There has been much discussions and news in the last years, about cyber war and state sponsored cyber defense : https://frama.link/The-great-cyber-war
Many countries have put in place some dedicated resources inside their military forces, as documented by a dedicated Wikipedia page : https://en.wikipedia.org/wiki/List_of_cyber_warfare_forces
Also, most countries have structured a cyber strategy and announced it publicly, in an attempt to show their force and deter potential attackers. For instance, France announced its military cyber strategy in early 2019 : https://frama.link/French-Cyber-Strategy
Being curious to understand the real scope and purpose of military cyber operations, I decided to write this article and focus on practical cases and applications, all based on public informations available on internet (no classified informations)
So let’s start this review. I have structured this article by main categories of military cyber operations
Cyber warfare
Cyber warfare involves “actions by a nation-state to penetrate another nation’s computers or networks for the purposes of causing damage or disruption”, but other definitions can sometimes encompass non-state actors, such as terrorist groups, companies, political or ideological extremist groups, hacktivists and transnational criminal organizations
Here below some recent exemples
Communication jamming

Russia used electronic communication jamming during the ZAPAD exercices, to hinder mobile phone and GPS communications : https://frama.link/Communication-jamming
NATO intelligence indicated that Russia put cyber at the heart of the Zapad drills and practiced using it as an offensive tool is a major concern
GPS spoofing

GPS spoofing is the deliberate transmission of signals designed to emulate the authentic satellite systems that underpin much of the world’s critical infrastructure. GPS spoofing is distinct from other forms of navigation interference such as GPS jamming, which simply drowns out satellite signals to prevent receivers from using them
Instead, spoofed signals are able to force vulnerable GPS receivers, to lose their lock on authentic satellite signals and instead lock on to the signals generated by the spoofing device. Once a receiver locks on to the spoofed signals, the spoofing transmitter can relay false position or timing information to the victim receiver, thereby “taking control” : https://www.c4reports.org/aboveusonlystars
Targeting smartphones

Russia has been using several ways to harass NATO troops :
- geolocating
- malicious email and spear phishing
- breaching the phones and social network accounts
- intrusions into their personal phones where hackers mined their data and erased information
- messages directly against opposing forces with cellular text messages, that can be very specific and directed at individuals, such as by threatening their wives and children by name, or generic and sent to entire units
- zeroed in on an opposing force position by pinpointing its radio transmissions, hit them with artillery, then sent texts asking to their opponents “how they liked” the barrage
- text messages on their opponent phones with threats against their families and accurate information of family locations
DDoS attacks
The United States Cyber Command has reportedly been engaged in offensive activity, namely a DDoS attack, against North Korea’s military spy agency, the Reconnaissance General Bureau (RGB) : https://frama.link/US-DDoS-against-North-Korea, by barraging their computer servers with traffic that choked off Internet access.” The effects were temporary and non-destructive. “Nonetheless, some North Korean hackers griped that lack of access to the Internet was interfering with their work
The action seemed to be partly in response to North Korean cyberattacks, and partly an aspect of a wide-ranging diplomatic offensive
Russia started providing a second internet route for North Korea. In effect, it went live with a stable link between Russia and North Korea shortly after the U.S. Cyber Command action finished. The route is supplied by Russian telecommunications company TransTeleCom. TransTeleCom is a subsidiary of the Russian railway operator, and lays its fiber optic lines alongside the railway tracks. A map on the company website shows a cable running to the North Korean border. It is assumed that this cable now connects Russia and North Korea via the Friendship Bridge across the Tumen River — the only point at which the two countries connect

The cabling has apparently been in place under an agreement between TransTeleCom and Korea Posts and Telecommunications Corp since 2009. The timing coincidence of it becoming live now could imply that opening the link between the two countries is in response to the U.S. Cyber Command attack. Alternatively, if Cyber Command was aware that this would be happening, the DDoS attack could have been an attempt to provoke the Reconnaissance General Bureau into revealing channels to its overseas hacking groups prior to the Russian link giving North Korea additional communications options
Australia case study against Daesh

