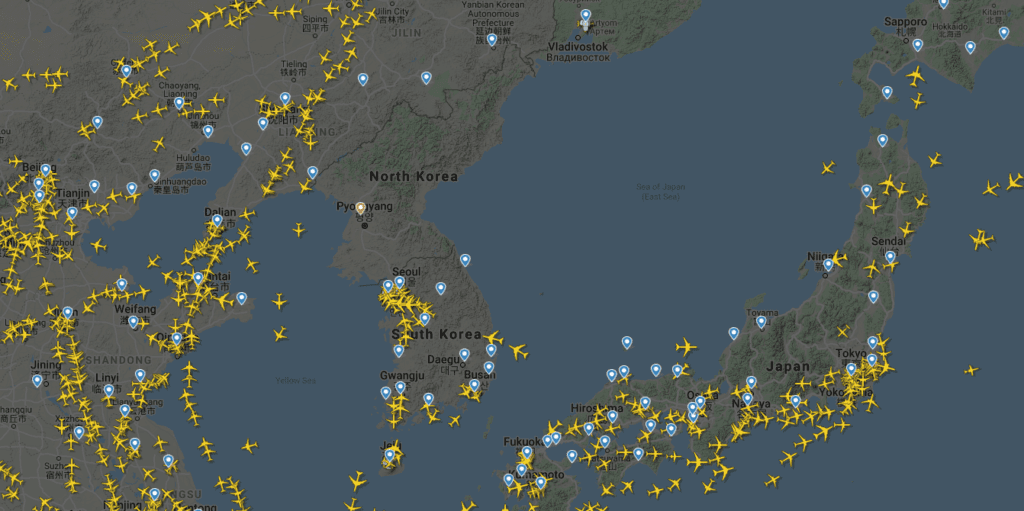
North Korea (“NK”), or DPRK – Democratic People’s Republic of Korea – is seen as a dictatorship, and a very isolated country, for some good reasons. On one hand, they have almost totally isolated their country from the Internet. On the other hand, we know that NK hackers are very active. This contradiction made me think that it would be interesting to dig in, and write an article about North Korea and the Web…so let’s go !

As an introduction, I would like to start providing a few hints about the physical isolation of NK. In fact, there is an extreme correlation between the physical isolation of NK and it’s degree of isolation on the web…bridging the two is helpfull to understand the overall situation
Isolation of North Korea
NK is a relatively small country of about 25 Million people, located in sandwich between China and South Korea. It has a small border also with Russia in the North East (near the city of Vladivostok)
NK is a stalinist – communist driven country. Here is a short reminder of it’s recent history :
In 1910, Korea – at that time, a unified territory – was annexed by the Japanese Empire. At the end of the second world war, in 1945, Japan capitulated and the Korean peninsula was separated in two parts, following the offensive of two superpowers, Soviet Union in the north and USA in the South. Negociations for a reunification being stalled between Soviet Union and USA, distinct governments are formed in the north and in the south. In 1948, the north intends to attack the south, leading to the Korean war between 1950 and 1953. The armistice between the two opponents will be a cease fire, but no peace treaty will ever be signed.
After the dislocation of the Soviet Union, NK will face a catastrophic famine. The Kim dinasty, at the head of the country, will lead a policy of “military first”, to strengthen the country and it’s government. At the same time, NK will take an ever increasing path towards a dictatorship, building concentration camps, deporting people, killing thousands of political opponents. As a “rogue nation”, more and more isolated, constrained by embargoes, NK will grow an illicit trade with some complicit countries. In this respect, because of the former Sino-Soviet relationships, and also some common business interests, NK will have specific ties with China and Russia, in many areas
Having said that, let’s have a deeper look at NK physical flows with its neighbors
Closed borders
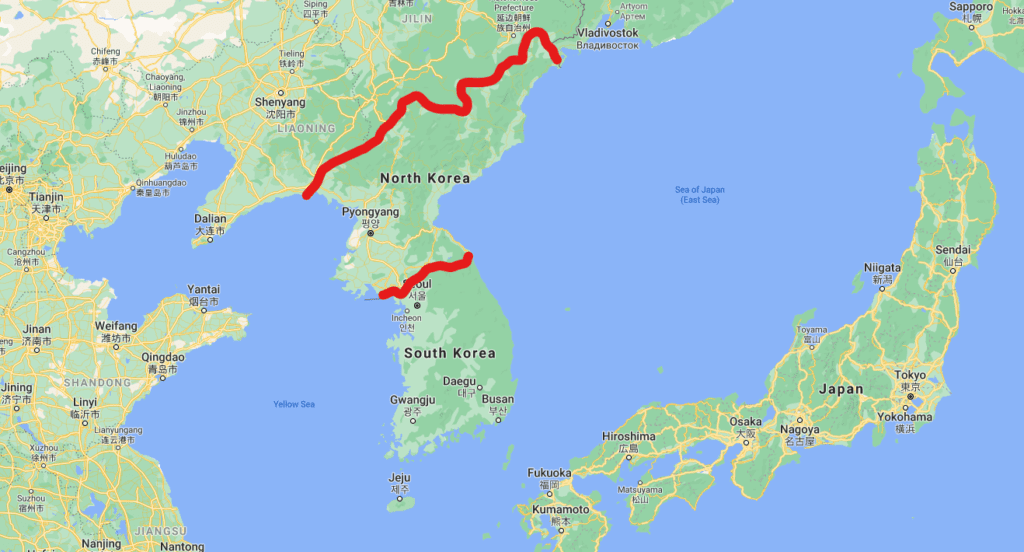
In the South, since the cease fire with SK, it has a so called DMZ – demilitarized zone – border with SK. This border is a very strong barrier as can be seen below. There is a single point of entry called the Joint Security Area
In the North East, it has a natural border with Russia, in a quite desertic and isolated area, with the Tumen River. There is only one bridge linking the two countries, the so called Friendship bridge. The overall area is poor and rather hostile
In the North, it has a natural border with mainland China, with the very long Yalu River. There are a few bridges across the river, the main one being the Sino-Korean Friendship Bridge, located in the Chinese city of Dandong (top left corner of the below photo). There’s a good article here if you want to know more about Dandong : https://bit.ly/3npFqZC
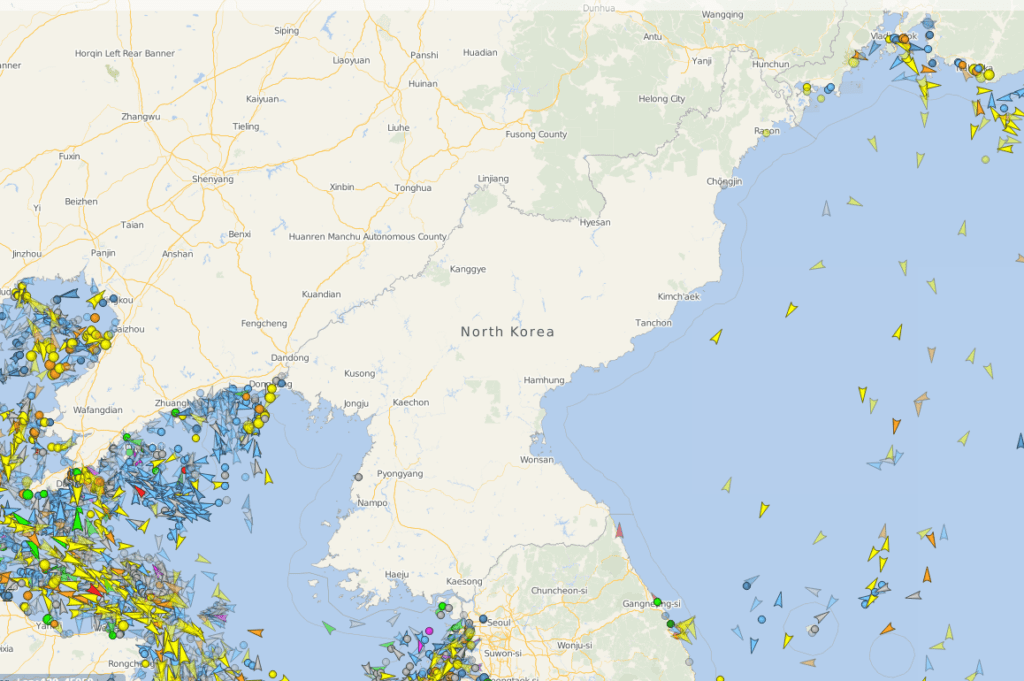
The sea traffic is very low as per global live traffic maps (in addition to the embargo, at the time of writing this article, NK had taken measures to limit sea traffic because of the COVID pandemic)
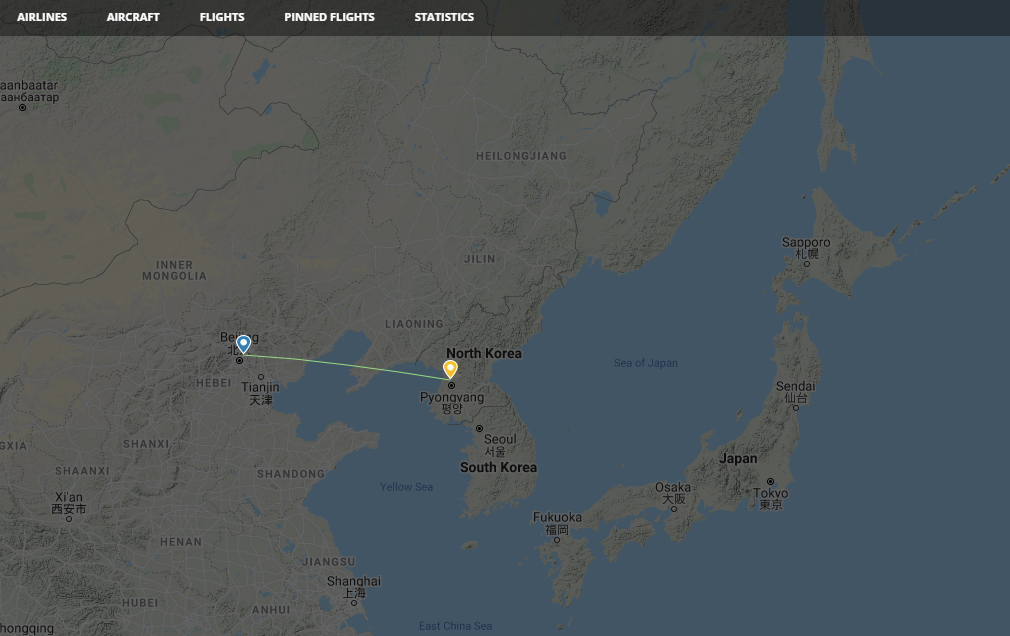
The air traffic is almost null, see below the captures of the today’s live traffic, and also the scheduled flights in the next 7 days…just one flight to Beijing in China !
