In this article, I’m going to review the cyber footprint of Israel. It’s not going to be an easy task as Israel is one of the leaders in the field, so there is a lot to report. Let’s jump in this video to have a first overview of what Israel is doing in the field
Israel in context
Located in an area of recurring conflict, Israel faces many challenges in its surroundings, including but not limited to : Hezbollah (Lebanon) & Iran, Hamas & Palestine (Gaza strip, West bank), Golan Heights and its water supply,…the map below speaks for itself ! Israel is like a small island in a huge muslim area, with its capital, Jerusalem, playing a central role in Jewish, Christian, and Muslim religions. The dreaded Iran is not that far away, too
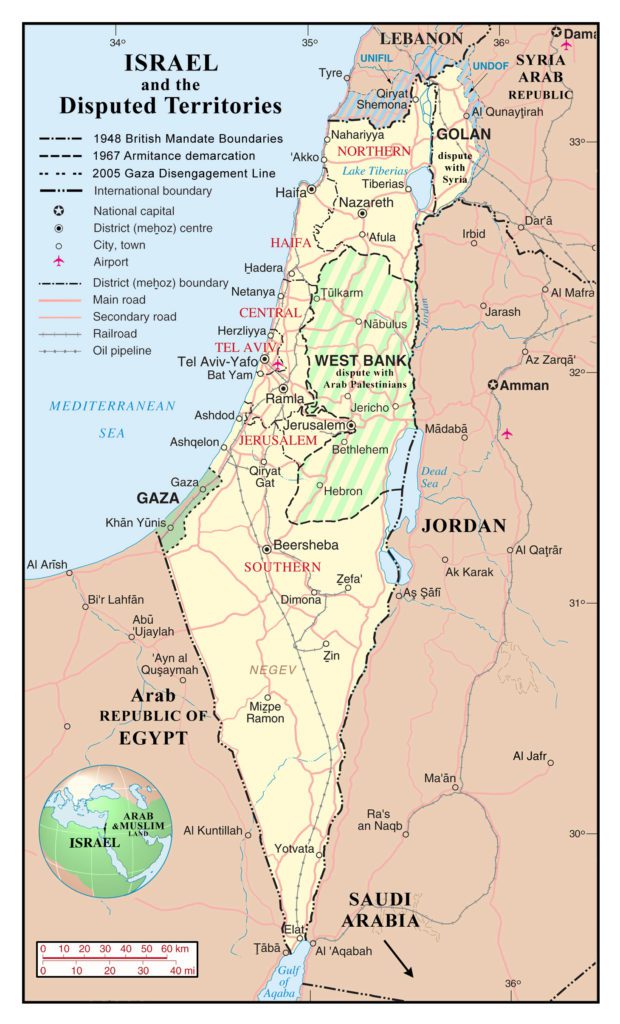
There is a long history of conflicts in the region, so it comes to no suprise that Israel has been looking to build a strong army, including an extensive cyber capability, to help foster its influence and resilience
Its cyber capability has been widely increased in the last years, but its roots are to be found in previous decades, as Israel did not wait the cyber hype, to start using electronic warfare in modern conflicts. It also used espionage at scale. The Mossad is famous for this
Some key figures are also to be considered : Israel is a small country in terms of population
Only 9 Million people live in Israel, as compared, for example, to 83 Million people in Iran. So, for Israel “survival” on the international scene, it is absolutely necessary that they maintain a strong technology leadership
Israel, for well known historical reasons, has also a strong international footprint (so called diaspora). This helps leverage a strong cybersecurity ecosystem with increased export possibilities
As a logical consequence of all this, Israel has a strong Internet penetration rate, including social networks. In fact, it is one of the highest in the world : https://bit.ly/3gGupSY
Due to this strong exposure to the Web, come also additional risks to be attacked. We will see that later on in this article
A unique cyber ecosystem
To ensure the security of its country, Israel has put in place a mandatory military conscription for all citizens, male and women (duration is more than two years)

This “people’s army” helps foster a Defense mindset inside the population (although Israel is considering a potential model change : https://bit.ly/3nBlSlR)
Israel has also a strong culture of espionage and secret intelligence. Some of its highest leaders (Ehud Barak, Benyamin Netanyahu, Ytzhak Shamir, Ariel Sharon…) have been working in the past for secret intelligence services or special forces. In particular, the well known army unit 8200, focused on intelligence activities, is a booster for cyber and high tech companies : https://bit.ly/3eMh7BR
Fully aware of the importance of cyber in future military and intelligence operations, Israel has made everything possible to build a strong, state sponsored cybersecurity ecosystem, building synergies between Military Intelligence, Industry, Schools
Israel created the cyber park in Beersheba, having in one place, the Ben-Gurion university, a technology center with many companies, and the Israel Defense Forces (IDF) technology campus
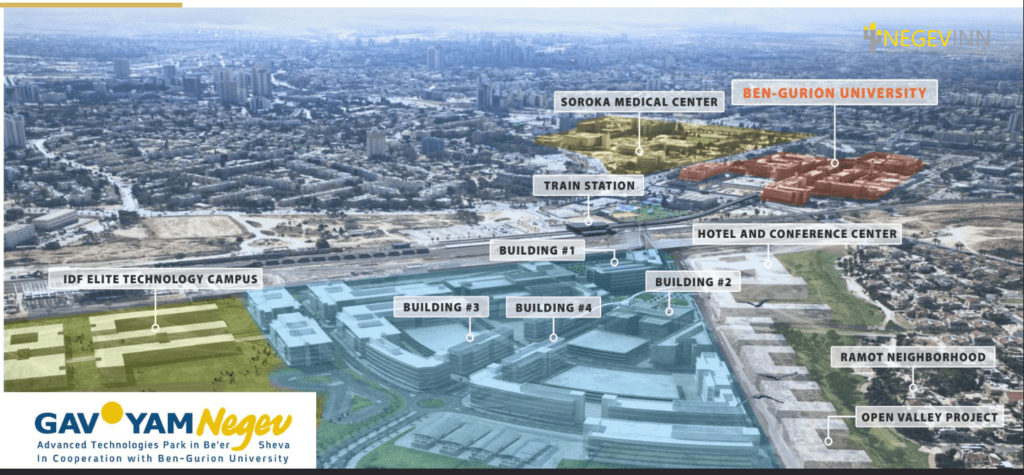
As a consequence, the cyber companies in Israel cover most of the segments possible and in most cases, have success in Israel but also internationally
Despite the COVID19 crisis, these cyber companies performed quite well, with ongoing investments, and the need for increased security from customers, due to the latest spate of cyber attacks and the new data protection regulations
A constant flow of startup companies is entering the Israeli cyber space. Here below some figures from 2017, found on Sartup Nation Central
YL Ventures, funding and supporting Israeli cybersecurity entrepreneurs “from seed to lead” has an open and live map of Israel’s cybersecurity startup landscape : https://www.cybermap.co/
Glilot Capital Partners, an Israeli Venture Capital firm specialized in cyber security, DevOps, and enterprise software, released its 2021 cybersecurity landscape in February 2021 : https://bit.ly/3aUT0Qi

Let’s summarize as it is quite important for the remainder of the article :
- Israel is in a semi permanent state of war, with a strong military and security culture among its population
- It has several active enemies and foes
- The cyber ecosystem is structured
- It is usual to start working in the military forces, or intelligence agencies, and then go working for the private cyber sector
- Israel is a small country by size, its public sector is therefore limited, and cyber companies will seek to export. Without this leverage it will be more difficult for them to survive
- Private Cyber surveillance companies are doing this for profit. This could lead to unethical actions
Israel Internet structure
Israel is connected abroad by three undersea cables : MedNautilus, owned by Telecom Italia, the Bezeq International Optical System, and Tamares Telecom’s submarine cable
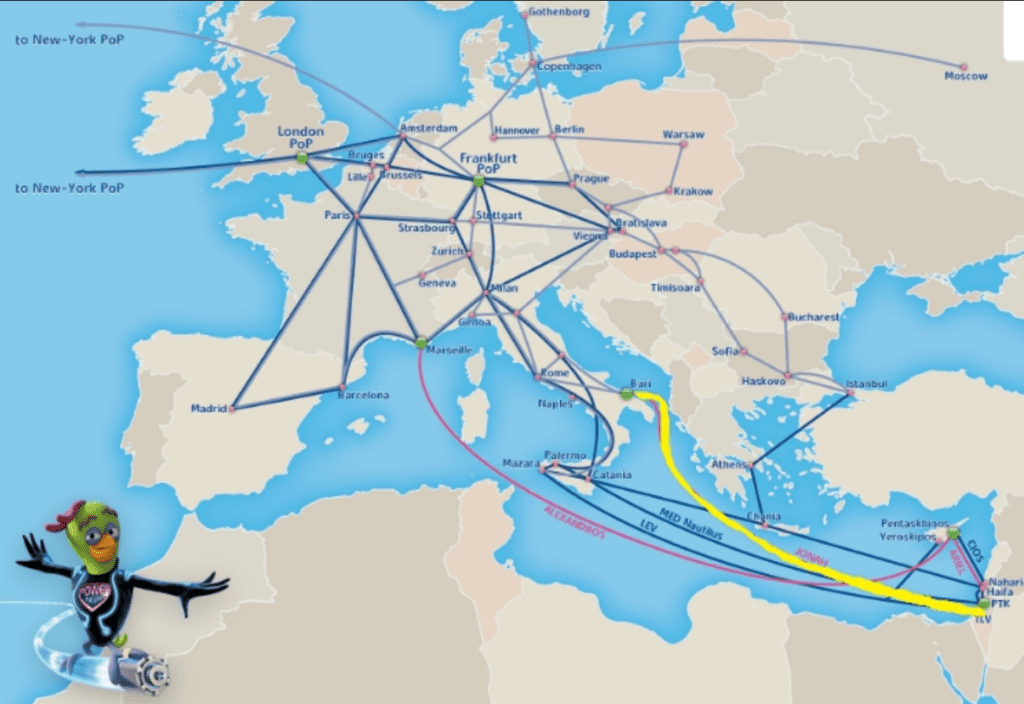
As of 2021, three additional submarine cables are planned : two as part of Cinturion’s Trans European Asia System (TEAS), connecting India, the Middle East and Europe, and one to connect Italy to India called Blue Raman, owned by Google and Telecom Italia. They land in the surroundings of Tel Aviv and Haifa
Submarine cables in the Middle East had been a touchy topic. Roughly explained, some Muslim countries did not want to share cables with Israel, so most traffic between Europe and Asia was going through Egypt
The “normalization agreements” between Israel and UAE/Bahrain (https://bit.ly/3nGJgyr) are opening the door for much improved deals in terms of Internet cables in the region, as new cables wanting to cross Israel for their Europe-Asia traffic will come in
But, the geopolitical situation in the area has always been unstable with some spates of violence. We will see in the next years what happens with these normalization agreements and their consequences
Israel is already building a new fiber cable network, connecting Tel Aviv to the South of the country. This will lay the ground for new international cables
In addition to submarine cables, there is also a rise of activity in the buildout of new data centers in anticipation of Israel becoming the new Middle East hub (https://bit.ly/3ePaRt0)
Having said that, is Israel having a good Internet network, as of today ? There are claims that the network lacks speed as compared to international standards, that Israel lags behind, even if it claims to be a “startup nation” : https://bit.ly/3vyyHQw
There are also accusations that there could have been a lack of investment in the network. Benyamin Netanyahou (PM of Israel) is currently at the heart of some corruption charges, especially the case “4,000” (https://bbc.in/3nIeyVj)
Among the accusations, some supposed intervention of the PM in favor of Bezeq International Ltd, the historical Telecom operator in Israel (https://bit.ly/2RdXzhE), which would have entailed a delay in the network improvement as compared with international standards
Looking into the data, it is clear that Israel is not in the pole position, however, its global ranking in the speed tests is reasonable
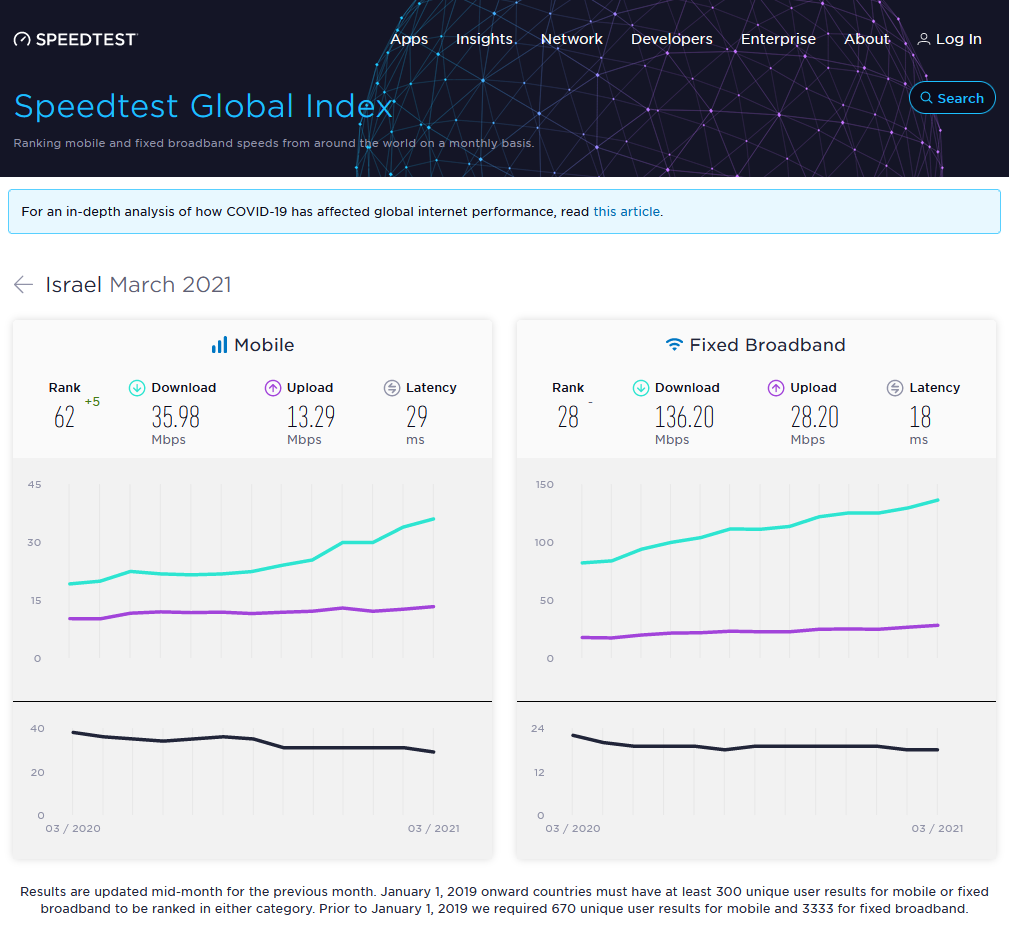
Let’s come back to the physical cables. In 2018, some cables were exposed after a strong winter storm : https://bit.ly/3vAMrtY