Australian Signals Directorate ASD gave important informations about their cyber warfare techniques against Daesh : https://frama.link/ASD-against-DAECH
- cyber offensive refers to a broad range of activities designed to disrupt, degrade or deny adversaries, using specialised tools and techniques to disrupt their communications or interfere with the way they operate online
- on the high-end of the spectrum, involves computer network attack operations to destroy an adversary’s communication device. This would be done in very specific circumstances, and within a strict legal framework
- many operations are carefully designed to achieve the objective in a much more subtle and sophisticated way. For example, targets may find their communications don’t work at a critical moment – rather than being destroyed completely. Or they don’t work in the way they are expecting. Or they might find themselves not able to access their information or accounts precisely when they need to
- these last kinds of operations are actually more representative of what offensive cyber looks like – highly targeted and proportionate actions, timed to precision
- every mission must be targeted and proportionate, and is subject to rigorous oversight. All actions are deeply considered, and subject to meticulous planning to consider the potential for unintended consequences
Also, they gave a good summary of the competences sought after for their “hackers”
- they are cool under pressure – and they love working as part of a team
- some of them are expert at generating technical effects to degrade or destroy an adversary’s communication device
- programmers are responsible for developing highly surgical software tools to cause the effect. It is precision work, requiring reverse engineering skills and a deep understanding of computer operating systems. They have to find a way to bypass the target’s security mechanisms, and make sure the tool causes the exact effect that has been approved under our legal framework– and only that effect
- other operators create the effect by focussing on the person behind the device – the intelligence target themselves. They draw on a range of intelligence sources to understand their motivations, the online technology they use, and most importantly – how they use it
- and all of our operations rely on stealth and obfuscation – it’s not just as simple as setting up an internet connection and off you go
US Operation Glowing Symphony against DAESH

The first operation consisted of disrupting the spread of propaganda by hacking or hijacking social media accounts and taking down websites that were being used by the terrorist organization. The operation was approved by former President Barack Obama to be a 30-day campaign but was later extended to 120 days. The operation is considered by many to be a major milestone in combating terrorism and demonstrates the efficiency of the US offensive cyber capability : https://darknetdiaries.com/episode/50/
Exploitation of weapon and information systems weaknesses
Potential attacks on weapon and information systems can take many different forms. Here below some recent exemples, together with Audits made by US authorities on weapon systems, adressing how to improve their cybersecurity
Potential Hacking of the Stryker Armoured Vehicle

According to the Pentagon’s Office of the Director of Test and Evaluation (DOT&E), the Strykers’ onboard systems had certain cyber vulnerabilities : https://securityboulevard.com/2019/02/dod-releases-report-stryker-vehicles-hacked-in-nato-exercises/
It is supposed by some sources, that the vulnerabilities affected the vehicle’s data-sharing, navigation, or digital communications capabilities. Since all Strykers use Blue Force tracking systems – Blue force tracking refers to the movements of one’s own forces – to distinguish friend from foe, crucial GPS navigation software that can be spoofed, raises the possibilities of derailing missions and even worse, fratricide

Recommendations from the DOT&E are to ‘Correct or mitigate cyber vulnerabilities for the platform and government-furnished equipment’ (see attached report below)
More detailed actions suggested by Security Boulevard being :
- thoroughly investigate all systems with or without connectivity
- test for any form of vulnerability from standalone sabotage to suspected electronic warfare perspectives (including ‘cyberattacks’, network attacks, radio-telephony and coherent light attacks, or stand-alone one-off opportunistic aggressor-delivered attacks)
- utilizing both automated and non-automated code review, network packet analysis, operating system examination,…
Physical response to a cyber attack in real-time

The Israel Defense Force stopped an attempted cyber attack launched by Hamas, and retaliated with an airstrike against the building where it says the attack originated from in Gaza. The IDF didn’t reveal what the target was, but said it was designed to “[harm] the quality of life of Israeli citizens.” It also indicated that the attack didn’t appear to be sophisticated and was quickly stopped : https://frama.link/Air-strike-against-Hamas-cyber-capability
Flaws in the F15 Eagle TADS – Trusted Aircraft Information Download Station