For a much detailed navigator of NK topography, go to the excellent 38North web site : http://38northdigitalatlas.org/
Enough with geography data…I think you got it ! It sets the tone for what will see next
Internet cable routes
First of all, we can have a look at the submarine internet cables in the area of North Korea : https://www.submarinecablemap.com/
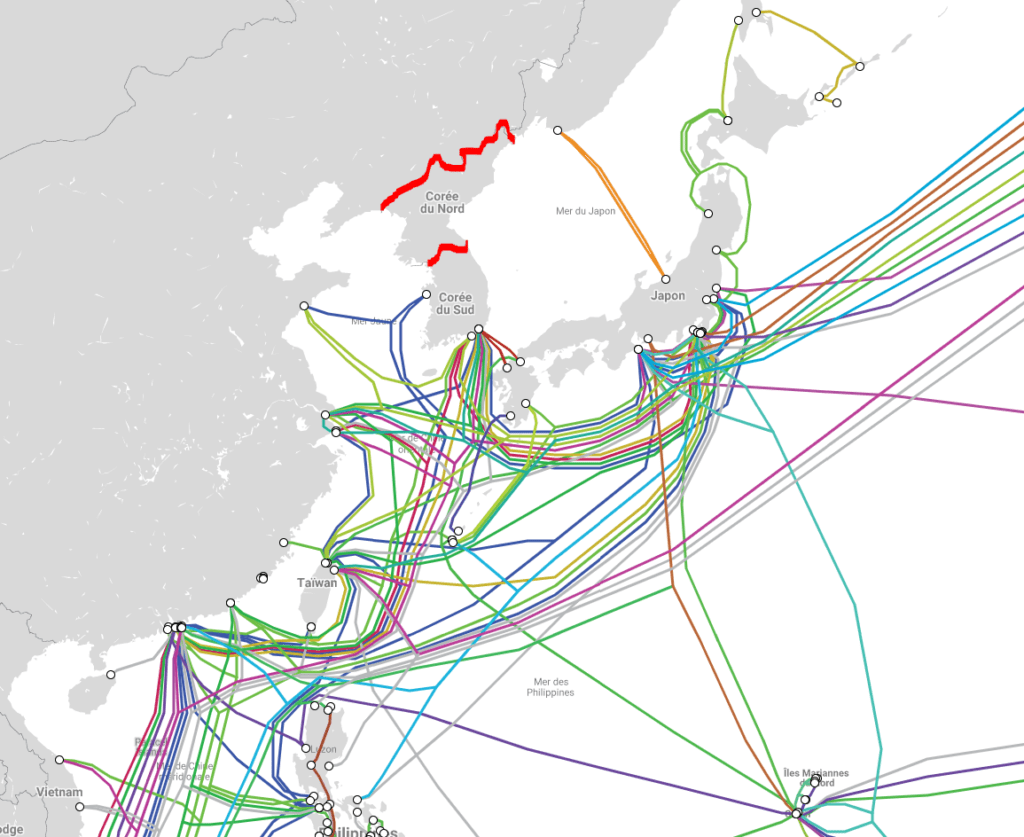
There are no submarine cables going to NK. Not surprising !
China Unicom has a notorious terrestrial cable going to NK, through Dandong
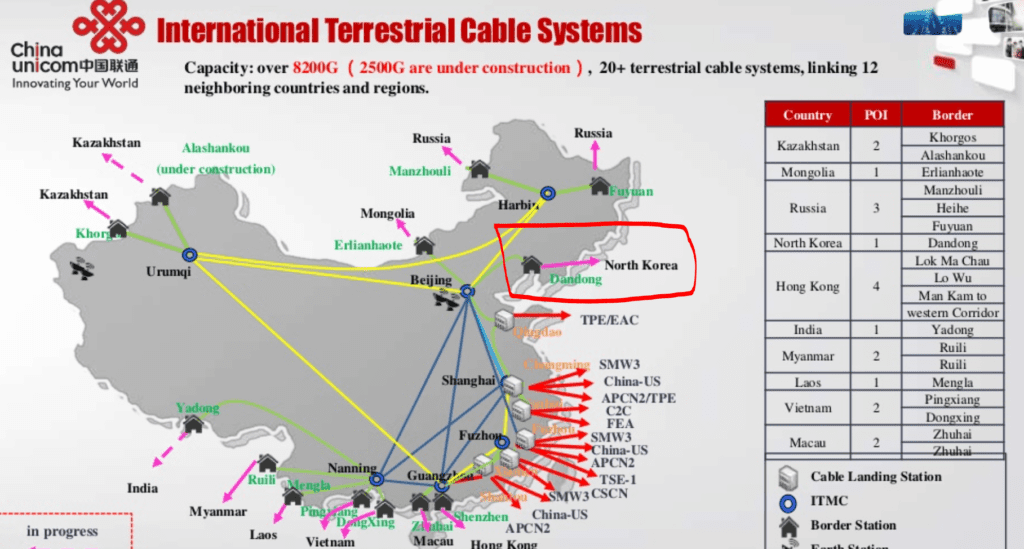
This cable goes along the Sino-Korean Friendship Bridge, seen above
There is also a cable running from Russia into North Korea, through the Tumen River Friendship bridge (again, seen above). It is operated by the Russian TTK – TransTeleCom
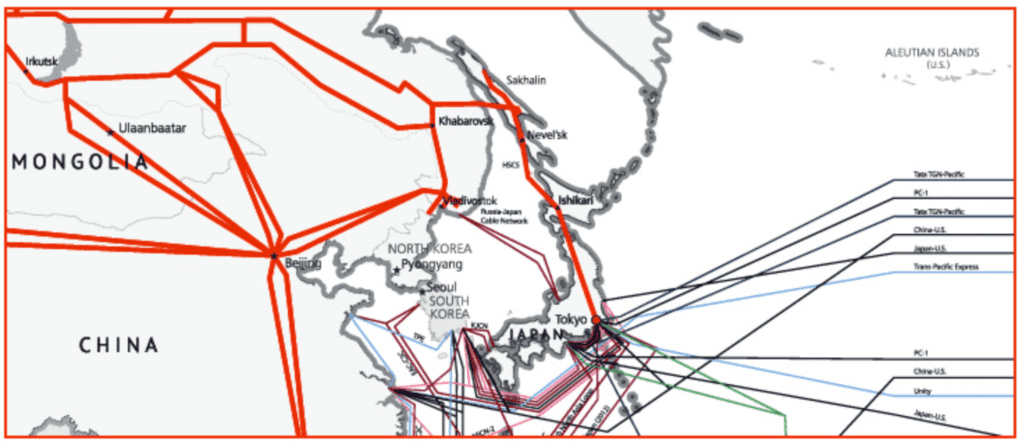
Before the opening of this second cable, NK was only relying on one cable, the Chinese cable. Therefore NK was not quite secure from an Internet access point of view. This cable was a “single point of failure”
The USA triggered a reaction from NK, when they decided to DDoS their internet line, following a spate of hacks from NK : https://www.38north.org/2017/10/mwilliams100117/
The Russian cable was put in service shortly after !
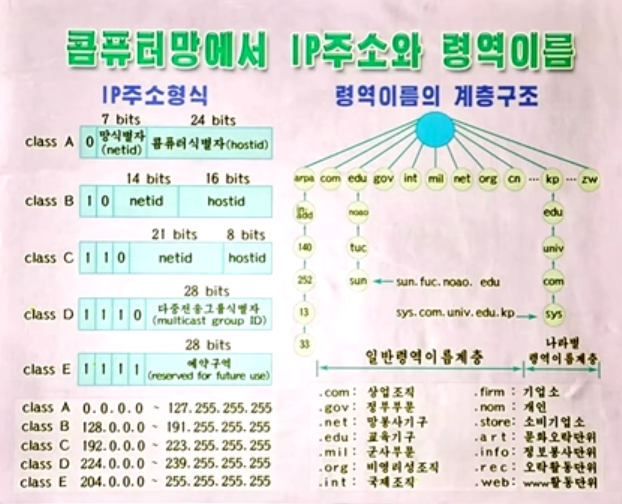
TLD – Top Level Domain of North Korea
I will start by providing an interesting number…how many internet users in North Korea ?
To answer this question, let’s go here : https://resources.potaroo.net/iso3166/v4cc.html
This link provides a full updated table of internet usage per country in the world : number of IP adresses, number of internet users,…
North Korea lies in the 240th position…with a number of internet users as low as 51 557 users. That means an internet access as low as Eritrea, but this African country only has 3.5 million people, while North Korea has about 25.7 million people…
Who are these users ? This article, based upon good data, explains that the Elite has access to the global Internet : https://www.recordedfuture.com/north-korea-internet-activity/
Let’s continue and have a look at the top level domain information from NK. For this, let’s go to the IANA website : https://www.iana.org/about
Let’s search into the Root Zone Database : https://www.iana.org/domains/root/db
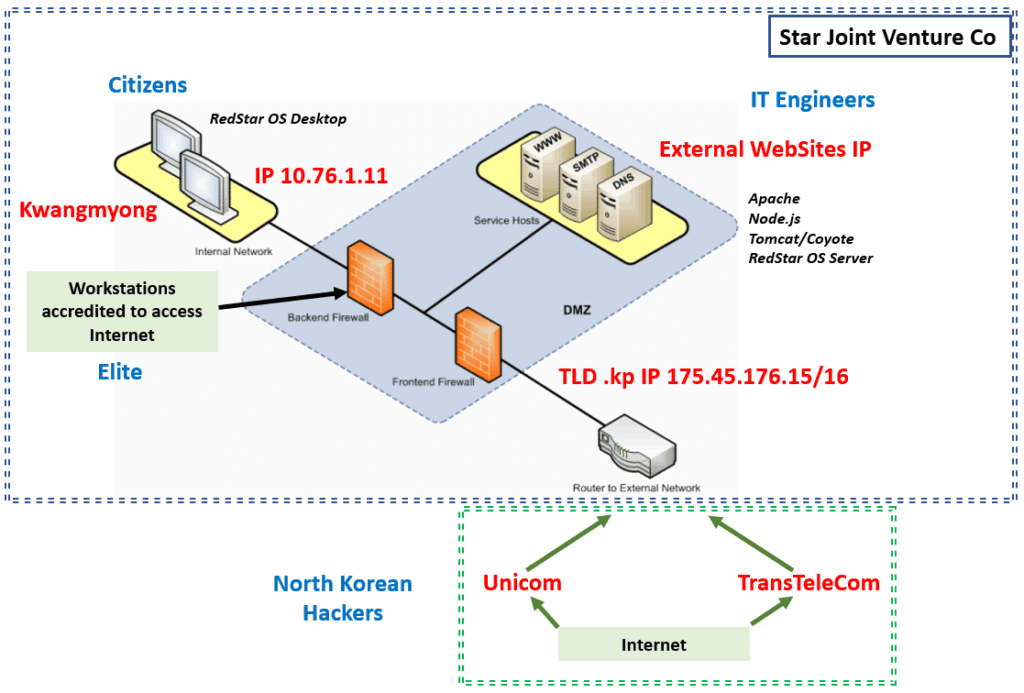
The TLD – Top Level Domain for North Korea is .kp. Searching in the database brings us to those details
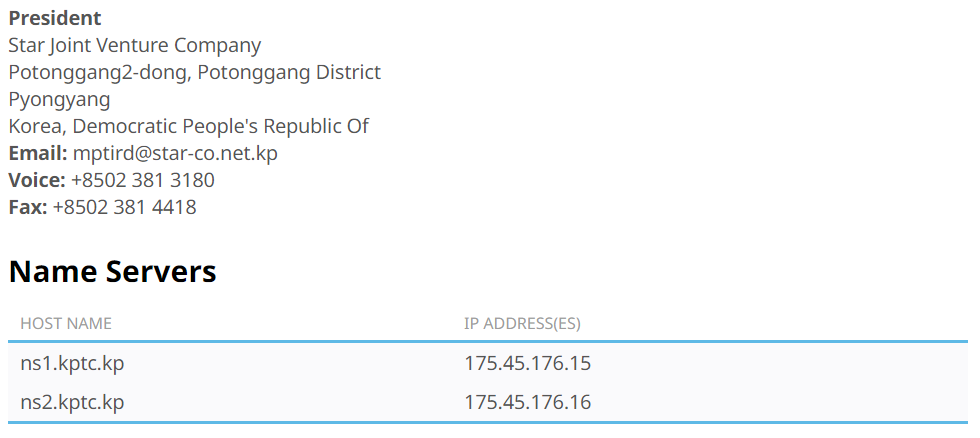
Who is Star Joint Venture Company ? It’s a joint venture between the Korean Post and Telecommunications Corporation, a NK governmental enterprise, and Loxley Pacific Company Limited, located in Thailand
Loxley is a Thai Conglomerate operating since many years, highly diversified in many business sectors : https://www.loxley.co.th/profile.html

One of their business units is specialized in Networking technology

You well get a good background in this article, about the ties between Thailand and North Korea : https://philipiglauer.wordpress.com/tag/thai-north-korea-ties/
Let’s check these IP adresses and see what we can learn from it. I use some basic search tools, such as https://network-tools.com/ and https://www.whois.com/. I’m doing a traceroute (to find out the network path from my location, to the destination IP in North Korea), and step by step, a whois search to find more informations about individual IPs found in the traceroute
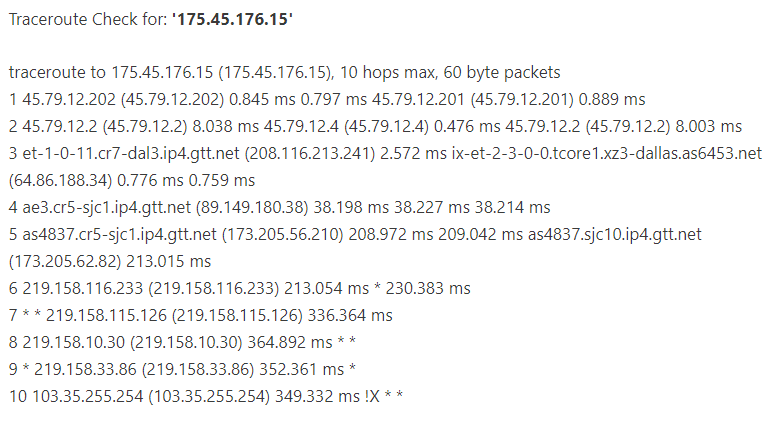
The route is the following : USA -> Germany -> USA -> China. The last node (103.35.255.254) before reaching North Korea, is CENBONGT-HK located in China, Hong-Kong province. Just before, we had the node 219.158.33.86, which is CHINA UNICOM
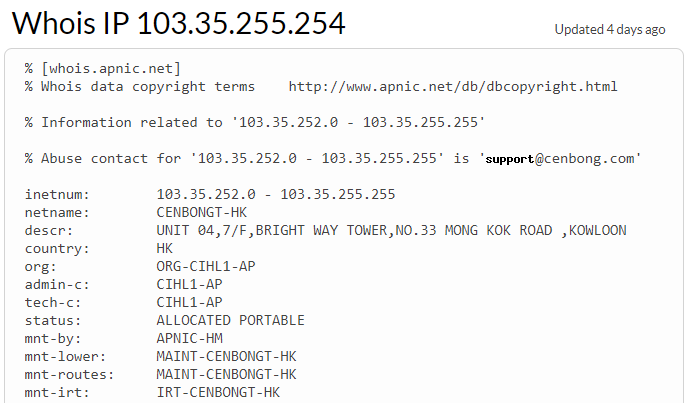