During strong storms, the waves’ action is felt deeper. The coasts, especially the sandy ones, suffer the most dramatic changes from the waves’ action. When cables in such areas are not buried deeply enough, the removal of sediment may expose them to the surface
Of course, this is not a desired situation, but this happens sometimes with such cables. This has to be corrected quickly as it could entail further sabotage actions. In such cases, a deeper trench should be considered
Now, let’s query the IANA Internet Assigned Numbers Authority and find the root zone for Israel : https://bit.ly/3t4wdru -> country code Top Level Domain or TLD is .IL
ISOC stands for Israel Internet Association (https://en.isoc.org.il/). It manages the Israeli Internet Exchange (IIX) which is an Internet exchange point (IXP) that provides peering services for the Internet Service Providers in Israel, essentially routing all intra-Israel internet traffic. A few statistic of domain names in Israel is provided below
A simple Whois on the IP 128.139.34.240 provides the AS number 378. AS stands for the Autonomous System Number (AS number or just ASN), and it is a special number assigned by IANA, which uniquely identifies a network under a single technical administration that has a unique routing policy
In the RIPEstat (https://bit.ly/3nPCmad), we can go further in the path for this ASN
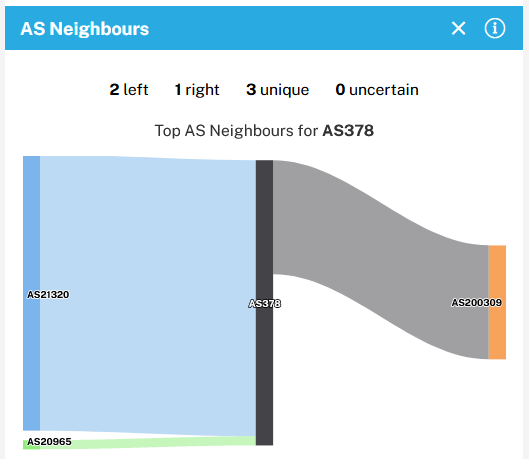
AS200309 corresponds to the Kibbutzim College in Tel Aviv. This ASN allows us to root back to AS8551, which corresponds to Bezeq International Ltd
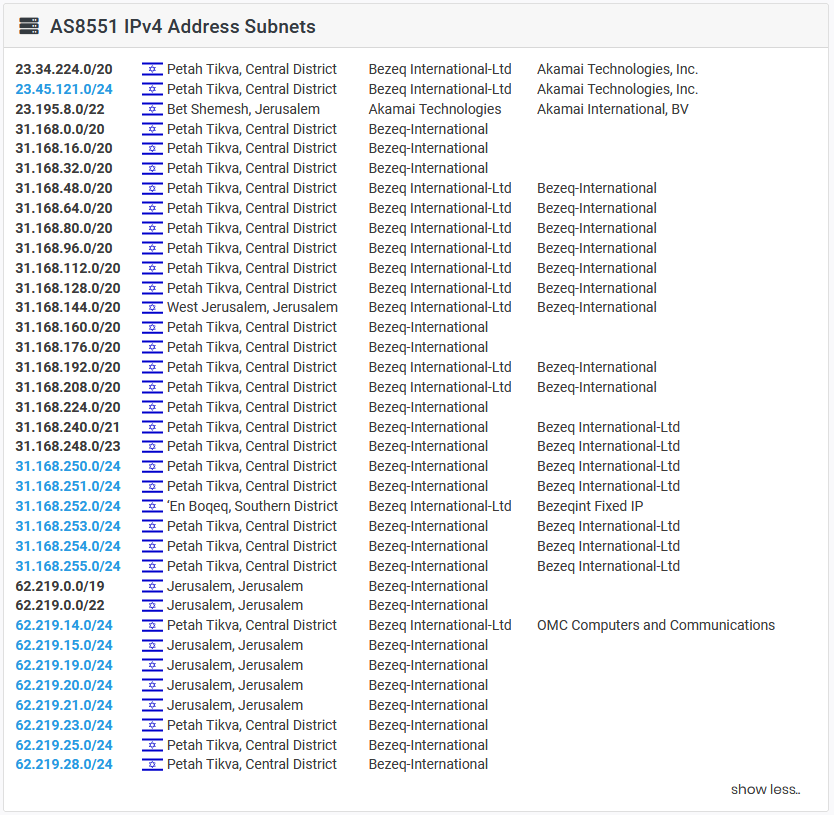
A RIPEstat query for AS8551 shows that this ASN has been found in recent blacklists “level3” or “uceprotect-level3“. What is this ? The purpose of this “RBL” UCEPROTECT blacklist is to block ASNs that allow spam to be sent from a large number of IP addresses in the network
Realtime Blackhole Lists (RBLs) can be a great tool in your security arsenal. You may not know you’re using them, but all email providers and company email servers leverage these services to verify whether servers and IP addresses are sending spam or other abusive content against a known list of offenders
These services use a number of methods to compile lists of IP addresses reputed to send spam, mostly populating them using honeypots. RBLs serve as a useful database of known abusive IP addresses

It is important to mention that UCEPROTECT is not considered to be a reliable source by some analysts : https://bit.ly/3aWYfiu
Anyway, here is an excerpt list of the suspicious IPs found by a query of AS8551 in RIPEstat
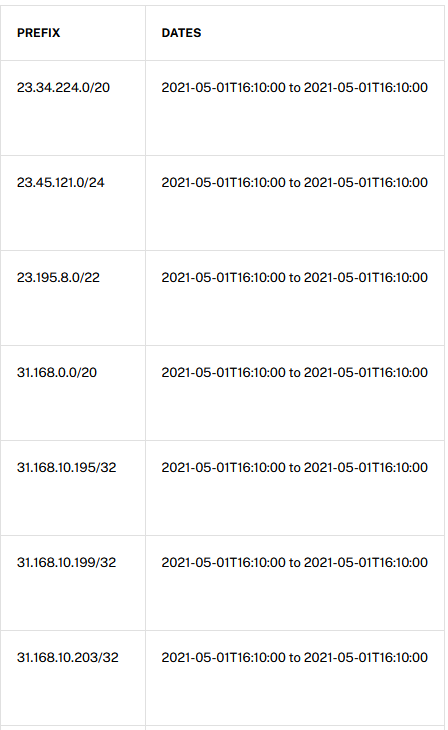
We can see that this IP list matches quite well the AS8551 IPv4 address subnets
At the time of writing this article, Bezeq was ranked in the position n°1580 of the global “UCEPROTECT Level 3 Charts”, out of 1875 records. However, it is important to mention that there are more than 10000 ISP worldwide. So, we can reasonably consider that there is a spam issue on the Bezeq network
Is it a big issue ? Not sure. Here are some statistics from Kaspersky : https://bit.ly/2QRFvKe
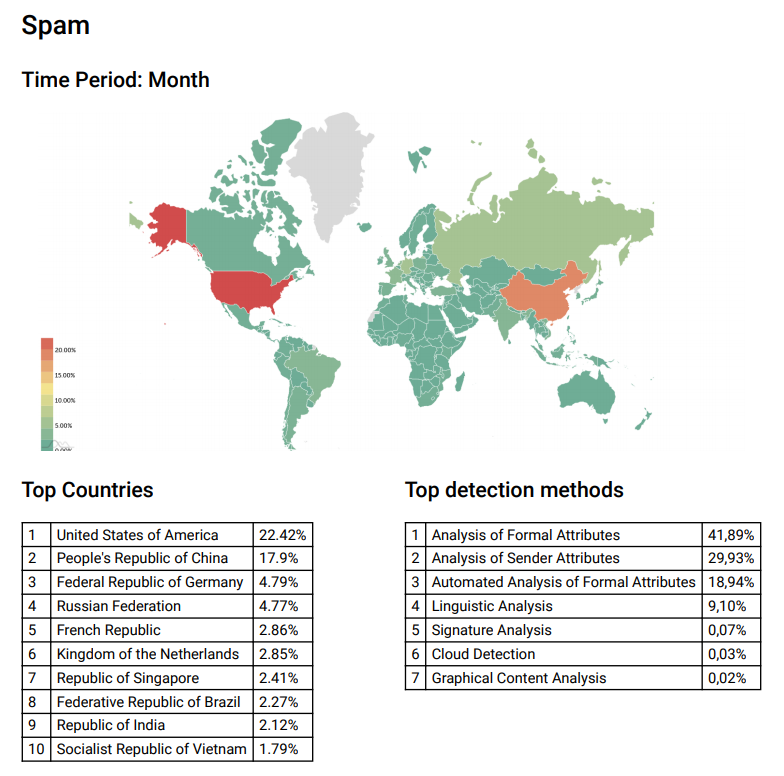
Israel is far from the “top 10 countries” for spam reports. However, in relative terms, taking into account the size of Israel, their score report shows quite a strong spam activity “per person”. Their was an article from 2014 saying that Israel “was a Mecca for spammers” when doing the ratio of spam activity vs inhabitants in the country : https://bit.ly/3nEhXop
Israel is a small country, with fewer computers than the top spam-sending countries. For smaller countries, such as Israel, the benchmark of poor anti-spam security is the number of messages sent out relative to the population. Israeli computers on average relay some significant spam activity
Does that mean that there are a larger number of infected computers in Israel that are being used by spammers elsewhere ? We can probably say, that there is room for improvement in the effective use of malware and virus detection systems, especially when you consider that Israel pretends to be a leader in cybersecurity
But to be fair, it is extremely difficult to block spam traffic, as offenders are very creative and use relays to spread. No country, even if very strong in cybersecurity, can really block spam traffic, as it also depends heavily on end users
Additional reading -> there’s a good NATO study about Israel : https://bit.ly/3hPblmd
Social media and internet manipulation
Because of its unique situation (as explained above), Israel is quite logically using the social networks for its security and political targets. Private sector companies with former officials from surveillance agencies, are coming in handy for this ! There are also many attempts to manipulate the opinion against Israel

This statement from a former Israeli intelligence officer says it all (https://bit.ly/3baNHMA)
“Social media allows you to reach virtually anyone and to play with their minds. “You can do whatever you want. You can be whoever you want. It’s a place where wars are fought, elections are won, and terror is promoted. There are no regulations. It is a no man’s land.”
Before continuing, it is very usefull to watch this video about Israeli private intelligence companies, as it will set the overall tone, and introduce major companies such as PsyGroup, NSO, Black Cube,…
There has been several manipulation tactics deployed. I provide here below some examples
PsyGroup
PsyGroup is a former Israeli private intelligence agency. In 2016, they had started a campaign against “Boycott Divestment Sanctions” activists on US college campuses, private sector and NGOs supporting the BDS cause
PsyGroup collected informations on these activists, either from social media and from HUMINT sources (intelligence methodologies)
PsyGroup operated a website “outlawbds.com” that is now out of service, which published informations about BDS activists. Some traces of this website can be found in the wayback machine (https://bit.ly/3xVW48B)

In this site, you could find the photos, names, and links to the social media pages of these activists (Facebook, Twitter, Linkedin,…)