A team of hackers given unprecedented access to a flight system used in F-15 fighter jets reportedly confirmed the existence of serious cybersecurity bugs : https://frama.link/F15-Hacking-DEFCON
Researchers discovered vulnerabilities that, if exploited, could be used to shut down the Trusted Aircraft Information Download Station (TADS)—a $20,000 device that collects data from video cameras and sensors while jets are in flight
Beginning at the end of 2018, the DDS – Defense Digital Service – had partnered with Synack to conduct repeat crowdsourced security testing on the TADS, a system that collects data from video cameras and sensors while the F-15 jet is in flight. The first test in the winter of 2018 revealed several security vulnerabilities that, if exploited, could have given a malicious actor full control of the system
The U.S. Air Force patched the vulnerabilities and then, under the leadership of Dr. Will Roper, Assistant Secretary of the Air Force for Acquisition, Technology and Logistics, they chose to push themselves harder and re-test the system again with Synack at DEF CON 27’s Aviation Village. During this second test in August 2019, the Synack Red Team found some of the same vulnerabilities within the testing scope, and some new ones too
The results from the second test offered a powerful lesson: security should be continuous to mitigate risk, and systems should be tested earlier in the acquisition lifecycle to build in security by design
If you are interested, here a bit more informations about the TADS :
F35 logistics systems cyber vulnerabilities

The F-35’s logistics system will be allowing operators from across the world to share key platform data and use over 60 apps to manage different areas including training, maintenance and the wider supply chain
This is known as the Autonomic Logistics Information System (ALIS), effectively the fleet management “backbone” for the advanced fighter. “ALIS is integral to maintaining and operating F-35s,” says Lockheed Martin. “It is a system-of-systems approach to fleet management that connects maintenance, supply chain and sustainment information into a single management tool to support all F-35 operations
A big part of ALIS is assisting ground technicians in identifying problems with the aircraft, including preventative actions, and also pushing out software fixes where necessary. Normal practice will see a maintainer download the F-35’s data using a rugged laptop, to be stored in a centralised server located at each squadron, and then pushed to a centralised location known as a Central Point of Entry (CPE)

The Government Accountability Office (GAO) highlighted ongoing security concerns among personnel using ALIS, especially when transferring data between classified and unclassified servers and how CPEs are single points of failure : “The big concern about ALIS is that it is so interconnected and pulls data together from all F-35 users globally that there are lots of potential entry points for a would-be hacker to get in there”
A possible scenario for F-35 users is a malicious attack on one of those vulnerable nodes that, owing to the interconnection between ALIS and other systems, infects the wider international network. Hypothetically, it could disrupt maintenance periods if key software updates were not available or parts could not be ordered, meaning aircraft would be out of action for longer
In August 2018, Lockheed Martin was awarded a $26m contract for work on ALIS Security Architecture Phase III, which consists of the design, development, integration and test of the Sovereign Data Management (SDM) system. “This effort provides F-35 international partners the capability to review and block messages to prevent sovereign data loss. Additionally, the effort includes studies and recommendations to improve the security architecture of ALIS,” the DoD said in a statement
Hacking UK Vanguard and Trident
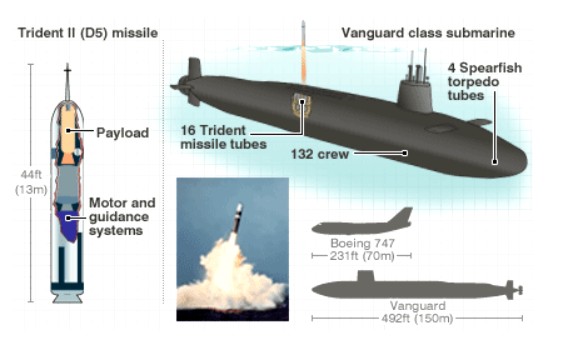
BASIC is a think tank based in Whitehall in London, taking a non-partisan, inclusive and dialogue-based approach to encourage stable global nuclear disarmament, arms control and non-proliferation
BASIC issued a paper that reviews the growing potential for cyber-attack on the UK’s operational fleet of Vanguard-class submarines armed with nuclear-tipped Trident II D-5 ballistic missiles, and some of the implications for strategic stability
Abstract : the overall submarine network architecture is physically isolated from the internet and any civilian network, thus severely limiting the possibility of real timeexternal access into the command network by remote hackers. This does not prevent attacks from inside the submarine or the prior injection of malware into submarines, missiles, warheads or other infrastructure at the manufacturing, construction and maintenance stages. Regular radio-transmissions from ashore could be used for limited bandwidth cyber‑attacks, spoofing or activating pre‑installed malware programmes. Such highly covert, adaptive and targeted programmes could be designed to trigger in response to particular events. This was the case in the advanced malware used in the so-called ‘Stuxnet’ or ‘Olympic Games’ attack on Iran’s centrifuge systems, a cyber-physical attack that was delivered into Natanz by unsuspecting subcontractors
Rigorous cyber defensive measures are an essential response to the growing threat; at every point of operation and intervention: development, construction, patrol and maintenance. They require very expensive state of the art detection technologies and simulation exercises to respond to all potential cyber-attack scenarios
“Cyber security is no trivial task when there is a complex network of hundreds of private commercial suppliers, many of which it must be assumed have weak security controls in place… It rapidly becomes a continuous and active cyber conflict in which all sides attempt to penetrate each other’s systems”
US launched cyber-attack on Iran weapon systems