Let’s look for CENBONGT in this tool : https://whois.ipinsight.io/
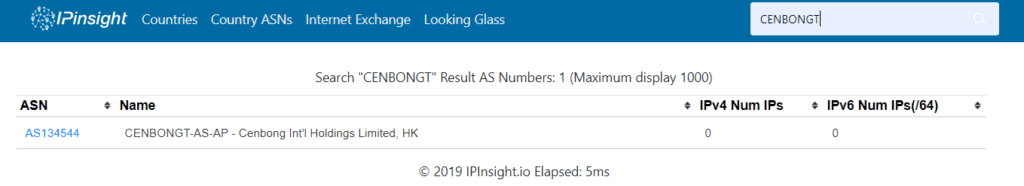
We find the AS number wich is AS134544. The AS number stands for Autonomous System Number (AS number or just ASN), and it is a special number assigned by IANA, used primarilly with Border Gateway Protocol, which uniquely identifies a network under a single technical administration that has a unique routing policy, or is multi-homed to the public internet
This autonomous system number is required, if you are to run BGP and peer with your internet service provider, and between internet service providers at peering points and Internet Exchanges (IX). The ASN must be globally unique so that IP adress blocks appear to come from a unique location that BGP can find, and route to this location
BGP uses Prefixes and Autonomous System Paths (AS Paths) to determine the shortest path to a destination where a prefix is located
Let’s click on AS134544, we find that this AS is linked to the CHINA UNICOM backbone, which is consistent with the previous node we found in the traceroute
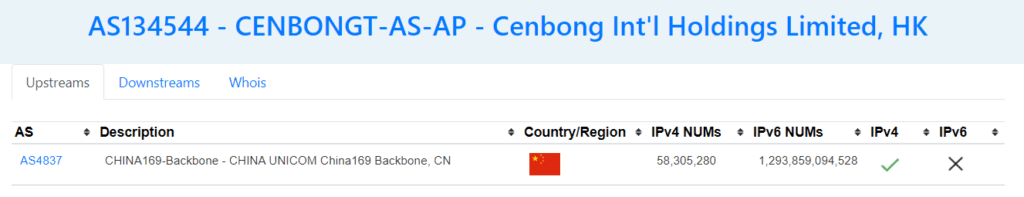
Then, let’s go “downstreams”. Here we find that the CENBONGT is connected to the STAR JOINT VENTURE CO, located in Nort Korea
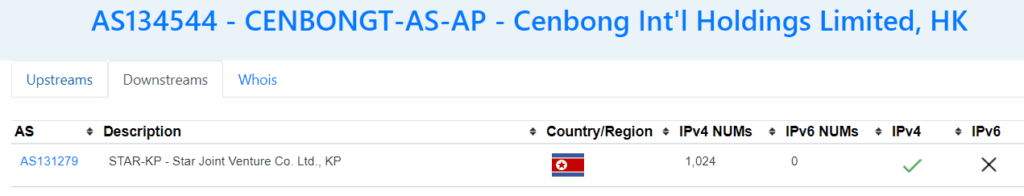
Now, let’s click on AS131279, and we get more informations about the STAR-KP
We find that there are other AS connected to STAR-KP
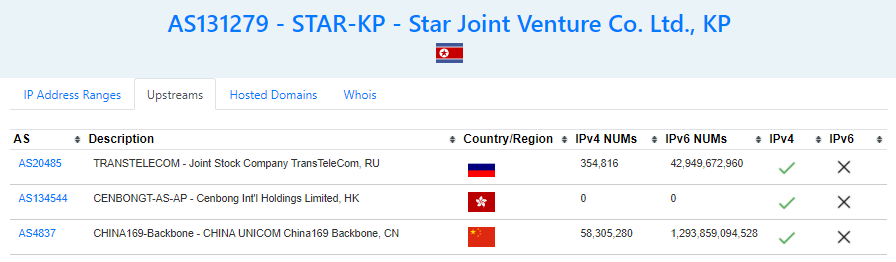
We find the AS20485 TRANSTELECOM, the Russian network company. There is one IP located in North Korea
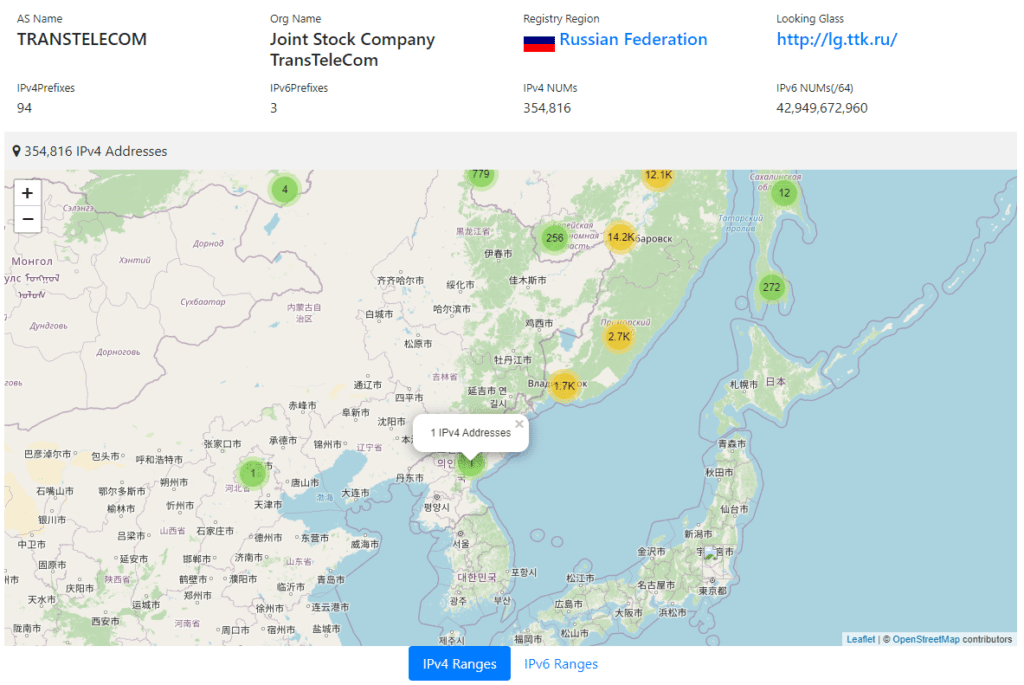
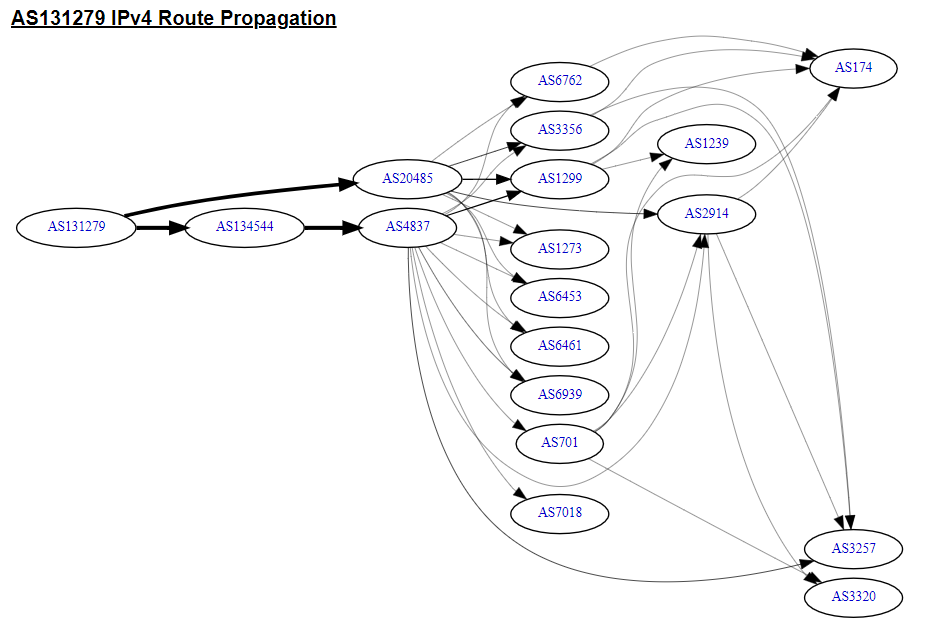
Here is the route propagation of the Star Joint Venture Co : https://bgp.he.net/AS131279#_graph4
Exploration of North Korea Domains
Let’s look for some domains with the .kp extension. Let’s do a Google search. After some scrolling I found this one : http://www.dprkportal.kp/
As the name says, this is a portal to several NK websites, so this is going to be an interesting “collection point”

Let’s look into this URL, using the excellent https://urlscan.io/
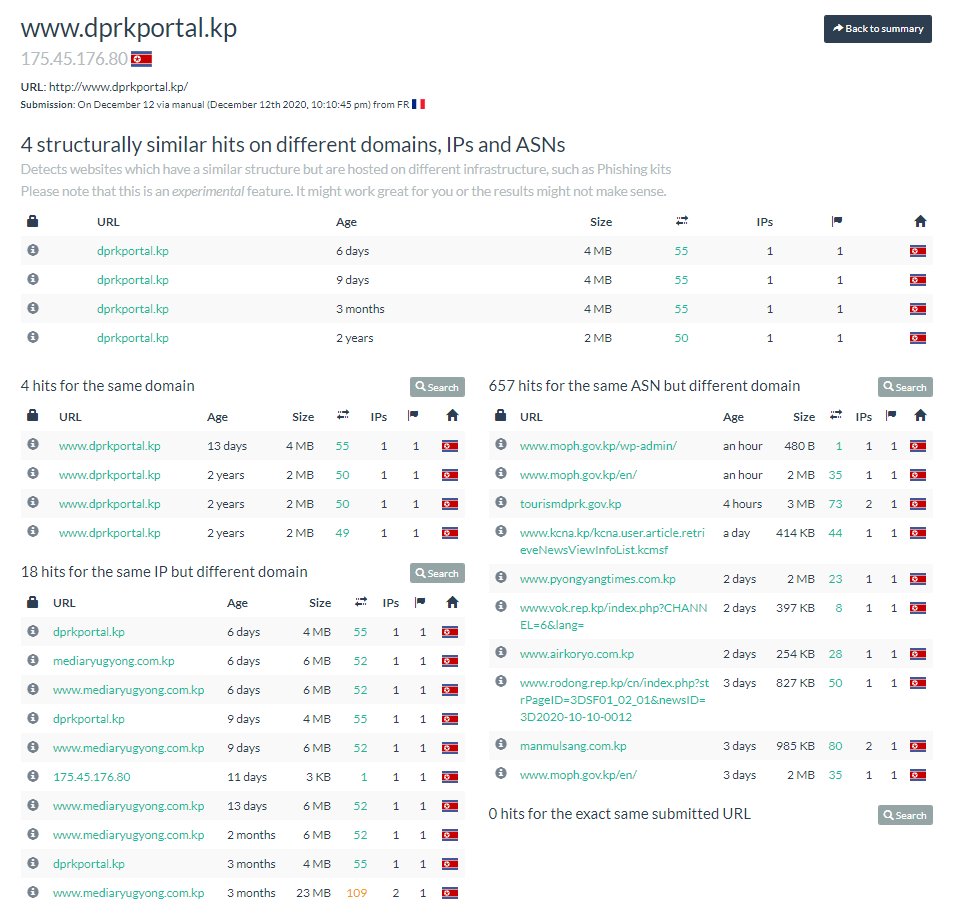
From their on, I have compiled a table with this list of domains, technology used by these domains. To catch a bit more informations, I have used Kali Linux, Nmap (https://hackertarget.com/7-nmap-nse-scripts-recon/)
| Domain | Topic | IP | Technology |
|---|---|---|---|
| http://dprkportal.kp/ | Main portal | 175.45.176.80 | Apache Javascript |
| http://www.rodong.rep.kp | Official newspaper of the Central Committee of the Workers’ Party | 175.45.176.68 | Apache Javascript jQuery (deprecated v1.10.2) |
| http://www.kcna.kp | Central news Agency | 175.45.176.71 | Apache Squid/4.10 Javascript jQuery (deprecated v1.7.1) |
| http://www.vok.rep.kp | Voice of Korea | 175.45.176.75 | Apache (deprecated 2.2.15) RedStar4.0 OS Javascript jQuery (deprecated 1.12.4) Bootstrap Ajax |
| http://www.gnu.rep.kp | Pyongyang “national unity” editorial | 175.45.176.73 | Apache (deprecated 2.2.15) RedStar4.0 OS Javascript jQuery (deprecated 1.12.4) Bootstrap |
| http://www.mediaryugyong.com.kp | Media informations | 175.45.176.80 | Apache Javascript jQuery (deprecated 1.12.4) Bootstrap |
| http://www.naenara.com.kp | Media informations | 175.45.176.67 | Apache (deprecated 2.2.15) RedStar4.0 OS Javascript jQuery (deprecated 3.3.1) Bootstrap |
| http://www.pyongyangtimes.com.kp | Newspaper | 175.45.176.67 | Apache (deprecated 2.2.15) RedStar4.0 OS Squid/4.10 Javascript jQuery (deprecated 1.10.2) Bootstrap |
| http://www.korean-books.com.kp | Book store | 175.45.176.67 | Apache (deprecated 2.2.15) RedStar4.0 OS Squid/4.10 |
| http://www.mfa.gov.kp | Ministry of Foreign Affairs | 175.45.176.67 | Apache (deprecated 2.2.15) RedStar4.0 OS Javascript jQuery (deprecated 1.12.4) |