The activities against the BDS movement had been coordinated with the code name “Project Butterfly”, with top participants including former intelligence and government officials. The project has been structured with a complete report issued by PsyGroup, detailing its purpose, timing, budget,…

I would like to mention that there has been a lot of controversy around the BDS movement. There are still articles to be found about it in 2021 : https://yhoo.it/3hkOVJ0
Through the project Butterfly, Israel used some ways to identify, expose the activists and defend itself
Social media bots
There have been several reports that Israeli politicians make use of Twitter bots to influence this social network and push it to their advantage : https://bit.ly/3vSCisN
On the other hand, there have been recent reports of Twitter bots agressive towards Israel
One tool to uncover twitter bots / fake accounts, is TwitterAudit (requires a PRO version to proceed with searches). The accuracy and interest of this tool is documented here : https://bit.ly/3txHXD8
Israel, like any other countries, has to fight against fake news propagation. A Twitter bot, for example, can be created with some programming knowledge by any individuals. There are quite a few tutorials to be found on YouTube
There has been an initiative launched to create an App that involves any citizen to alert about fake news and open criticism against Israel : Act.IL

“Act-IL is a platform that leverages the power of communities to support Israel through organized online activity. It is the place where all pro-Israeli advocates, communities and organizations meet to work together to fight back against the demonization and delegitimization of the Jewish state”
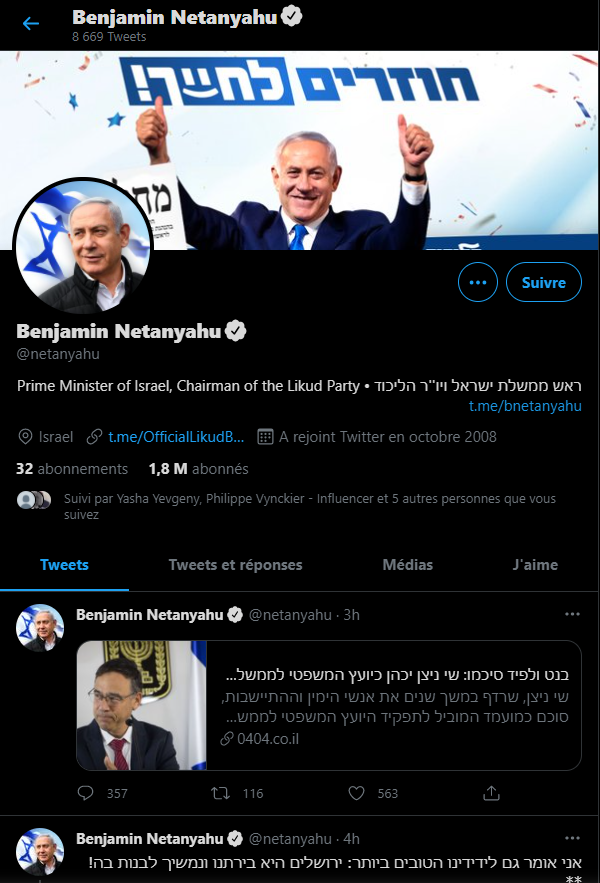
Netanyahu social media empire
The Israeli PM is well know to have a strong social network basis : https://bit.ly/2R5BfXQ. Much like any high ranking politician, he spends money with his party “Likud” to manage his social network activities :
- Appointment of dedicated resources to manage his accounts
- Cash expenditures to promote his posts
- Use of consultants to help gain visibility, influence, reputation
Github Projects
In this paragraph I’m going to review some of the codes to be found in Github, searching with the key words “Israel” and then “Palestine”. There are a few interesting resources that provide additional context about the hobbies, the interests of the coding community out there
One Kilometer | Fighting for democracy in Israel : https://github.com/guytepper/1km.co.il
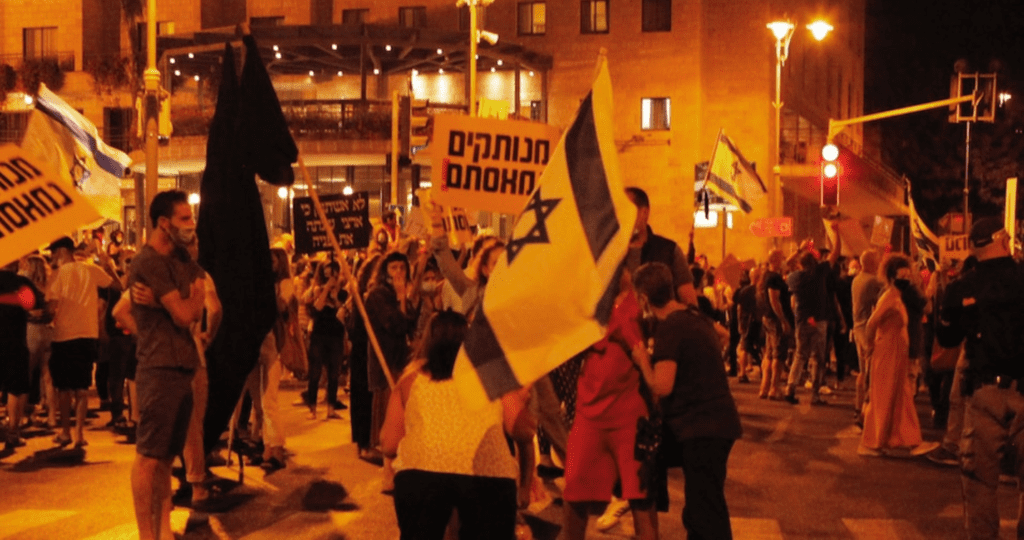
Israel’s second lockdown due to COVID19 had shaken the country with a political crisis, the government restricting the right to protest to a distance of one kilometer from ones homes. Because of this, some members of the anti-Netanyahu protest movement have launched an App dedicated to manage protests in the one kilometer radius
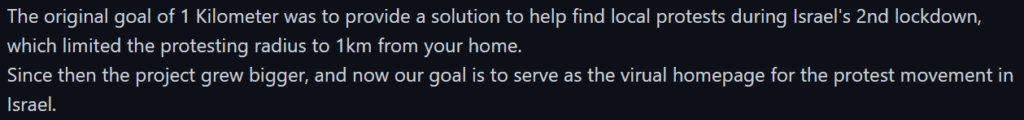
After providing your address, the site will refer you to a list of protests happening in your vicinity and will even provide a link to the WhatsApp group of that specific demonstrations’ organizers
The code is written in React – based upon Javascript – for the Front End, and Firebase is used for the Back End. It loads some important libraries
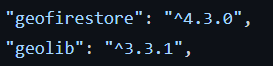
GeoFirestore selectively loads the data near certain locations, keeping the application light and responsive, even with large datasets. GeoLib is a computational geometry library. Both will be usefull in the context of this app, for location based storage and calculation of radius/distance
The user location is catched
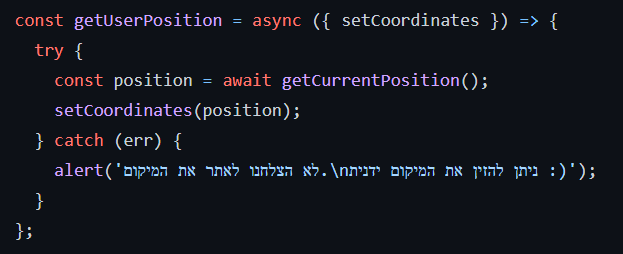
Protests are created
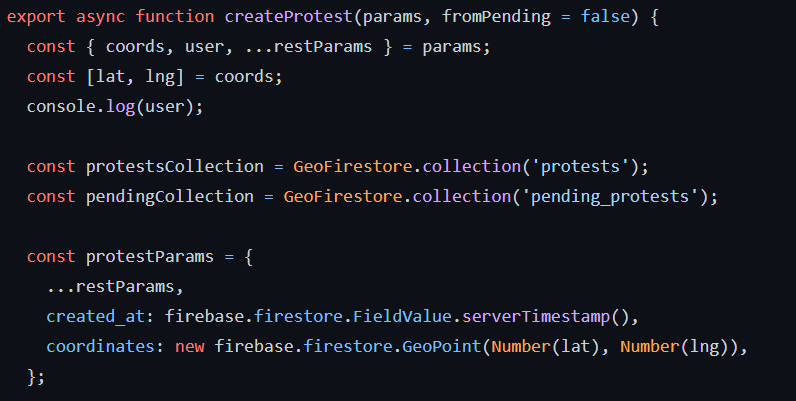
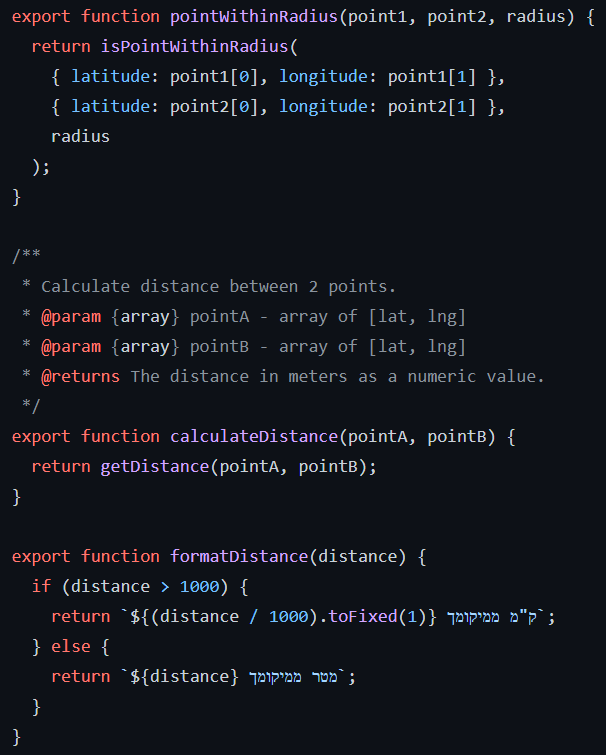
Then protests are sorted to match the user location
Isracoin | The Israeli Cryptocurrency : https://github.com/israelcoin/Isracoin
Isracoin is a defunct cryptocurrency “made in Israel”. It was launched in 2014 but was quickly phased out, at a time when Bitcoin was still in its infancy. Here is a background statement issued when Isracoin was launched
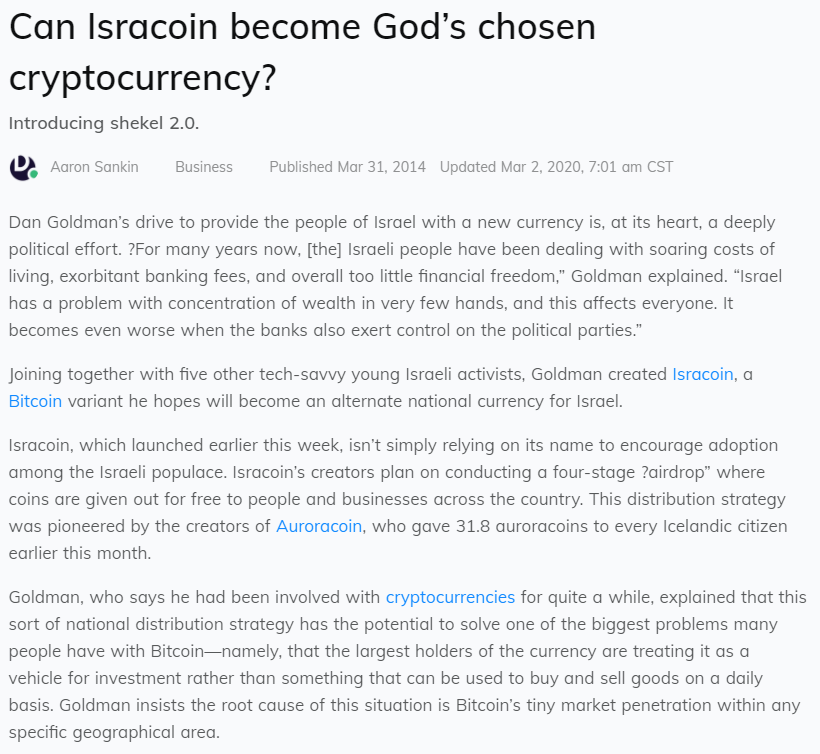
Isracoin was based on the Blockchain technology. This launch did not work as expected. However, Israel plays nowadays a leading role in cryptocurrencies. There are several crypto stock exchanges : https://bit.ly/3fhsCSa
Currently, the Bank of Israel is taking gradual steps in preparing for the launch of its own central bank digital currency (CBDC) : https://bit.ly/33ICLSj
The currency in question for Israel would be the digital shekel. But, there are no firm steps laid out at this moment in time
The Github page includes a basic Python script pyminer.py, simulating a miner. The code shows quite clearly the way that hashing is performed in order to mine new blocks
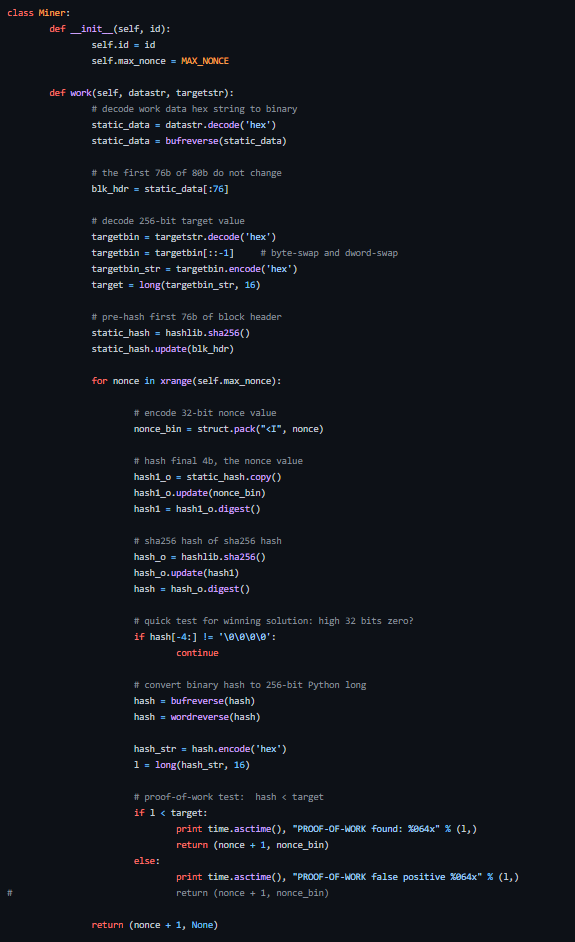
It is however a CPU-only algorithm, and doesn’t use some of the more advanced mechanisms for accelerating the hashing process. And therefore, it will be slow to run
Despite this, it definitely offers a good introduction into how the generation of blocks and hashing works, without the added complexity of having to deal with GPU-based mining code, which is highly optimised and as a result will likely be more difficult to understand
The Isracoin App itself has been written in C++, obviously to ensure a good performance. It also includes the Qt GUI framework to build the application
Some usual security countermeasures inherent to C code were taken into account (protection against buffer overflow and other stack attacks,…)
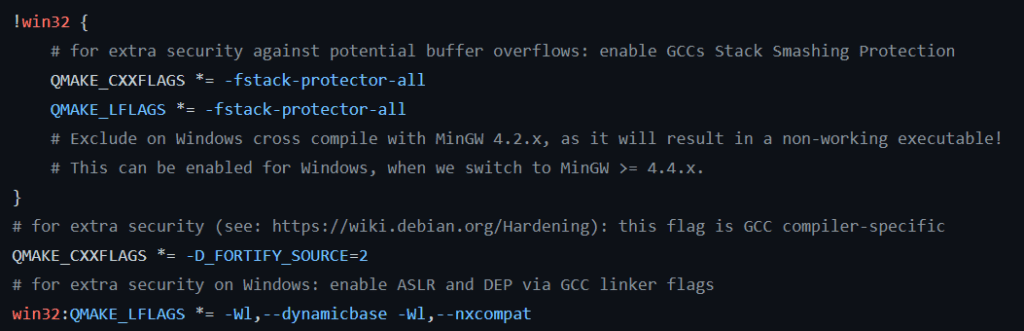
Then, the C++ code is very complex and would need a full and long article to explain it in detail, as this App is a fully fledged application, including a complete GUI, mining, wallet management and more. I will just show some comments included in the mining file, to give a preview of what parameters it considers for the mining process
RedAlert | Real-time rocket alerts : https://github.com/eladnava/redalert-android
This app has been created following the 2014 clash between Israeli and Palestinians, and the rocket attacks against Israel’s south by Gaza Hamas : https://bit.ly/3tO5S1g
It somehow reduces the risk that those in the affected areas would not hear the instituted “Red Color” emergency sirens, that are supposed to warn residents 15 seconds in advance of a rocket explosion
As a “backup” warning system, Red Alert has been developed. It sounds a warning on cellphones at the same time the real siren goes off
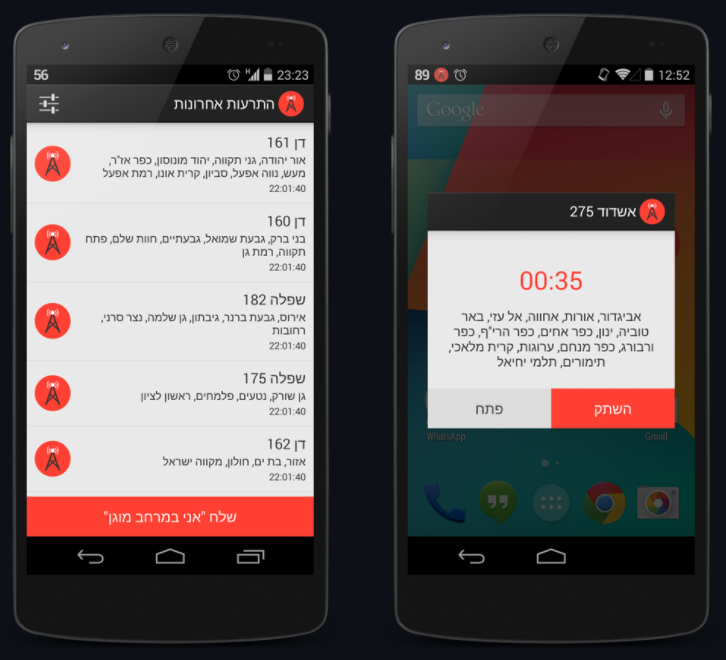
The app utilizes real-time alert data provided by the Home Front Command (Pikud Haoref). Rocket alerts are detected using the open-source pikud-haoref-api Node.js package
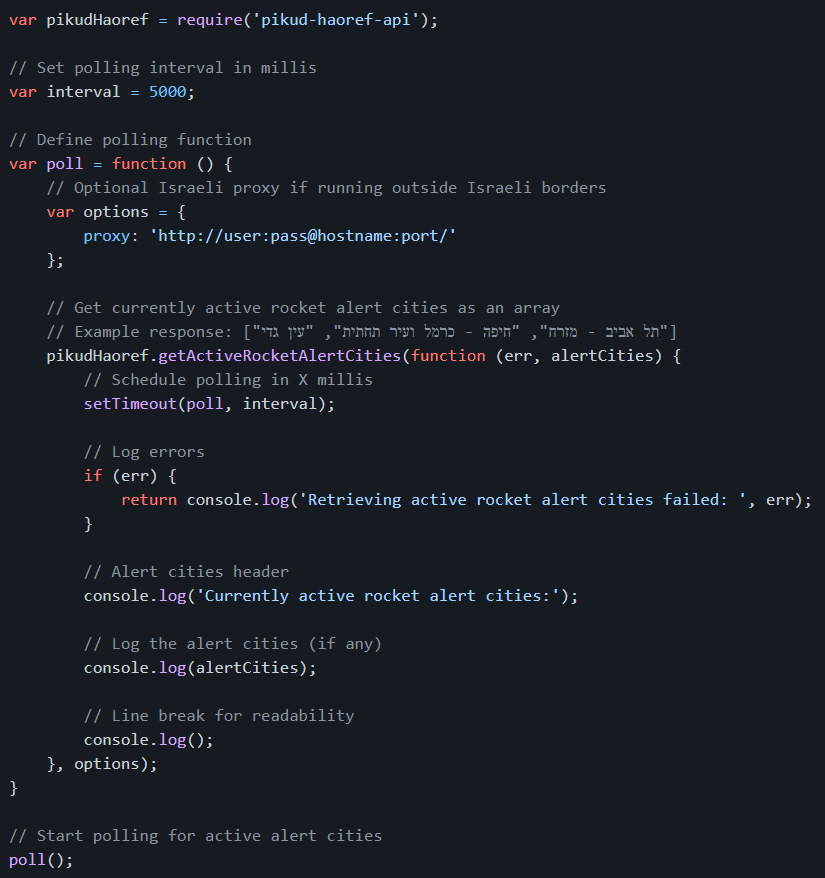
The App is written in Java. The user can select its location and city
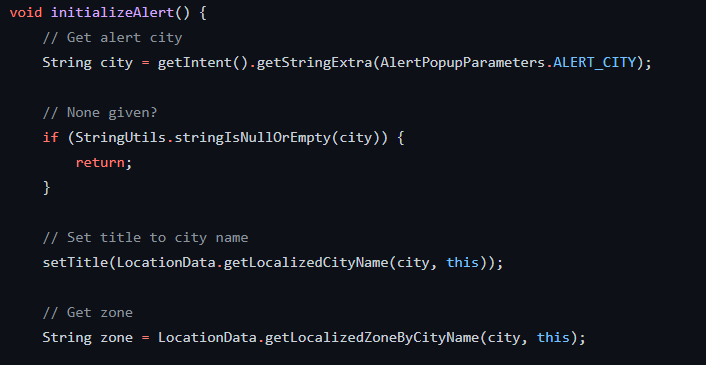
As shows the strings.xml file, here are some of the functions provided by this App
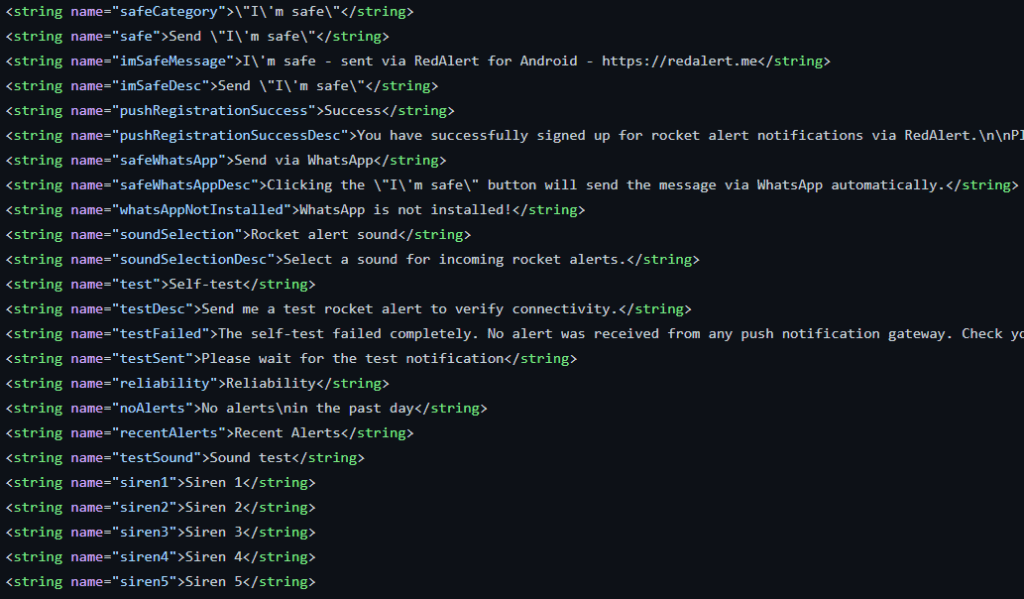
The App will generate notifications when Rockets are launched around the user location
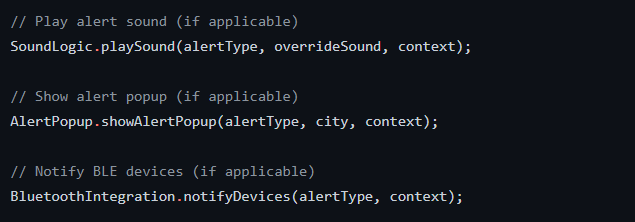