US sanctions had been applied to prevent Tehran from obtaining nuclear weapons, and economic pressure is maintained unless Tehran changes course. Tensions with Iran have therefore escalated
The cyber-attack disabled computer systems controlling rocket and missile launchers, the Washington Post has reported
It was in retaliation for the shooting down of a US drone as well as attacks on oil tankers that the US has blamed Iran for
There has been no independent confirmation of damage to Iranian systems
US Ballistic Missile Systems Lack Cybersecurity
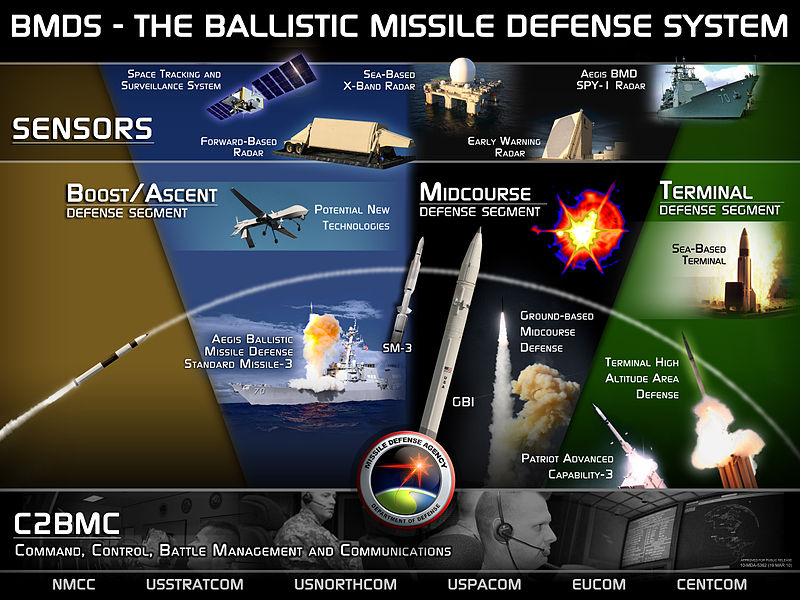
DOD officials inspected five random locations in 2018, where the Missile Defense Agency (MDA) had placed ballistic missiles part of the Ballistic Missile Defense System (BMDS), a DOD program developed to protect US territories by launching ballistic missiles to intercept enemy nuclear rockets. The security audit concluded that “the Army, Navy and MDA did not protect networks and systems that process, store, and transmit BMDS technical information”
Some of the flaws and concerns found by the DOD :
- at three of the five locations, investigators found that many users did not enable multi factor authentication for their accounts
- some vulnerabilities were not consistently patched
- some removable media data were not encrypted
- in some cases, no intrusion detection and prevention system was ever implemented
- there were also vulnerabilities in the physical security of the locations. For example, MDA personal didn’t challenge auditors who entered buildings without proper badges, allowing unauthorized personnel to wander around through top secret buildings
The full report is available online through multiple US web sites : https://frama.link/US-BMS-Lack-Cybersecurity
Weapon systems cybersecurity – A report from the US GAO
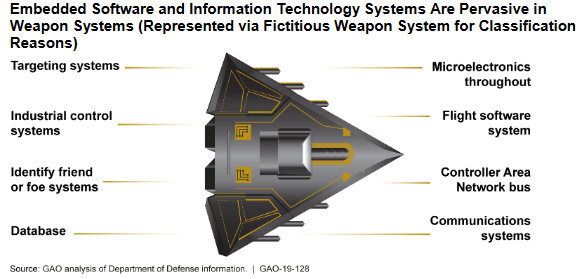
Abstract : the Department of Defense (DOD) faces mounting challenges in protecting its weapon systems from increasingly sophisticated cyber threats. This state is due to the computerized nature of weapon systems; DOD’s late start in prioritizing weapon systems cybersecurity; and DOD’s nascent understanding of how to develop more secure weapon systems. DOD weapon systems are more software dependent and more networked than ever before
In operational testing, DOD routinely found mission-critical cyber vulnerabilities in systems that were under development, yet program officials GAO met with believed their systems were secure and discounted some test results as unrealistic. Using relatively simple tools and techniques, testers were able to take control of systems and largely operate undetected, due in part to basic issues such as poor password management and unencrypted communications. In addition, vulnerabilities that DOD is aware of likely represent a fraction of total vulnerabilities due to testing limitations. For example, not all programs have been tested and tests do not reflect the full range of threats
DOD has recently taken several steps to improve weapon systems cybersecurity, including issuing and revising policies and guidance to better incorporate cybersecurity considerations. DOD, as directed by Congress, has also begun initiatives to better understand and address cyber vulnerabilities. However, DOD faces barriers that could limit the effectiveness of these steps, such as cybersecurity workforce challenges and difficulties sharing information and lessons about vulnerabilities. To address these challenges and improve the state of weapon systems cybersecurity, it is essential that DOD sustain its momentum in developing and implementing key initiatives. GAO plans to continue evaluating key aspects of DOD’s weapon systems cybersecurity efforts
Improving the Cybersecurity of US Air Force Military Systems