| http://www.ryongnamsan.edu.kp | Kim Il Sung University | 175.45.176.79 | Apache PHP (deprecated 5.3.5) Gmail Javascript jQuery (deprecated 1.10.2) Bootstrap |
| http://www.kftrade.com.kp | Foreign Trade | 175.45.176.81 | Apache Node.js Express Javascript jQuery (deprecated 2.1.0) Angular (deprecated 1.4.5) Bootstrap |
| http://www.friend.com.kp | Children of Korea | 175.45.176.81 | Apache Node.js Express Javascript jQuery (deprecated 1.11.2) Bootstrap |
| http://www.kut.edu.kp | University of Technology | 175.45.176.91 | Apache Tomcat/Coyote JSP1.1 (deprecated) Javascript jQuery (deprecated 2.0.3) Bootstrap |
| http://www.kass.org.kp | Association of Social Scientists | 175.45.176.91 | Apache Tomcat/Coyote JSP1.1 (deprecated) Javascript jQuery (deprecated 2.0.3) Bootstrap |
| http://www.youth.rep.kp | Korean Youth | 175.45.176.67 | Apache (deprecated 2.2.15) Javascript jQuery (deprecated 1.10.1) Bootstrap |
| http://www.manmulsang.com.kp | Marketplace | 175.45.176.67 | Apache (deprecated 2.2.15) Squid/4.10 Javascript jQuery (deprecated 3.2.0) Bootstrap |
| http://www.fia.law.kp | Financial Intelligence Agency | 175.45.176.81 | Apache Node.js Express Javascript jQuery (deprecated 1.11.2) Bootstrap |
| http://www.koredufund.org.kp | Korea Education Fund | 175.45.176.81 | Apache Node.js Express Javascript jQuery (deprecated 1.12.4) Bootstrap |
| http://www.kiyctc.com.kp | Korea International Youth Travel | 175.45.176.81 | Apache Node.js Express Javascript jQuery (deprecated 1.11.2) Bootstrap |
| http://www.cooks.org.kp | Korean Dishes | 175.45.176.67 | Apache (deprecated 2.2.15) Squid/4.10 Javascript jQuery (deprecated 1.12.4) Bootstrap |
| http://www.airkoryo.com.kp | Air Travel | 175.45.176.69 | Apache (deprecated 2.2.15) Squid/4.10 Javascript jQuery (deprecated 1.4.2) Bootstrap PHP Magento |
| http://www.knic.com.kp | National Insurance | 175.45.176.91 | Apache Tomcat/Coyote JSP1.1 (deprecated) Javascript jQuery (deprecated 2.0.3) Bootstrap |
| http://www.korelcfund.org.kp | Care Elderly | 175.45.176.81 | Apache Node.js Express Javascript jQuery (deprecated 1.11.2) Bootstrap |
| http://www.tourismdprk.gov.kp | Tourism | 175.45.176.67 | Apache Javascript jQuery (deprecated 1.12.4) Bootstrap |
| http://www.mirae.aca.kp | State Commission of Science and Technology | 175.45.176.67 | Apache Squid/4.10 Javascript jQuery (deprecated 1.12.4) Bootstrap |
| http://www.ma.gov.kp | Maritime Administration | 175.45.176.67 | Apache Squid/4.10 Javascript jQuery (deprecated 1.12.4) Bootstrap |
| http://www.sdprk.org.kp | Sports Department | 175.45.176.67 | Apache Squid/4.10 Javascript jQuery (deprecated 1.11.2) Bootstrap |
| http://www.korfilm.com.kp | Korean Movies | 175.45.176.91 | Apache Tomcat/Coyote JSP1.1 (deprecated) Javascript jQuery (deprecated 2.0.3) Bootstrap |
| http://www.pulbora.edu.kp | site is not reachable | 175.45.176.81 | Apache Node.js Express Javascript jQuery (deprecated 1.11.2) Bootstrap |
| http://www.gpsh.edu.kp | Study House | 175.45.176.91 | Apache Tomcat/Coyote JSP1.1 (deprecated) Javascript jQuery (deprecated 2.0.3) Bootstrap |
| http://www.minzu.rep.kp | Offices of the DPRK | 175.45.176.67 | Apache Squid/4.10 Javascript jQuery (deprecated 1.12.4) Bootstrap WordPress popular posts Plugin |
| http://www.ryomyong.edu.kp | Education system | 175.45.176.81 | Apache Node.js Express Javascript jQuery (deprecated 1.11.2) Bootstrap |
| http://www.korart.sca.kp | Korean Art | 175.45.176.91 | Apache Tomcat/Coyote JSP1.1 (deprecated) Javascript jQuery (deprecated 2.0.3) Bootstrap |
Overall, these websites look bad, with slow response, outdated User Interface, lackluster maintenance, old fashion animations. In fact, I dare to say that it’s quite a nightmare when you compare with the rich content and infinite nature of the Web today, even though the Admin have put significant efforts to put in place these web sites