Open Pension | “Hasadna” project aimed to revealing the secrets behind the Israeli pension market : https://github.com/hasadna/open_pension
This is one project of the “Public Knowledge Workshop”. Here below their purpose
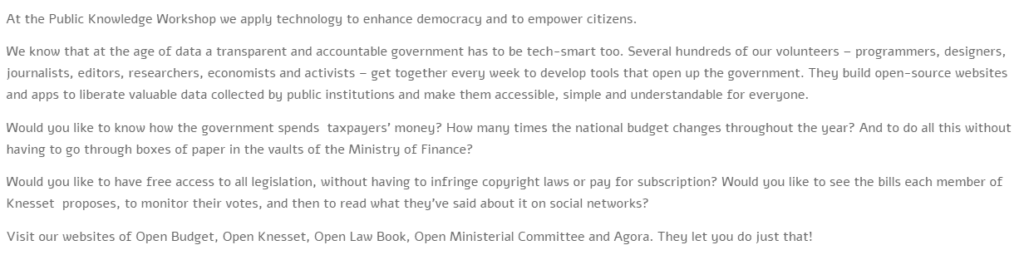
This is, in my opinion, a great initiative, showing the commitment of Israeli citizens and the wish for transparency in public services
We have seen the fast COVID19 vaccination campaign in Israel, in exchange of a large medical data access to Pfizer : https://n.pr/34ezLNG [note : Israel has applied cyberwar crisis management to the COVID19 issue]
Although there has been voices against it, this confirms that Israel is relatively opened in terms of data publication
Hasadna organizes some Hackhaton to accelerate the innovation around these projets
They run several disclosure projects : https://www.hasadna.org.il/en/projects/
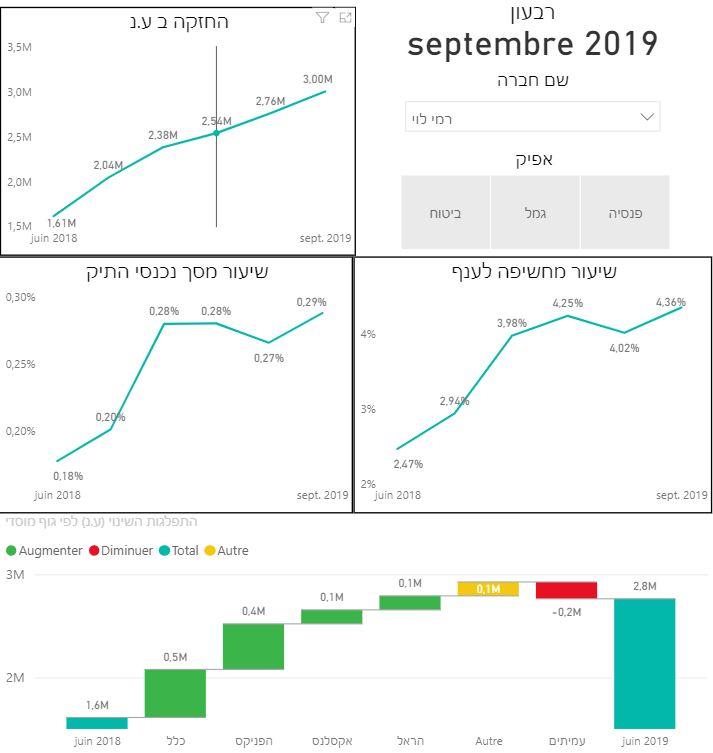
I have chosen the OpenPension project, aimed at providing an insight into the investment policy of pension funds in Israel, including their risk management and asset allocation. Part of the tool is based upon Microsoft PowerBI for data visualization
The code available in the Github page, based upon Go and GraphQL, is gathering data as in the exemple given below
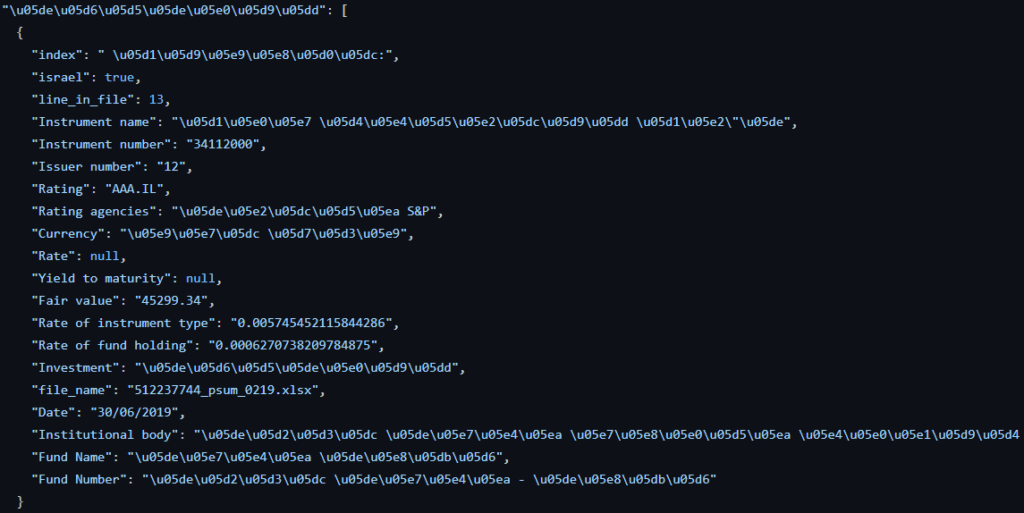
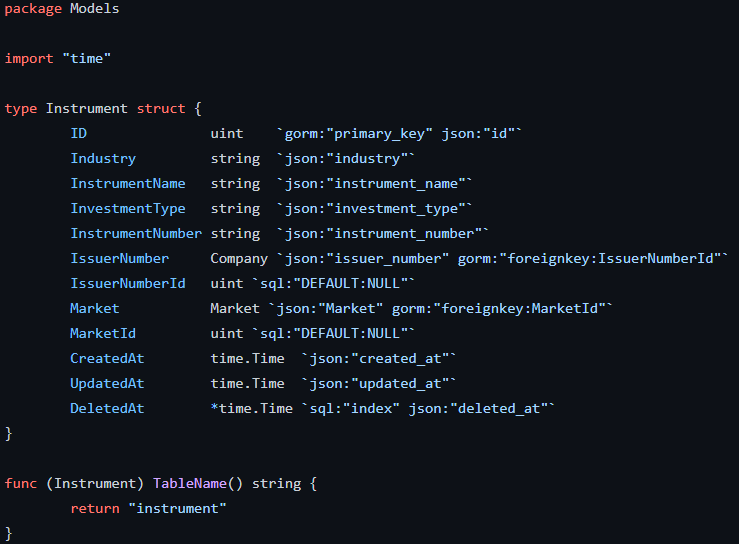
The corresponding data is placed into multiple structures as follows (exemple with financial instruments)
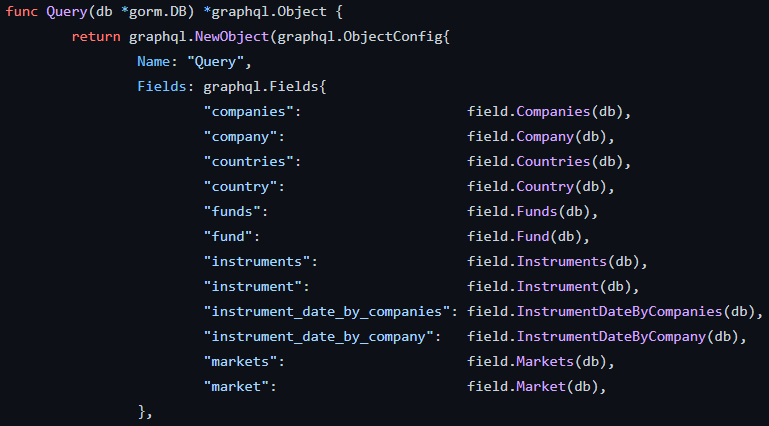
To achieve this, the App is based upon multiple queries in the database, looking for the expected attributes
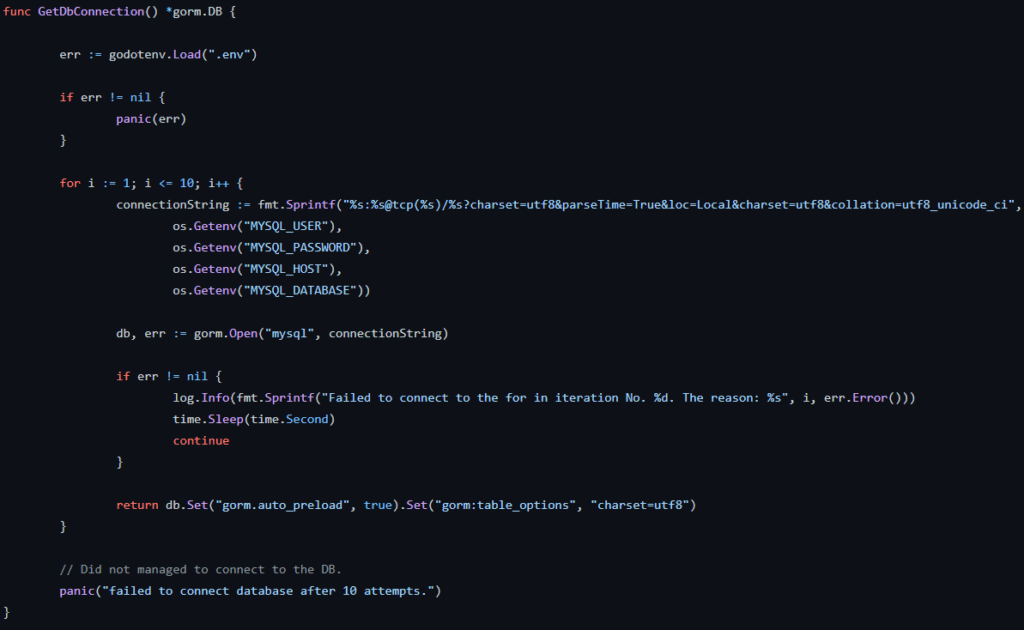
The connection to the SQL database is managed with this module
Israel Palestine Petition : https://github.com/100millionvoices/israel-palestine-petition
This is a petition platform, this one being specialized on the Israel | Palestine issue. The code is strongly borrowed from https://github.com/alphagov/e-petitions
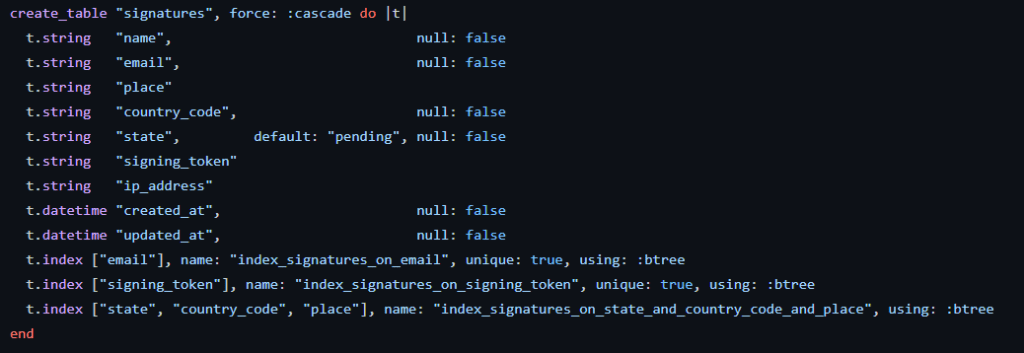
The code is written in Ruby. Here below, the data which is collected each time the petition is signed
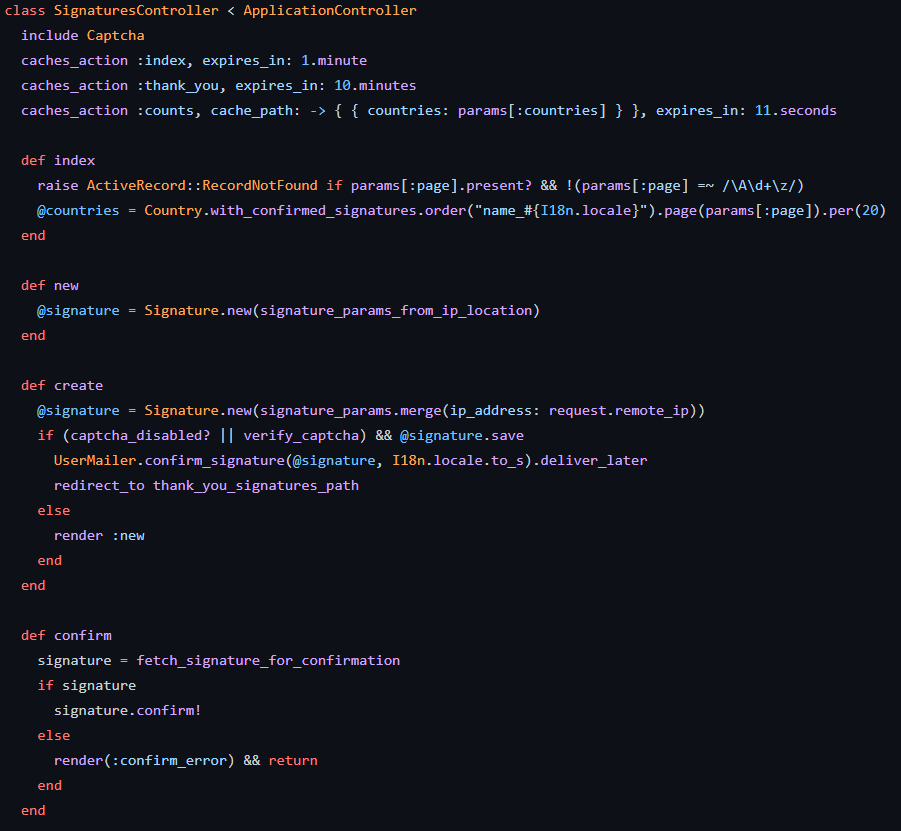
The signature process includes a captcha validation
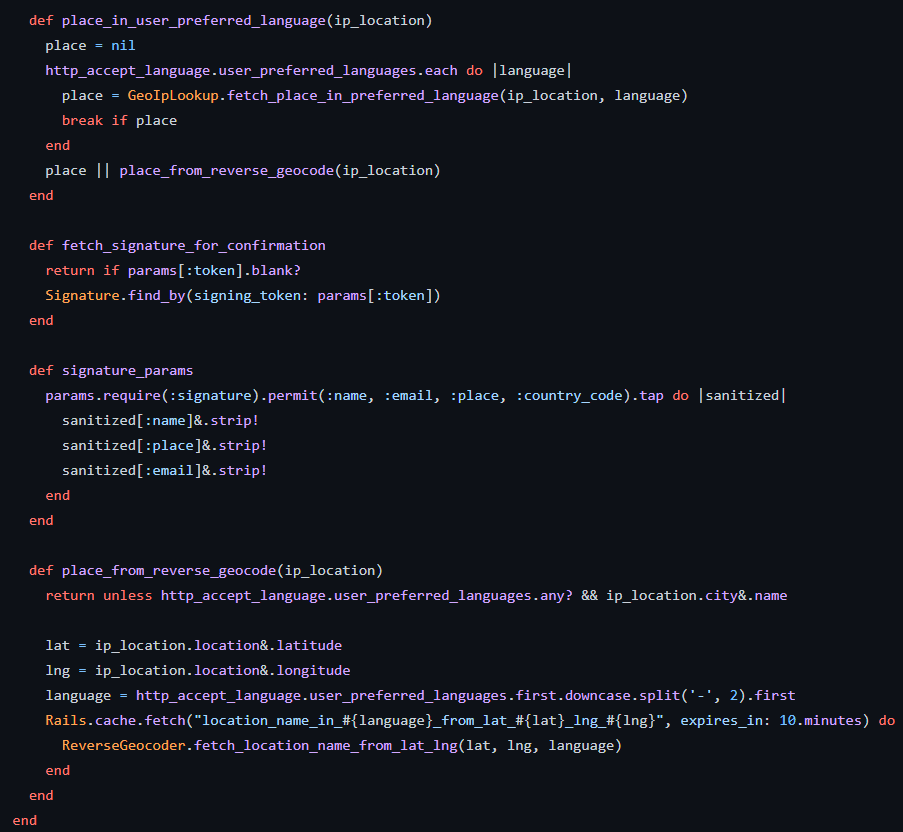
It has also the I18n code : https://en.wikipedia.org/wiki/Internationalization_and_localization
So, your web page is going to be adapted to your local settings as per your Geographical location
Politibot | Create tweets like Israeli politicians : https://github.com/GilZ/politibot
Politibot takes recent politicians tweets, creates a Markov chain from them, and then tries to create a tweet that sounds like something they would tweet
A Markov chain is a model describing a sequence of possible events in which the probability of each event depends only on the state attained in the previous event. Nowadays, it is in use in Speech recognition, for example
The App is written in Python. Here below a preview
It includes the dependency markovify. It is a Markov chain generator. Its primary use is for building Markov models of large texts and generating random sentences from it
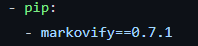
The App is going to follow tweets from the following politicians
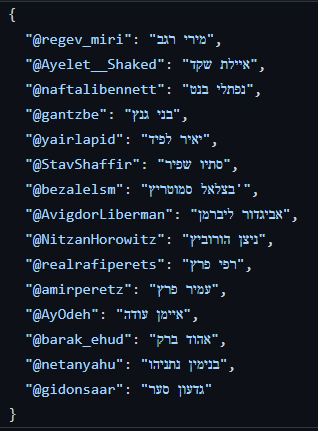
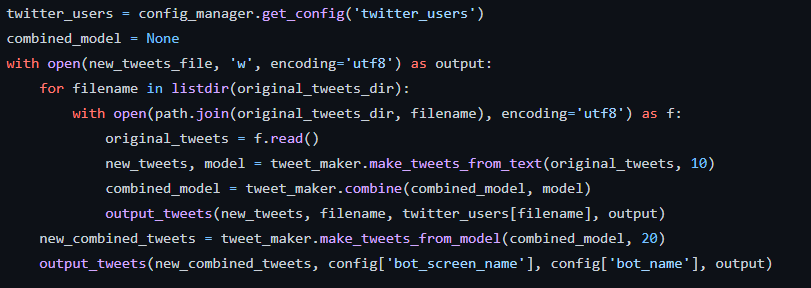
The tweets from these politicians are extracted using the following code
The tweet maker is quite basic and relies entirely on the markovify dependency
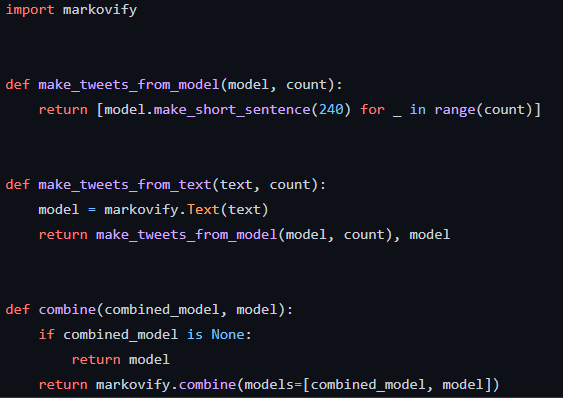
The tweets will be generated finally with this loop
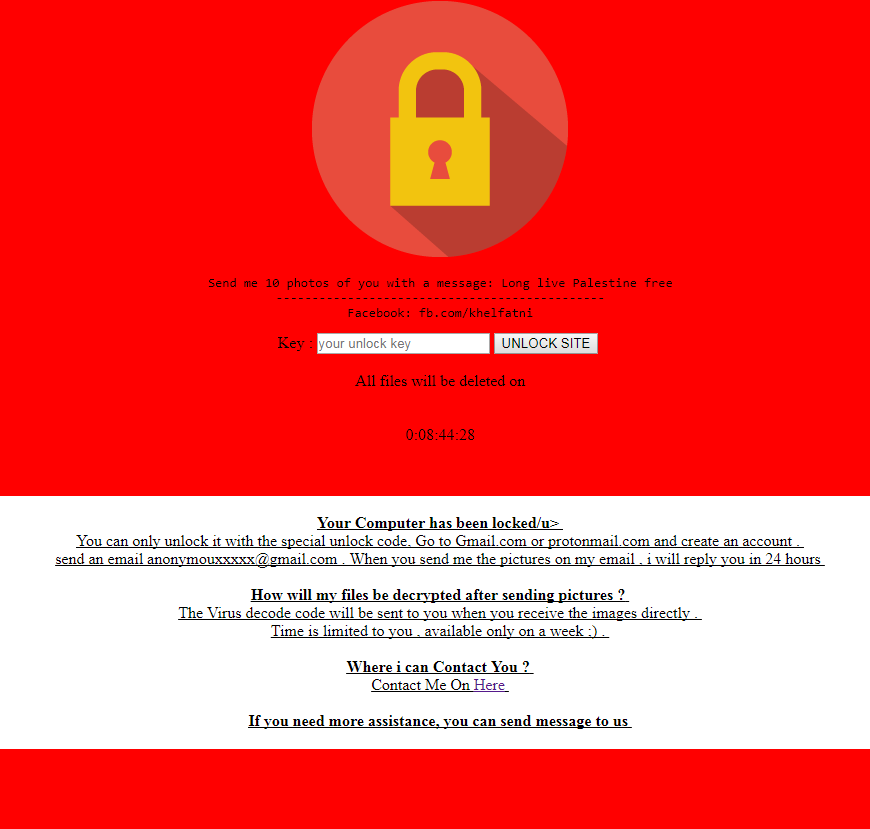
Ransomware free Palestine : https://github.com/aymankhalfatni/Palestine_Ransomware
The ransomware, once your computer has been locked, is asking you to send 10 pictures of you with the message “Long live Palestine free”, to the account anonymouxxxxx@gmail.com. Then, you are supposed to receive an unlock key shortly after
A facebook link is referenced on the screen : fb.com/khelfatni (but this account is inactive)
Hash SHA256 in the text file “hashVIRUS.txt” :
c89944f9ec704c2b8da3a1acf726699022e7c68334110f72007d762217a9a4a5
Hash SHA256 of the file ransomware.exe (unpacked) :
0261b2122b402e5ac232c86577bba26818e7a5687881c35c566c5f00c19afe52
Let’s have a look at the two attached files available in the Github repository
ransomware.html
This file includes the necessary code (HTML and Javascript) to display the above locked page. It also includes a countdown mechanism
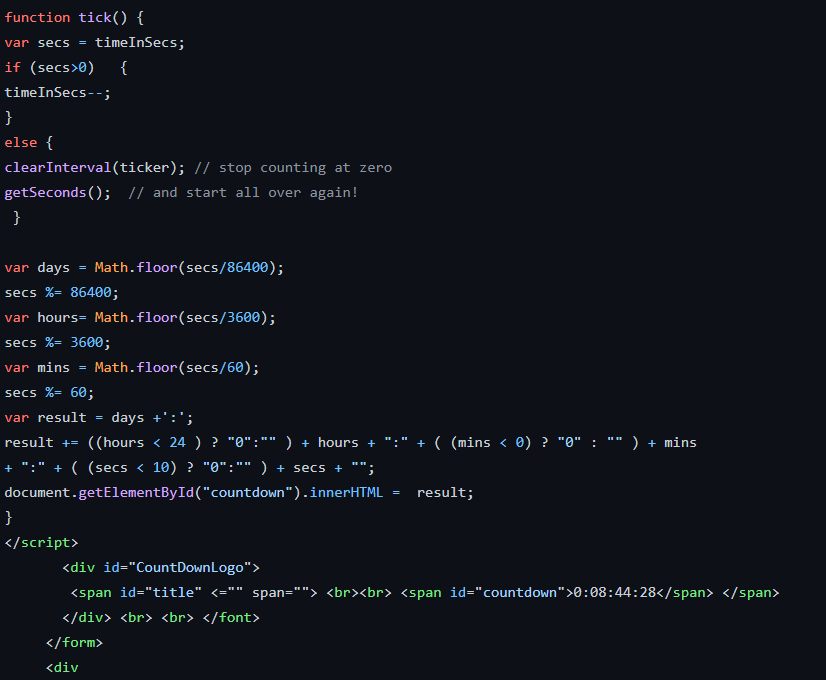
You can run this html file in your browser, and you will see that the code is working as the countdown is actually ticking
ransomware.exe
Let’s download this file in a Virtual Machine, just to make sure it does not harm our computer. As a first check, I run PEiD to check if the file is packed. Yes, it is ! It’s packed using ASPack
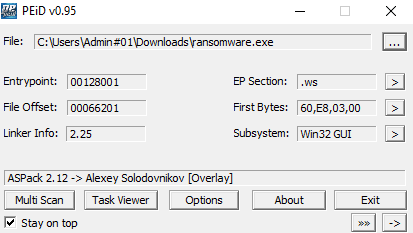
A search in Google and we find a tool to unpack it : https://www.aldeid.com/wiki/AspackDie
When clicking on the ransomware.exe, another windows file box is opening. We are invited to find a .wex file and open it
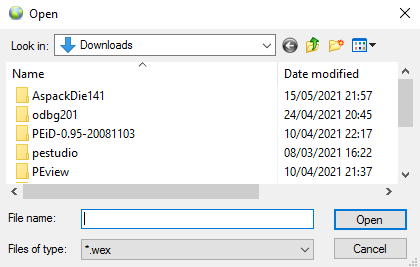
A .wex file is a WexView Browser Data file. WexView is a self-contained browser (WebExe)
Other way round, we can transform the html file into an exe and execute it outside of a browser
We can assume that the ransomware.exe was built using the ransomware.html and the WebExe software. So, this .exe can be distributed by any means and will launch in a browser environment whatever your PC configuration
technical analysis
From the hash given in the text file “hashVIRUS.txt”, we can find several resources on the web :
indicators : https://bit.ly/3yhAOdC
behavior : https://bit.ly/33Ou74M
what it does : https://bit.ly/2RZmbew
It’s a screen locker and not a real ransomware !
From the hash of the file ransomware.exe (unpacked), here is what we find :
indicators : https://bit.ly/3uSPDkU
behavior : https://bit.ly/3hrmJV6
There is no call to the HTML file. On VirusTotal, Microsoft classifies it as the malware Program:Win32/Wacapew.C!ml. There’s a post on Reddit which provides some background
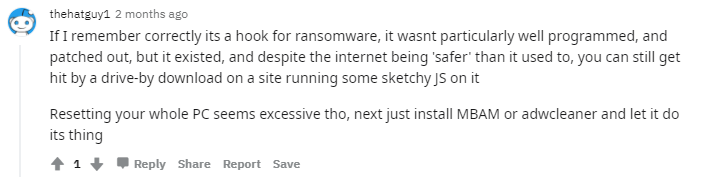
Overall, the files available look like an unfinished product, a simulation of a locker program but the components provided are not integrated together
Dynamic-ransom | Ransomware Detection : https://github.com/skaspi/dynamic-ransom
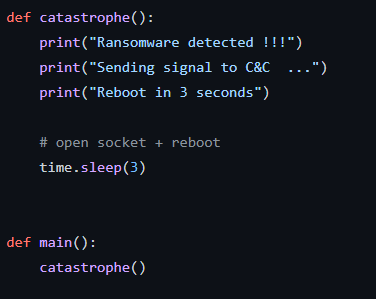
This is a Python script. It is based on the fact that during encryption by a ransomware, files extensions are modified. The script will check if the files in your system are modified and considers that this is a ransomware if at least 40 files extensions have been modified
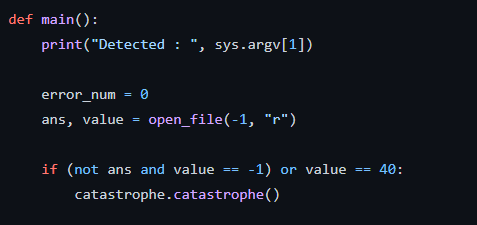
A “watchdog” screens and monitors changes made to the directory location it is pointing to
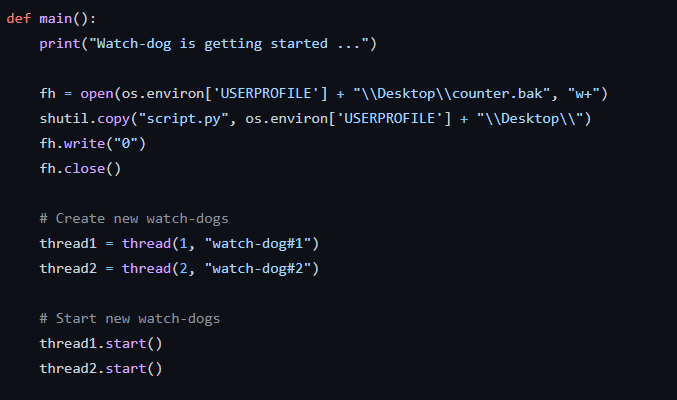
The program will issue the corresponding warnings
Israeli ID validator : https://github.com/atlanteh/israeli-id-validator
This is a basic ID validator written in Javascript
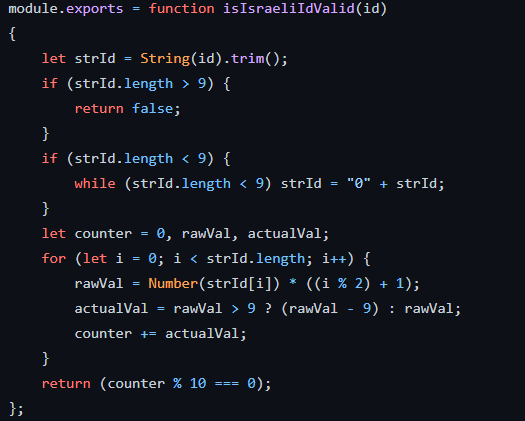
Why is this interesting here ? The ID is the basic identification number for a given citizen and is widely in use : https://bit.ly/2Qm7y4m