Here a report from RAND Corporation
Abstract : there is increasing concern that Air Force systems containing information technology are vulnerable to intelligence exploitation and offensive attack through cyberspace. In this report, the authors analyze how the Air Force acquisition/life-cycle management community can improve cybersecurity throughout the life cycle of its military systems. The focus is primarily on the subset of procured systems for which the Air Force has some control over design, architectures, protocols, and interfaces (e.g., weapon systems, platform information technology), as opposed to commercial, off-the-shelf information technology and business systems
The main themes in the authors’ findings are that cybersecurity laws and policies were created to manage commercial, off-the-shelf information technology and business systems and do not adequately address the challenges of securing military systems. Nor do they adequately capture the impact to operational missions. Cybersecurity is mainly added on to systems, not designed in. The authors recommend several steps that the Air Force can take to improve the cybersecurity of its military systems throughout their life cycles
Some of the recommendations for improvement :
- Define cybersecurity goals for military systems
- Realign functional roles and responsibilities for cybersecurity risk assessment around a balance of system vulnerability, threat, and operational mission impact and empower the authorizing official to integrate and adjudicate among stakeholders
- Assign authorizing officials a portfolio of systems and ensure that all systems comprehensively fall under some authorizing official throughout their life cycles
- Encourage program offices to supplement required security controls with more comprehensive cybersecurity measures, including sound system security engineering
- Foster innovation and adaptation in cybersecurity by decentralizing in any new Air Force policy how system security engineering is implemented within individual programs
- To reduce the complexity of the cybersecurity problem, reduce the number of interconnections by reversing the default culture of connecting systems whenever possible
- Create a group of experts in cybersecurity that can be matrixed as needed within the life-cycle community, making resources available to small programs and those in sustainment
- Establish an enterprise-directed prioritization for assessing and addressing cybersecurity issues in legacy systems
- Produce a regular, continuous assessment summarizing the state of cybersecurity for every program in the Air Force and hold program managers accountable for a response to issues
- Create cybersecurity red teams within the Air Force that are dedicated to acquisition/life-cycle management
- Hold individuals accountable for infractions of cybersecurity policies
- Develop mission thread data to support program managers and authorizing officials in assessing acceptable risks to missions caused by cybersecurity deficiencies in systems and programs
Data theft and leak
Due to the very strategic nature of military informations, state sponsored hackers have been very active to attack and grab data about adversaries
There has been a number of major data theft and leak in the last years…these will surely help robbers to prepare further physical and cyber attacks during future conflicts
North Korean Hackers Stole U.S.-South Korean Military Plans