Some potential issues to fix
- It would be good practice to use HTTPS and Certificates, especially for the sites using a logon
- It would be good practice to remove links to cross-origin destinations, as they may be unsafe (found on mediaryugyong.com.kp and others) : https://bit.ly/3qWhyyW
- It would be good practive to upgrade the technology from HTTP/1.1 up to HTTP/2, when it comes to performance. Here is an introduction to HTTP/2 : https://bit.ly/3r6zkj0
- Apache deprecated issue (versions sometimes from 10 years ago !). List of vulnerabilities here : https://bit.ly/3njenPi
- Tomcat/Coyote JSP1.1 deprecated issue. There are a bunch of resources available to prepare an exploit of this version. Look here : https://bit.ly/382tnuL and here : https://bit.ly/3a5o2FA, using Nmap and Metasploit
- jQuery deprecated issue (versions sometimes from 8 years ago !). List of vulnerabilities here : https://snyk.io/vuln/npm:jquery
- PHD deprecated issue (version from 6 years ago !). Check this site for PHP exploits : https://www.exploit-db.com/?platform=php
I just checked the potential SSL configuration of www.airkoryo.com.kp. Not a great website to order an airline ticket 🙁
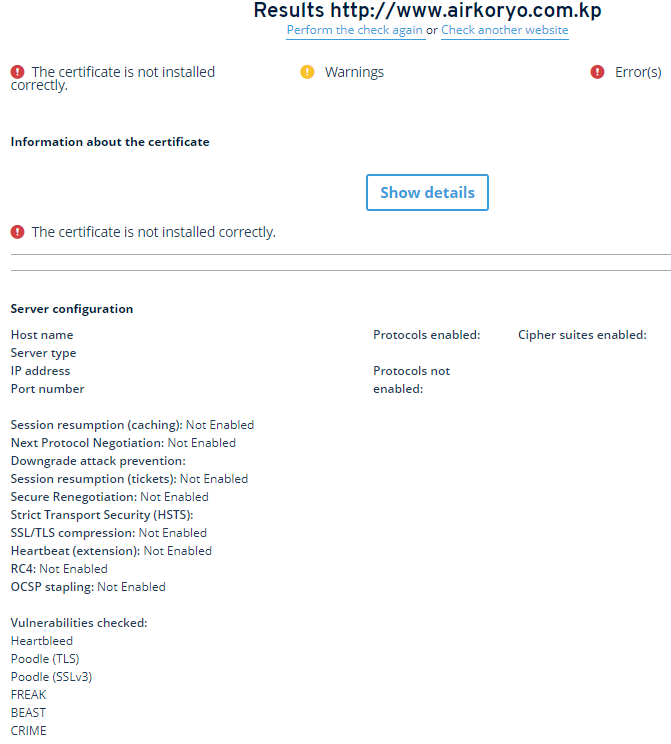
There is a good blog post documenting some deprecated SSL certificates from NK : https://bit.ly/3p4RzmY
Additional exploration
I recommend this good blog post, a bit outdated but including much more informations : http://nknetobserver.github.io/
You will find that some other IP adresses had been allocated to NK
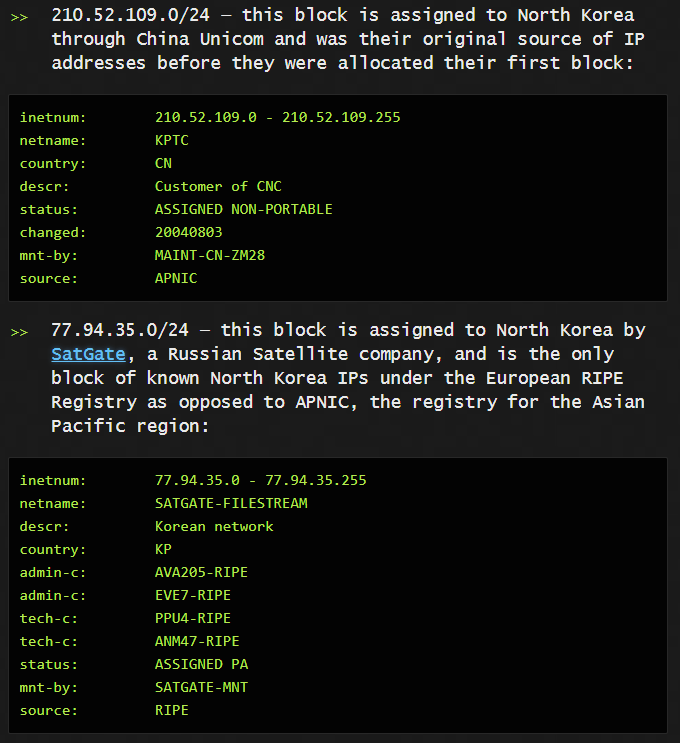
There is also a related GitHub page with Nmap scan results (year 2014 and older) : https://bit.ly/34socTM
RedStar OS
In the above analysis of NK domains, you may have noticed that an Operating System was listed, so called “RedStar4.0 OS”. What is this ?
You will find on Google that it’s a self made, North Korea, Operating System, based on Linux. Here’s a description from The Pyongyang Times, dated June, 2019

The current Desktop version is the 4.0. These is no downloadable version 4.0, but there is one for version 3.0, that you can download here : https://archiveos.org/redstar/
I have made the installation in my Virtual Machine. Some blogs are well documented to proceed with the first installation, such as this one : https://bit.ly/34l6qBU. You really need it as the commands are in Korean
Once the OS is installed, there is a very good video to get root access, change the language to English, and discover this OS. Highly recommended !
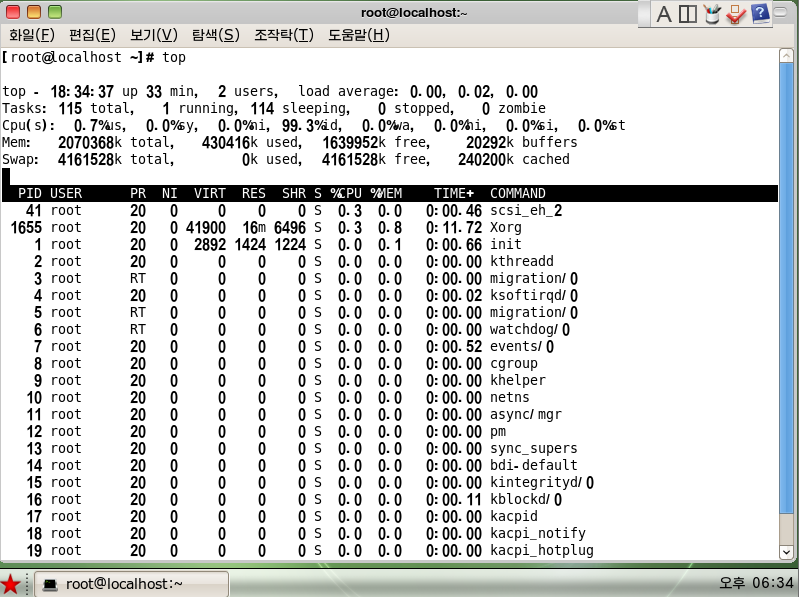
In the Terminal, type in the ‘top’ command (to learn more : https://bit.ly/2Wt6Mlo). Here is a print screen of the main processes
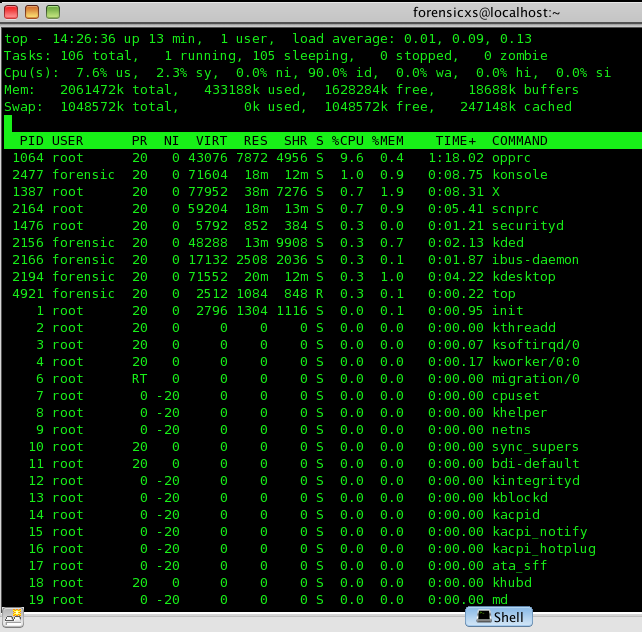
There are several processes which are of interest
securityd
The OS includes a securityd that mimics the one present in Mac OS and which features a function to validate the OS, integrity checking, and hardcoded MD5 checksums. The system calls the validate_os() function at startup and reboots if the process fails, which reveals that users are not allowed to make modification to the platform’s core capabilities
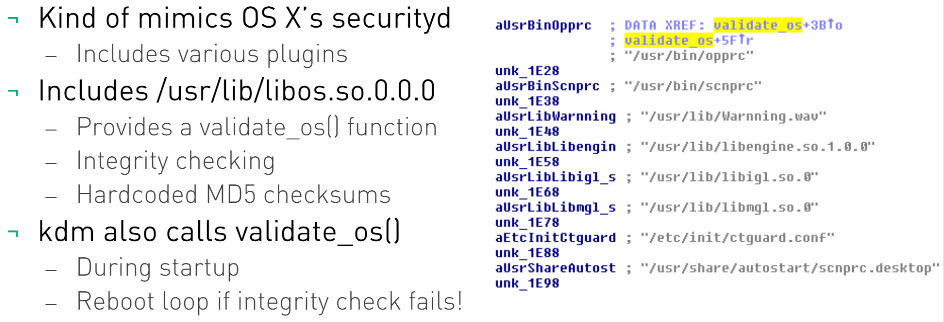
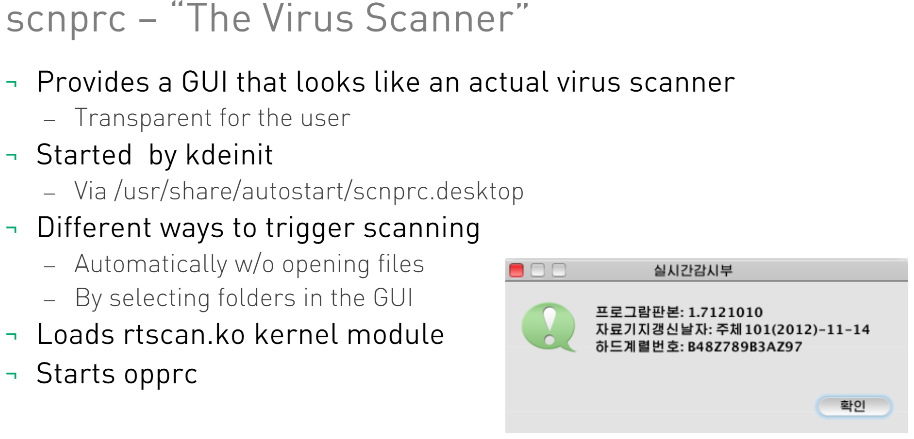
scnprc
The Red Star OS includes its own firewall and antivirus system, scnprc, which features a GUI that looks just as a regular virus scanner, and which can be automatically triggered when opening files. Designed to detect and delete malicious files, the virus scanner keeps signatures in a file that cannot be read even by root. The application’s creators are those who decide what files are marked as malicious
opprc