Data of deaths in Israeli-Palestinian conflict : https://github.com/aiza-k/Israel-Palestine
This one provides data about : deaths in Israeli-Palestinian conflict, and US military aid to Israel. The App is coded in R language (statistical analysis) to calculate the graphs from the datasources. You then have the possibility to launch the analysis with the provided html file, or directly opening the corresponding PDF reports
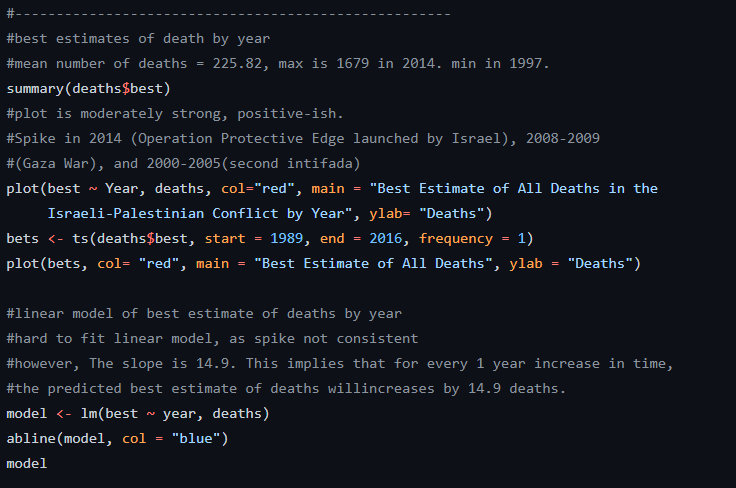
Some interesting facts about the US Military aid to Israel :