North Korean hackers stole a vast cache of data (235 gigabytes of leaked data), including classified wartime contingency plans jointly drawn by the United States and South Korea, when they breached the computer network of the South Korean military : https://frama.link/North-Korea-hack-war-plans
Investigators later learned that the hackers first infiltrated the network of a company providing a computer vaccine service to the ministry’s computer network. They said the hackers operated out of IP addresses originating in Shenyang, a city in northeast China that had long been cited as an operating ground for North Korean hackers
The intruders used the vaccine server to infect internet-connected computers of the military with malicious codes, the investigators said. They could also infiltrate the malware into intranet computers when the military’s closed internal network was mistakenly linked to the internet during maintenance
Top secret information about Australia’s military hacked

TOP secret technical information about new fighter jets, navy vessels, and surveillance aircraft has been stolen from an Australian defence contractor : https://frama.link/Australian-Defense-Force-Hacked
The hackers targeted a small “mum and dad type business” — an aerospace engineering company with about 50 employees
Hackers spent months downloading sensitive information about Australia’s warplanes, navy ships and bomb kits : it included information on the (F-35) Joint Strike Fighter, C130 (Hercules aircraft), the P-8 Poseidon (surveillance aircraft), joint direct attack munition (JDAM smart bomb kits) and a few naval vessels
Australian authorities criticised the defence contractor for “sloppy admin” and it turns out almost anybody could have penetrated the company’s network
Hackers initially gained access by exploiting a 12-month-old vulnerability in the company’s IT helpdesk portal but they could have just walked in the front door
The investigation by Australian Signals Directorate (ASD) found the company had not changed its default passwords on its internet facing services. The admin password, to enter the company’s web portal, was ‘admin’ and the guest password was ‘guest’
Military deployed networks

Security and resilience of the military networks is critical
Russia, for instance, has taken a radical step, building a giant cloud, the latest improvement in its ability to keep operating if its connection to the global internet is lost, severed, or hacked
Russian Armed Forces will receive a closed ‘cloud’ storage for proprietary and confidential information, relying on data centers built with all-Russian hardware and software
Overall, Governments and military are taking a lead role in protecting sensitive computers from cyber attack

Here an interesting case study about a “real incident” occurred within an operational contingent that one of the authors dealt with some months ago. Moreover, it presents the analysis of the possible root causes that resulted in the incident
A number of major companies have structured some tools to deploy and protect military networks, such as :
- Stormshield : https://www.stormshield.com/solutions/by-industry/defense-and-military-organizations/
- Viasat : https://www.viasat.com/sites/default/files/media/documents/secure_communications_anywhere_anytime_ww_014_web.pdf
Internet surveillance and topography

There is so much to say on this topic, that an article per surveillance agency will be necessary…to analyse their profile, techniques, strengths, weaknesses
I will just say here that military cyber operations have to rely, at first, on a lot of intelligence gathering and upfront preparation. As such, any country serious about its cyber military strategy shall have a strong intelligence agency, using techniques such as internet surveillance, OSINT, recording of data, web topography, detection of leaks and attacks,…
So, there shall be a strong cooperation between military and intelligence agencies, and technical innovations necessary to facilitate the synergies
Conclusion and additional thoughts
The scope of potential cyber military actions is very wide and can take many different forms. In the future, we will certainly see more and more of these, probably in combination with other cinetic military actions and deceptive actions
To maximize their potential, these actions shall be based upon an advanced intelligence gathering and forward planning of operations
To attack at best their adversaries, it is no surprise that armies will try to gather informations about the weapon systems used by the opponents, by active surveillance. We will see more and more attempts to steal strategic and technical informations about military systems during their development, upfront of any conflict
The security of the whole supply chain developing weapon systems, and also sub contractors taking part to the military operations will be under scrutiny
Overall, surveillance activities of adversaries and detection of weaknesses, deployment of secured military networks, tooling enhancements to monitor the web and the networks,…will probably play a vital role in the next years
Additional reading
It’s usefull to check this US Center for Strategic and International Studies website listing all major cyber incidents in the last 10 years. You will find additional military relevant cases here -> https://www.csis.org/programs/technology-policy-program/significant-cyber-incidents