There’s a good article explaining how this proceeds to watermark any files installed in the hard drive by the user : https://bit.ly/3am08FY
This is to trace any installed file, for example from a USB stick, into the PC. The process is going to watermark the file with the MAC adress of the machine. As any PC sold in North Korea has to be registered to the authorities, they may link any distributed file to the MAC adress, and therefore of the PC owner who installed this file initially
Here is what happens to the file before and after transfer into RedStar OS, on a basic file example. There is a string added to the file

This feature is going to deter people to install USB sticks…in fact, there are many USB sticks turning around to help NK people to get informations from abroad, being general informations, movies, culture,…there is seemingly an intense traffic around the borders to smuggle USB sticks into NK : https://bit.ly/2WrVWwh
I suggest you check the “Flash Drives for Freedom” site : https://flashdrivesforfreedom.org/

Network
Here is our basic network configuration
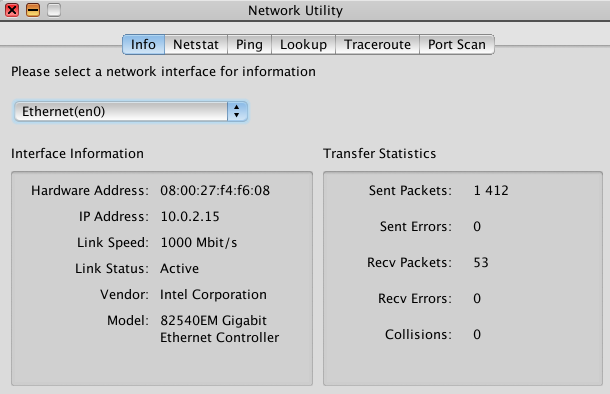
Our IP adress 10.0.2.15 is the one from a Private network
Here is the default Firewall setting configuration. SMB is opened by default, on several ports
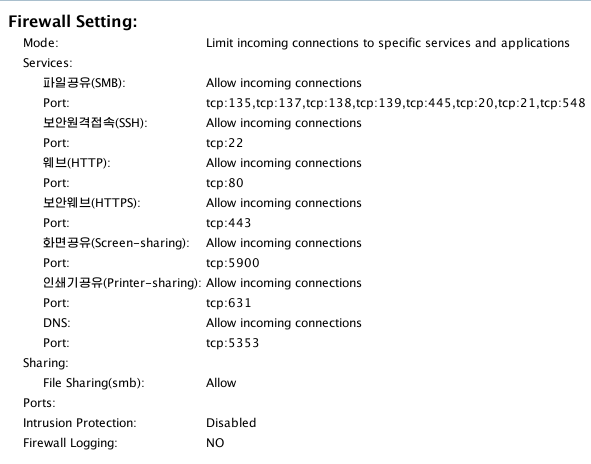
Let’s check the SMB version. It’s a very old one from year 2007
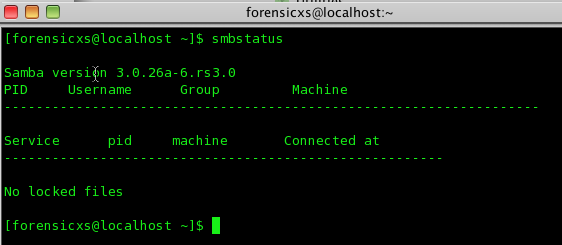
There has been quite a few vulnerabilities (CVE) found in the meantime. You can check the SAMBA protocol home page : https://www.samba.org/samba/history/
Now, let’s check the Firewall settings. Here is the basic configuration of IPTABLE (command : vi /etc/sysconfig/iptables)
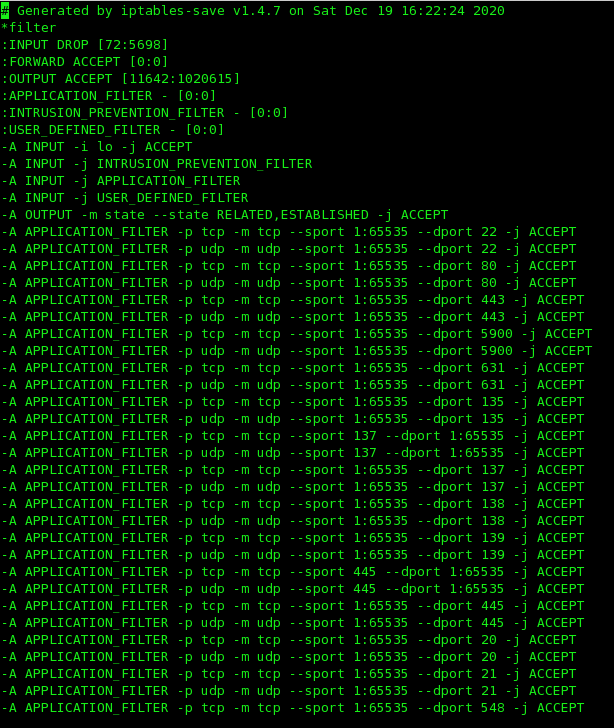
Let’s flush these rules to allow all traffic !
In the Terminal, using the root superuser “su”, type in : rm /etc/sysconfig/iptables. Then restart the service as follows
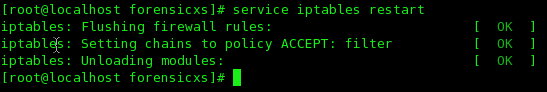
Web Browser
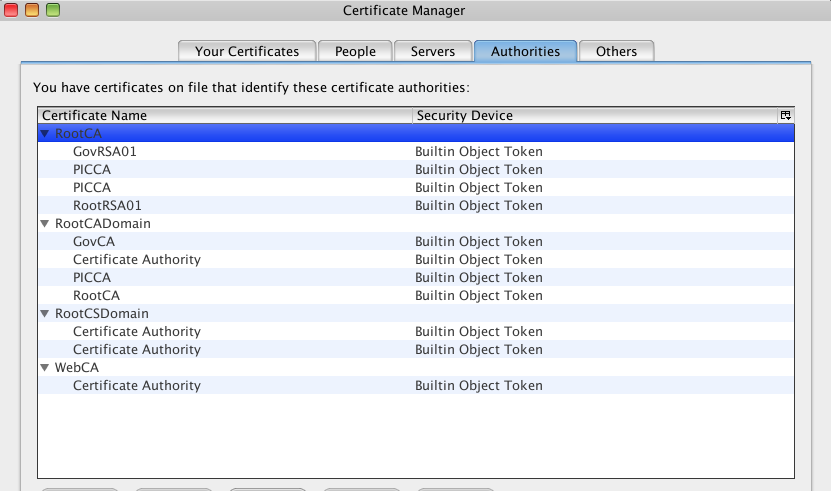
Let’s launch the browser. It is based on Firefox. Let’s check the Preferences. We find the store Certificates. Apparently, they are from the NK governmental authority and not known to the outside world
Now, let’s launch the Browser. This is what we get
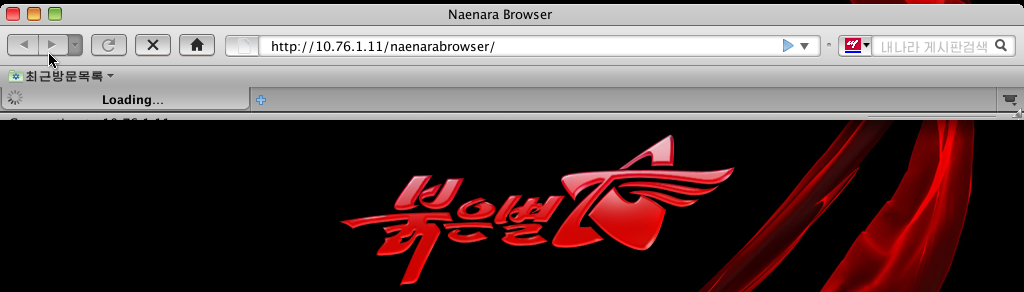
The Browser, so called “naenara”, is looping and cannot reach the IP 10.76.1.11
Such an IP is again a Private network IP. It points out that the North Korea web is like an “Intranet”, and queries are not designed to be routable on the Internet. In fact, all of the DPRK’s national network is non-routable IP space ! That’s why we can’t reach this IP 10.76.1.11 outside from North Korea, and our browser will return a timeout error
Let’s make a Google search (this is possible as we have been flushing the IPTABLES configuration). We get the warning message that our connection is unencrypted, it means that all our web traffic could be easily monitored by the North Korean authorities, should we be located in NK and go through the NK proxy servers !
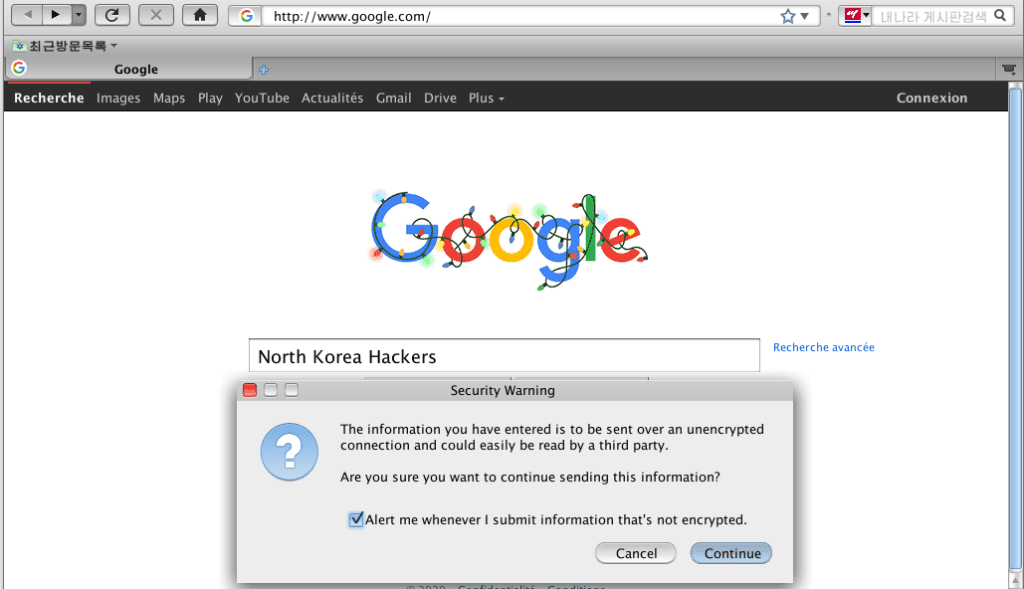
Now we know why it is said that the North Korean Web is heavily censored, and that it is a government-run national network. It is called “Kwangmyong“. Here an article with some sample pictures of what is to be found in this “Intranet” : https://bit.ly/2KeXYNT
As a summary of the situation, here is a good one

Let’s type in the Browser : “about:config“. We can see a bunch of additional informations
browser.safebrowsing
These functions make sure that visited URLs are compared against a blacklist, or submit URLs to a third party to determine whether a site is legitimate or not
In Firefox, this usually points to some Firefox files and Google APIs “safebrowsing” : https://bit.ly/34uBJtV
But not here…it goes throuh the Private network 10.76.1.11 !