The average yearly US Military aid to Israel has been 2.6 billion USD
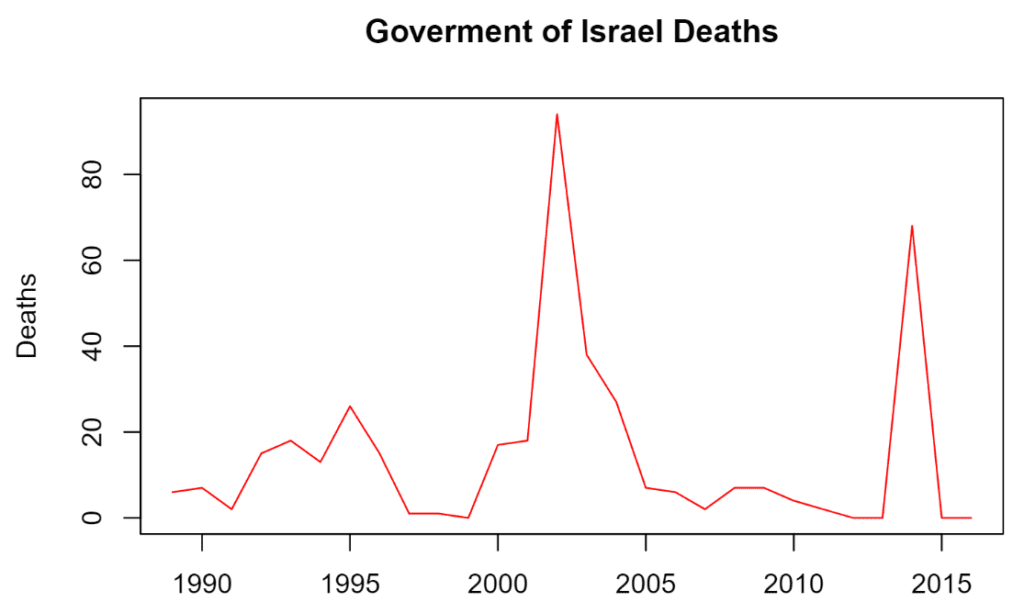
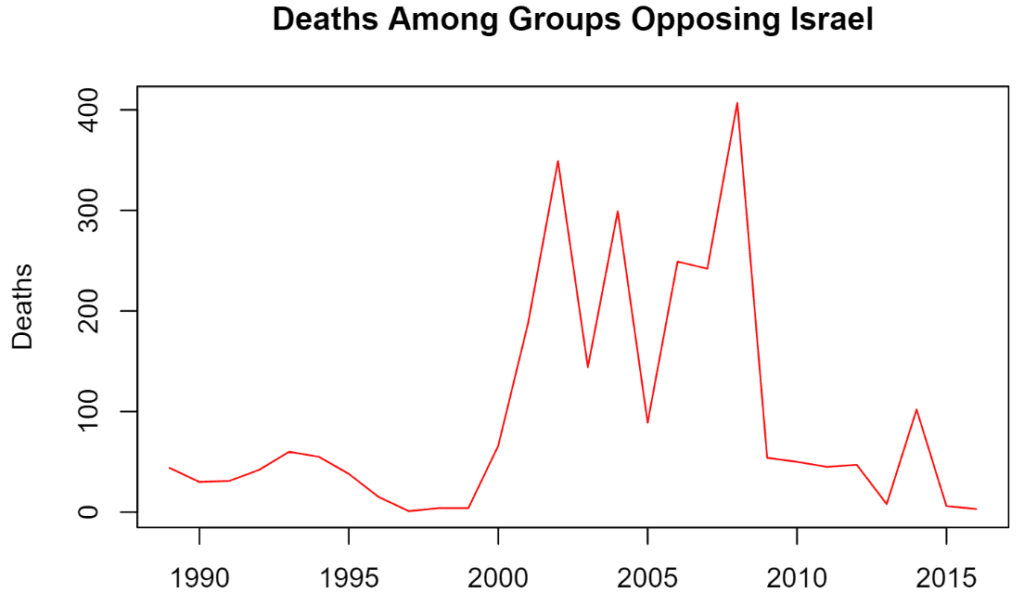
About the death rate, there has been much more casualties on the Hamas & Palestine side
NSO Group
As we said earlier in this article, Israel has a strong cyber ecosystem with some companies dedicated to surveillance activities. Frequently, their technical staff is coming from military & security agencies, such as Mossad or Unit 8200
NSO Group is one of these companies

Among other products and services, NSO has developed Pegasus : a spyware that can be installed on devices running some versions of iOS, Apple’s mobile operating system, as well on devices running Android
Discovered in August 2016 after a failed attempt at installing it on an iPhone belonging to a human rights activist, an investigation revealed details about the spyware, its abilities, and the security vulnerabilities it exploited
Pegasus is capable of reading text messages, tracking calls, collecting passwords, mobile phone tracking, accessing the target device’s microphone and video camera, and gathering information from apps
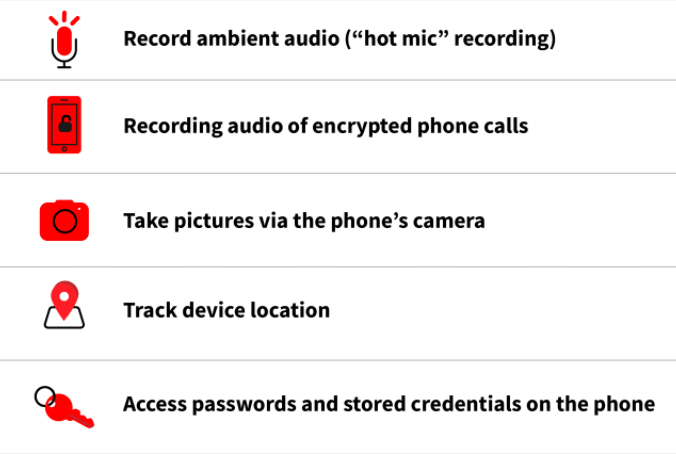
Citizen Lab tracked the suspected infections, scanning servers associated to Pergasus and conducting a global DNS cache probing study : https://bit.ly/3wu2om6
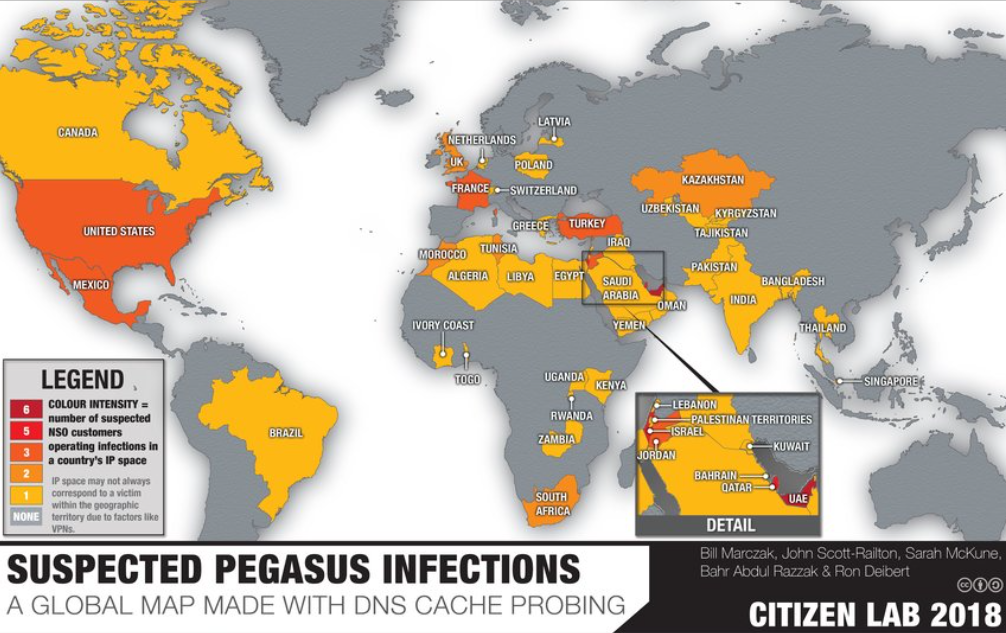
NSO has been critized for facilitating human rights abuses, for example in the following countries :
India
In late 2019, Facebook initiated a suit against NSO, claiming that WhatsApp had been used to hack a number of activists, journalists, and bureaucrats in India, leading to accusations that the Indian government was involved : https://bit.ly/3hI9z6g
Mexico
Pegasus has been used to target and intimidate Mexican journalists by drug cartels and cartel-entwined government actors : https://bit.ly/3vdsREm
Saudi Arabia
Pegasus software helped Saudi Arabia to spy on Saudi dissident’s smartphone and track his communication with journalist Jamal Kashoggi
He was assassinated in 2018 : https://bit.ly/3fAYKQR
Facebook, Google, Microsoft and other Tech Giants, have started a lawsuit against NSO, to reduce the risk of proliferation of hacking technology : https://bit.ly/3fIlu1r
Currently, NSO is said to be in talks with Jordan : https://bit.ly/3fEddeH
Pegasus has been used both on iOS and Android. Here are two reports from Lookout providing a great deal of details about the spyware inner working. Since iOS and Android have been patched in the meantime, those reports only apply to older versions of these OS
The spyware relies on some zero-day vulnerabilities
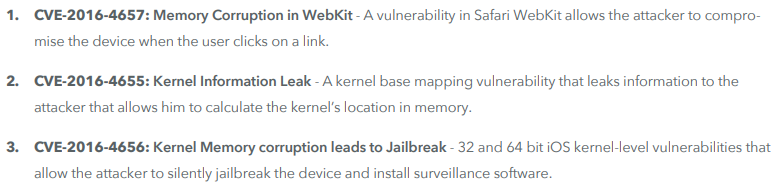
It starts with a phishing message. As soon as the user clicks on the provided link, the spyware will install
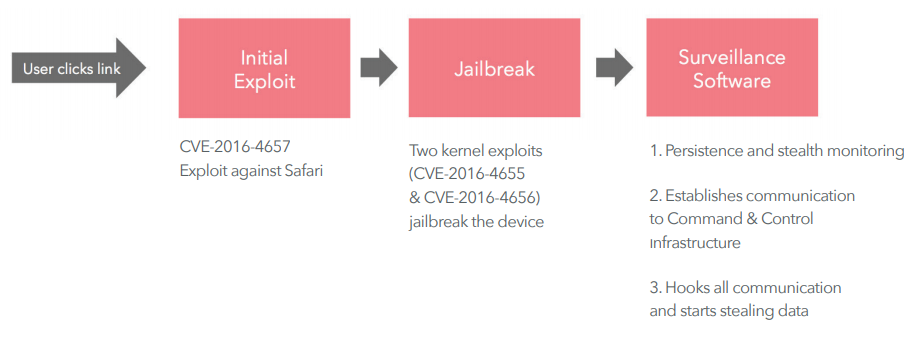
Pegasus is going to grab many user data. For example, here is the code for catching user passwords