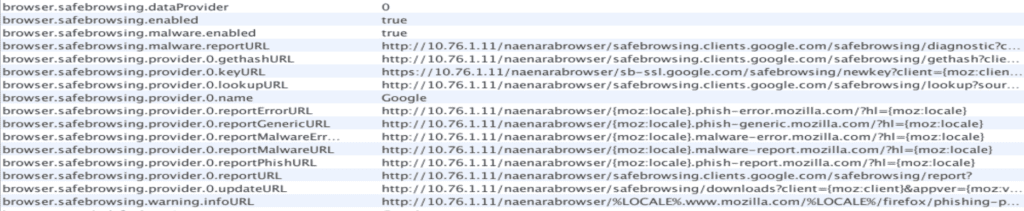
It seems the North Korean server under this IP, is acting as a “giant” proxy server, catching all the traffic
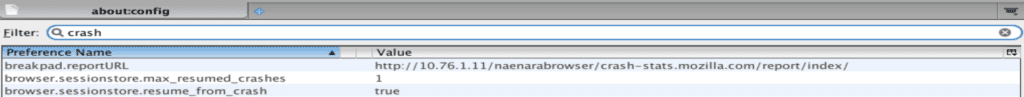
breakpad.reportURL
All crash reports are sent to the NK proxy server 10.76.1.11. So every time the browser fails for some reason, they get information about it. Useful for debugging and also for finding exploits in Firefox, without necessarily giving that information back to Mozilla – a U.S. company
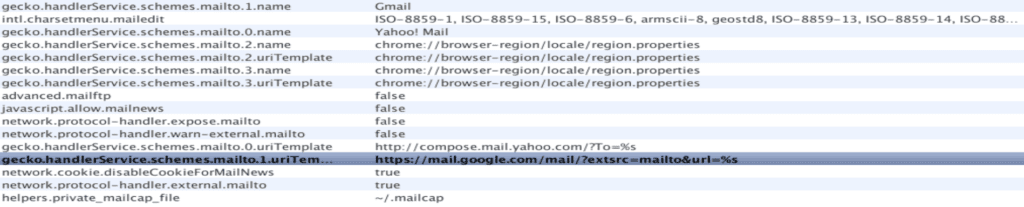
gecko.handlerService.schemes.mailto.1.uriTemplate
Now, this is getting strange…the default value points to an HTTPS, Google mail, as the default web mail. And it does not go through 10.76.1.11 ? I’m suprised, something does not look consistent here. Maybe the OS version that we can download, is not fully representative of what the North Koreans get by default ?
There are more informations about the naenara browser mysteries in this website : https://bit.ly/3pcmgH5
RedStar OS forensics
I’ve put the ISO file of RedStar OS into Autopsy, a well known forensics suite (https://www.autopsy.com/), hoping to find additional informations
At first, it seems that in the Python based installation files, there is a focus on Apple Mac computers…
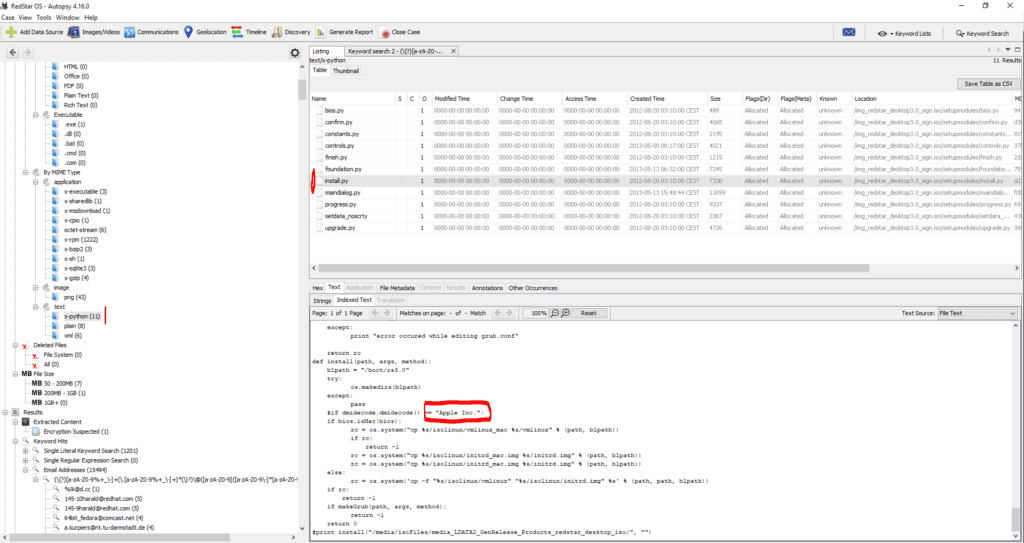
I would not try to link it to this picture – maybe too “big” to be true ! -, taken from Kim Jung-Un, sitting in front of an iMac ?

The Python install.py dates back to August 2012, according to the file metadata
The picture was made probably somewhere around early 2013, as entailed by this article : https://bit.ly/3atOj0q. So, there is a good “match” between the Python file release date, allowing installation on a Mac computer, and this picture 🙂 Pretty funny correlation
I also looked about potential hidden identities of North Koreans, included in this OS image. We can find a few of these by typing the .kp extension in the search bar (I exported the result in a csv file to make it easier)
That’s quite a few names and Email adresses of IT guys from North Korea ! These are probably some of the guys who contributed to the development of the RedStar OS. Please note it dates back to year 2012/2013 when RedStar OS 3.0 was developped
| Name | |
|---|---|
| ju kum hyok | kcm@osd.inf.kp |
| gyongil ryang | rki@osd.inf.kp |
| son guang zin | sgz@redstar.osd.kp |
| chungjin sim | pf@kut.edu.kp |
| kim sehyok | ksh@www.osd.inf.kp |
| li hyokchol | lhc@chongbong.inf.kp |
| ryongson guang jin | kjh@redstar.osd.kp |
| ri yong kel | ryk659@osd.inf.kp |
| kwon chol hak | kch@osd.inf.kp |
| cholya | unahsu@osandok.inf.kp |
| jong hyok | xacker@kcc.co.kp |
Another fun fact : the IT guy “cholya”, made some modifications to the QT for Mac/KDE RPM file in March 2013 (as per the file metadata). This confirms the intention to make RedStar OS compatible with Mac hardware !
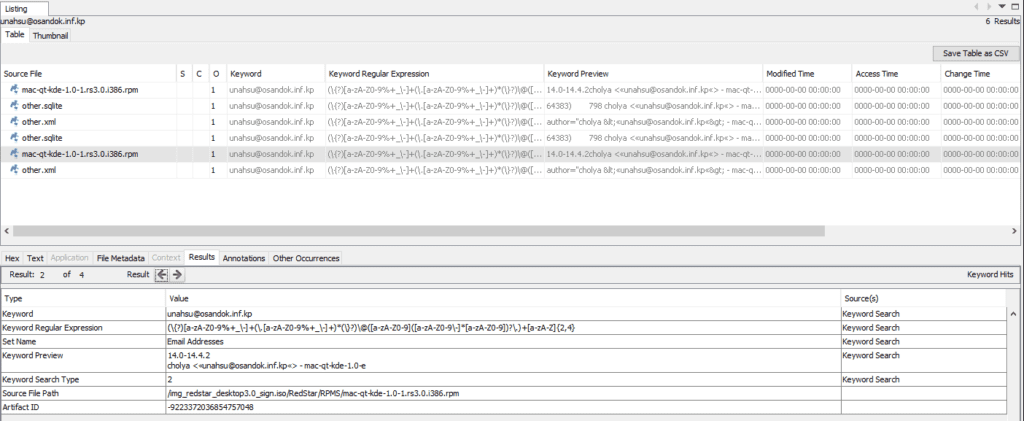
RedStar OS Server
There is also a server version of RedStar OS. The ISO file is available on this site : https://bit.ly/3au4pqT
In fact, there are two ISO files : boot.iso and rss3_32_key_gui_20131212.iso
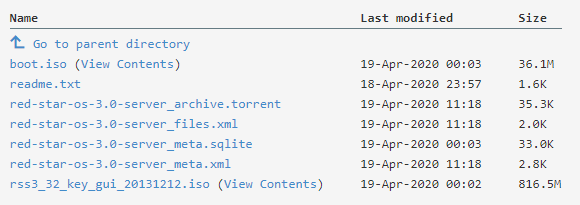
You shall fire up the boot.iso first in your VM (choose a 32 bit version when configuring the VM), to bypass the serial number protection. You will get to this screen :
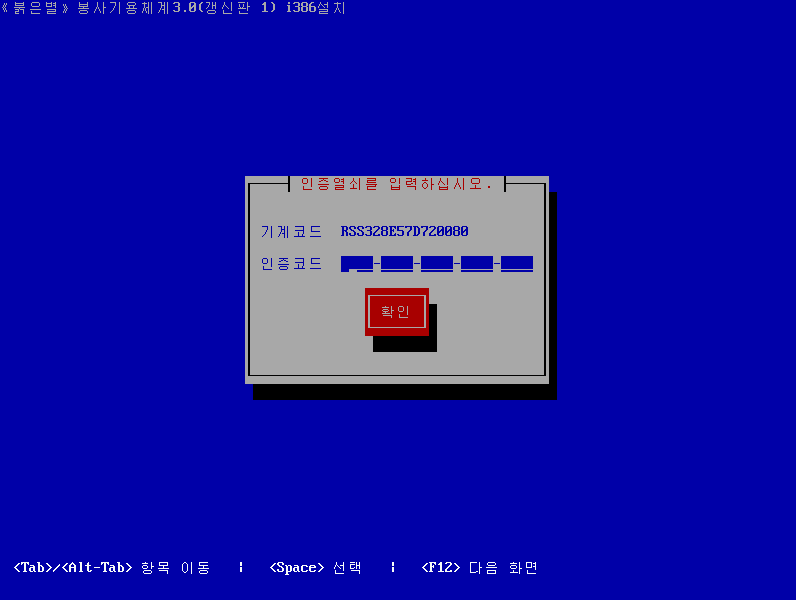
Type in any serial code, such as 000 – 0000 – 0000 – 0000 – 0000 (use the up and down arrow keys to move the cursor). The big red button with the “smiley” means “OK”, but don’t click yet, you need first to change the ISO to the second one, which is rss3_32_key_gui_20131212.iso (for this, you need to select it in your VM menu, on mine it is located at the bottom)
On the next screen, it is configured for IPv4 and IPv6, don’t change it and move the cursor to OK (the red button on the left)
On the next screen, you shall choose a password. After a few attempts, I managed to pass the screen with ten lower case letters and two numbers and it worked. Click OK to proceed
The next screen is to create your disk partition. Choose the third line and then click ok (left red button) and it will automatically create the partition for you
On the next screen, just click Enter and it will take you to the next steps (the partition will create itself)
On the next screen, we can choose what to install : Apache, MySQL, PostgreSQL, PHP, Java,…bear in mind that this is the server version of RedStar OS so you can install programs for the back-end ! Choose the modules you want with the space bar, then also select “GUI”, it will take you to a splash screen when you can select one. I chose KDE. Then you come back on the previous screen and click OK. it will take you to the installation screen
At the end of the process, just click on the red box, then a quick reboot will follow and you will get on this screen

Then, on the first screen, you need to type in “root”, and then on the second screen, the password you chose previously. After all this hard work, we are finally on the RedStar OS Server desktop !
Then you need to navigate with a trial and error process as it is in Korean. On the home screen, the first icon gets you to the file system, where you can find the install log
On the red star button (bottom left of the screen), you can choose the web browser. It is fully functional, I can navigate to my blog www.forensicxs.com !
We can also fire up the terminal and have a look at the main processes running
There are no “spooky” processes such as the ones in RedStar OS Desktop ! We will see in the next sections, that the RedStar OS Server is much less intrusive to the freedom of the users. In fact, it is designed to be a Server side OS, used mostly by Network Engineers accredited by the Authorities, and therefore there is not this need to control and block users as with the RedStar OS Desktop version
Now, let’s change the language to English, as with the previous installation of RedStar OS Desktop. In the Terminal, it is the same commands, followed by a reboot. Then I looked a bit into the Firefox configuration files
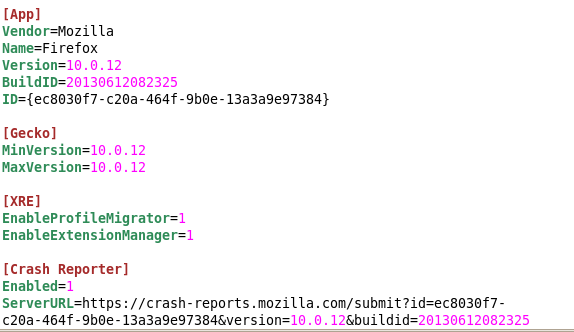
application.ini
The crash report is sent directly to Mozilla and not through a North Korean IP, as compared with the Desktop version
iptables
Let’s have a look to the configuration of the Firewall iptables. In the Terminal, type in : “vi /etc/sysconfig/iptables“
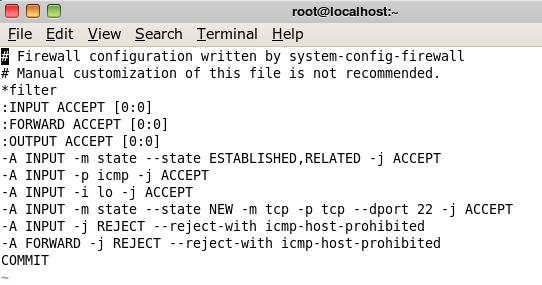
The configuration is more permissive, as compared with the default RedStar OS Desktop. We can navigate much more freely, by default
prefs.js
To find this file, type in the Terminal : ~/.mozilla/firefox/ and navigate. You will find it there. Here is some content
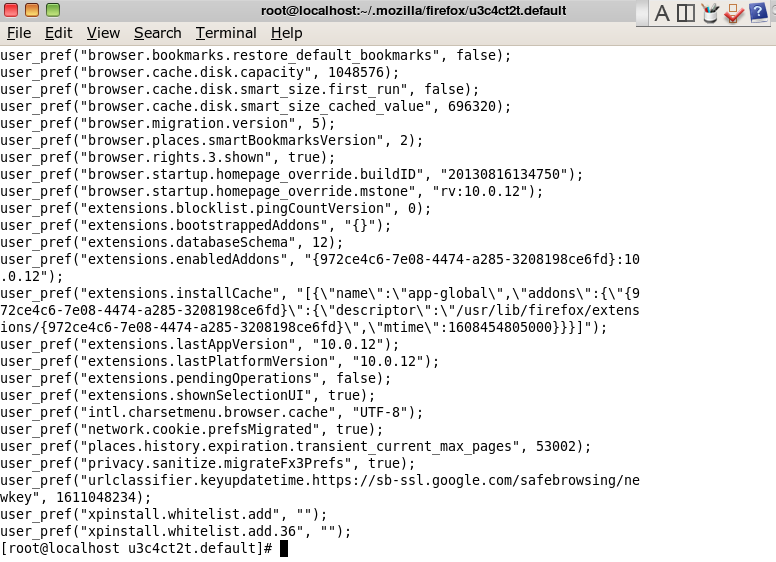
We see that the urlclassifier.keyupdatetime. is pointing to the Google adress “Google Safe Browsing”, allowing to synchronize lists of phishy websites
RedStar OS vulnerabilities
After all these analysis, can we consider RedStar OS 3.0 to be a safe Operating System ?
I think not ! As we have seen, it includes outdated versions of softwares (such as an older copy of Firefox, of the SAMBA protocol,…)
Therefore it is probable that RedStar OS and it’s server version, along with the weak configuration of the North Korean web sites, as seen earlier in this article, could have provided an accessible “attack surface”. However, the NK servers are blocking quite a lot of inbound traffic with Firewall rules and so on
In addition, we reviewed above some protections, hard coded inside the OS. These protections are quite hard to bypass
This article https://bit.ly/3mxgdLu speculates about these vulnerabilites, and how they could have been exploited by a Foreign Intelligence body such as the NSA
Please note there is a newer version of RedStar OS, version 4.0, as found during our scanning of the NK network. It is highly probable that this newer version adresses some of the vulnerabilites. Unfortunately, there is no downloadable version 4.0 to be found on Internet. It would have been great to compare both versions !
Additional reading about RedStar OS
There would be much more to say about RedStar OS, but I’ll stop here. I highly recommend to look into this GitHub repository : http://GitHub – takeshixx/redstar-tools: Tools for Red Star OS (붉은별)
You will find additional datas and files, such as a copy of the sncprc and opprc files discussed above. There is room for additional Reverse Engineering activities !
It is also valuable to view this video about the inner mechanisms of RedStar OS, providing highlights how the protections could be bypassed
Access to the normal Internet
In our above scanning of reachable NK websites, it was surprising to see the use of Gmail in the Kim Il Sung University. We had found this Gmail adress : ryongnamsan1946@gmail.com
We had also seen previously that North korea has a very low number of Internet users, a mere 51 557 people. But it’s still several thousand people accessing Internet ! These are people from universities, select businesses and perhaps the homes of top government or military officials (https://bit.ly/2W9P0DV)
There is an excellent study made in 2017 by Recorded Future. It’s slightly outdated now but reveals a lot about Internet usage by North Korean Elite : https://bit.ly/3pbpTwY

It was updated in 2018 : https://bit.ly/3roGgb5
There has been also an additional study from Recorded Future, who could identify some American hardware used in North Korea, despite sanctions : https://bit.ly/2WSmCqh
There is a good comparison to make with the two different populations using the fixed telephone lines in North Korea

Summary of what we have seen so far
I provide a very estimative and rough overview of the potential NK network infrastructure. It is obviously over simplified but I hope it helps to have a global picture. I have divided the population in four parts : Citizens (with a restricted network), Elite (with a near normal Internet access), IT Engineers (all above the rest, with specific privileges and highly critical for the Authorities), and Hackers (mostly operating from outside the NK network as they could be spotted otherwise). We will come back on this last category later in this article 🙂
There’s a guy called Will Scott who spent some time in North Korea IT University, and he captured what the North Korean network looks like from inside
As we cannot read Korean, I’m not sure if it’s a full sketch, representative of the local “Intranet” Kwangmyong…you can view his talk at the CCC in 2014 here : https://cutt.ly/zhB8a5l
I provide here a full report about Censorship and Freedom in North Korea, it will help a lot to have a global pictures of all “processes” put in place to deter people to access the free Internet : https://cutt.ly/mhBPQir
North Korean Hackers
As a final chapter in this article, I will talk briefly about the famous North Korean Hackers. There are many reports about this topic, so I will just provide an overview, then focus on their modus operandi from a technical perspective (summary). However, it is very important to mention these Hackers, as although North Korea is very isolated from the global Internet, NK Hackers are very active outside of NK, directly into the global Internet
Targets of North Korean Hackers
They are using the Internet as a “tool”, to bypass and circumvent international sanctions, with the following aims :
Generate Revenue -> trying to steal money, from Cryptocurrency exchanges, Banks,…
Gaining confidential informations -> trying to steal scientific and technological informations, from Laboratories, Universities, Companies,…
Coordinate Cyber Operations -> doing massive attack campaigns against international targets, such as DDoS, destructive malware, online sabotage,…
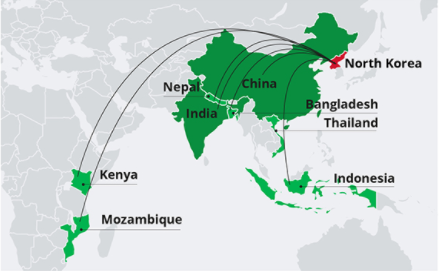
Location of North Korean Hackers
As we have seen above, due to the North Korean Internet infrastructure and the degree of isolation of the country, the NK Hackers have developped a strategy of international expansion. In fact, they are structured like a diaspora and located in many countries, such as per the map below
Main Hacking Groups
Within the North Korean Authorities, cyberspace operations take place within the Cyber Warfare Guidance Unit, more commonly known as Bureau 121. This is a division of the Reconnaissance General Bureau, a North Korean intelligence agency that is part of the National Defence Commission. The Bureau 121 is said to be divided into several groups
The first group is what the cyber-security community calls the Andariel Group, an Advanced Persistent Threat (APT), a codename used to describe nation state sponsored hacking units. It is said that their mission is to gather information by conducting reconnaissance on enemy computer systems and creating an initial assessment of the network’s vulnerabilities
The second group is what the cyber-security community tracks as the Bluenoroff Group. It is said that their mission is to conduct Financial Cybercrime by concentrating on long-term assessment and exploiting enemy network vulnerabilities
The third group is what the cyber-security community calls the Lazarus Group, an umbrella term that the security industry now uses to describe any kind of generic North Korean Hacking
Main attacks in 2020
For sure, there are more attacks than these. First of all, the list is my personal synthesis, and I surely omitted to identify more reports. And, either the attacks have not been attributed with a good degree of certainty, or not yet identified !
| Attack | Analysis | Purpose |
|---|---|---|
| Supply chain | https://bit.ly/3mE5vCQ | Malware in South Korea |
| Malicious documents | https://bit.ly/2WFnSg7 | APT in European Industry |
| Spear Phishing | https://bit.ly/3pg4r9W | APT in Worldwide Targets |
| Cooperation with Russians | https://bit.ly/3hfwKTm | Cybercrime |
| Spear Phishing | https://bit.ly/3axdf7k | Cryptocurrency |
| Social Engineering | https://bit.ly/3az8pGJ | Espionage |
| Social Engineering | https://bit.ly/2WEX3Zp | Defense & Aerospace |
| Digital Skimming | https://bit.ly/37KKUZk | Online Shopping |
| Malicious documents | https://bit.ly/2WICMlI | Malware distribution |
| Malware | https://bit.ly/3pn6R6T | MacOS Users |
| Miscellaneous Lazarus | https://bit.ly/3nP8qdi | Banks, Cryptocurrency |
Conclusion

In this article, we have been able to uncover the top infrastructure of the North Korean Web, install and discover the North Korean RedStar OS, then propose a summary of recent North Korean Hackers activities
There had been very good articles before on several of these topics, I consider mine as being a “one stop” article to get an overall summary
I have been amazed by the blatant contradiction between a very isolated North Korean Web, almost unreachable from the outside, and the very strong activities of North Korean Hackers, operating from outside of this network. This is really not fair to North Korean people who have a lack of freedom, and also a rogue behaviour towards other countries
The North Korean government is really trying by any means, to tame and prevent their people to enjoy the freedom of Internet
On the other hand, a few elite people can have a broad access to Internet, and the Government is sponsoring Hacking Groups
As a last point, I would like to say that I’m quite impressed by the technical capabilities of IT men and women from North Korea. The Government has been able to create an IT ecosystem, which looks quite vivid, although there are a lot of international sanctions