And here is the code for catching WhatsApp messages on the device
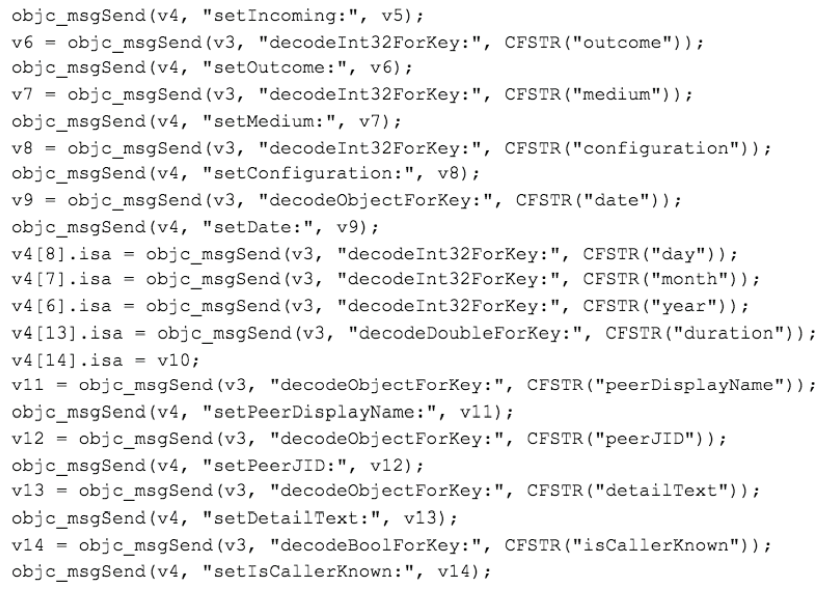
The spyware, in the form of an apk, has been distributed to the user via phishing attacks. The apk uses some vulnerabilities in previous Android versions, allowing the attacker to gain root access. A module called Framaroot has been used : http://framaroot.net/
To complete the installation, Pegasus will look the browsing history and activate only if it finds the necessary configuration strings
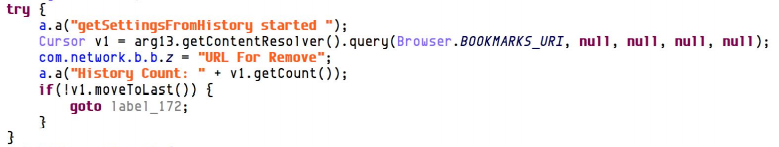
Pegasus will then establish a connection with the Command and Control server

The communications with the C&C server are encrypted
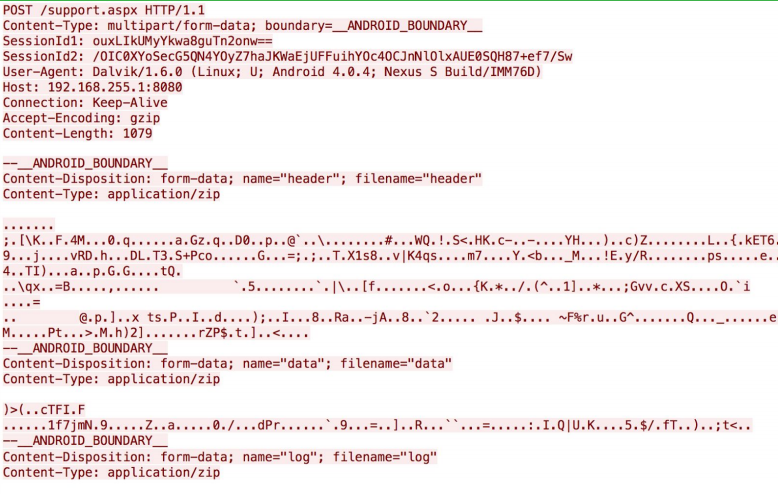
The data will be exfiltrated in XML formats. Here an example with calendar events
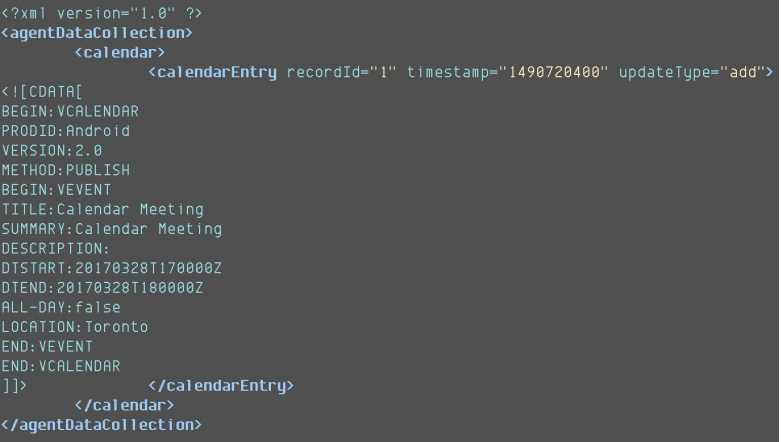
Pegasus will maintain persistence, as on iOS, and extract/forward all relevant data in the phone to the C&C server
X.509 Certificate
The root CA certificate installed by the Pegasus spyware was intended to be used to encrypt communications to its C&C server
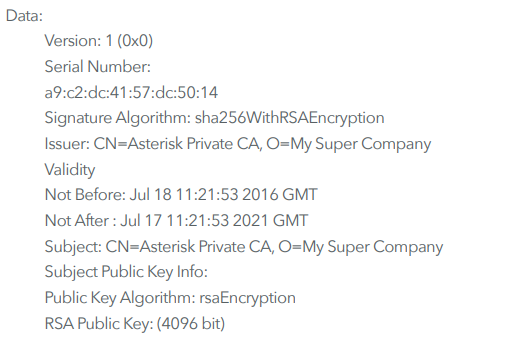
Using a self-signed root CA certificate with this custom, expensive, nation-state-only espionage software makes sense, as buying a certificate from a regular public CA establishes a payment and customer trail
Here is an analysis of this certificate : https://bit.ly/3oCxPYY
Overall, Pegasus is really a complexe piece of spyware. It has been designed professionally and is of an advanced quality level
NSO has also been able to take advantage of the zero-day ecosystem existing in Israel, essential to exploiting flaws in the mobile phones and attacking them
Zero day business
There are several actors in Israel :
NSO Group, which we already presented in the previous chapter. NSO is always looking for zero-day, either by their own research or buying external ones
They target mostly mobile phones hardware
Incredity, an Israel-German platform, dedicated to the disclosure and monetization of zero-day : https://incredity.com/
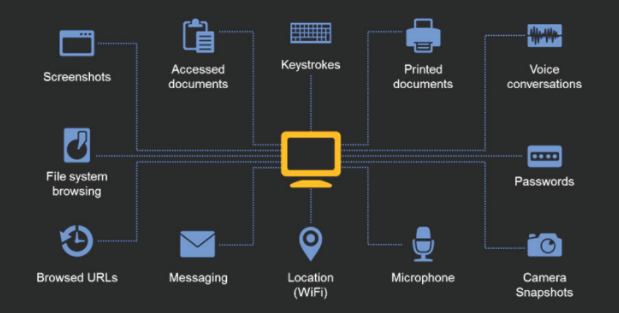
Elbit Systems (Cyberbit), which is a military equipment company, developed a spying software called PSS Surveillance System (for PC) : https://bit.ly/3ywxlIn
They target mostly PC hardware. PSS is distributed via phishing attacks
There are very good informations about PSS here : https://bit.ly/349Efp8
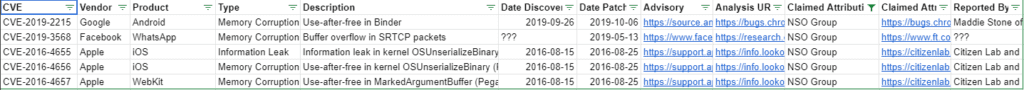
Here is a Google Docs table of known zero-day : https://bit.ly/3ywSiDa
It provides an overview of major zero-day globally, where we find NSO zero-day
Zero-day are difficult to find and hackers are trying to sell their research to private companies (such as Incredity) or to government agencies. Sometimes, governments launch covert calls to researchers to supply zero-day
Israel does this, and some years ago, a Request For Information (RFI) was disclosed to the public : https://bit.ly/3f9licb


According to a report from Fireeye, here is the year 2019 map of zero-day exploitation by hacking actors : https://bit.ly/3veuNMS
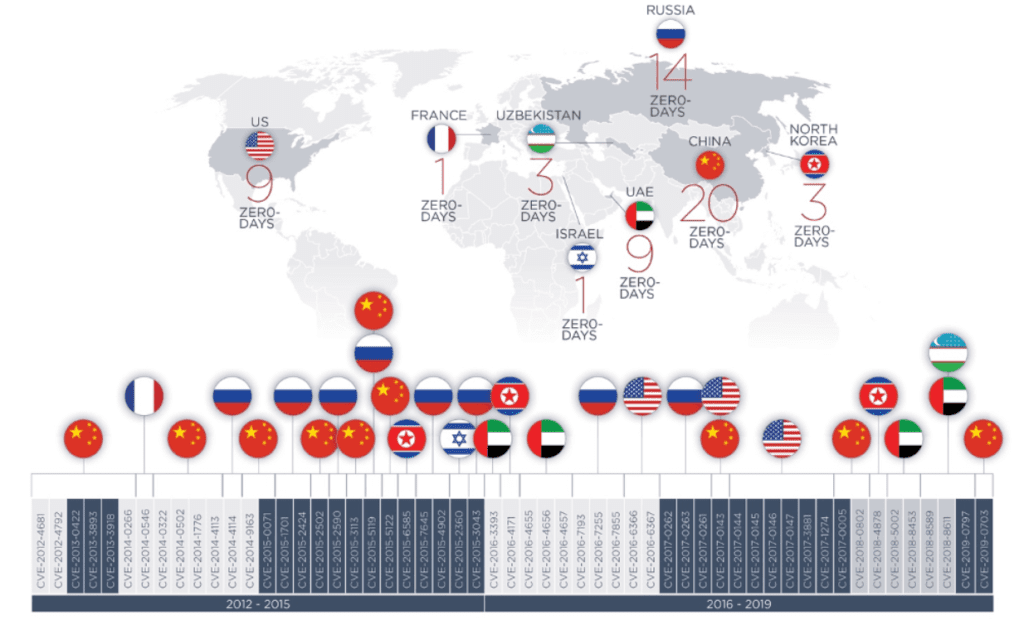
Israel has the NSO Group zero-day in the list, but other known cyber majors are beyond (China, Russia, USA, UAE,…)
Attacks from Israel
Israel uses offensive security as a standalone action, or in combination of kinetic force
Here below a summary of some known attacks :
| Date | Target | Summary | Link |
|---|---|---|---|
| 10/2007 | Syria | Hack air defenses | https://bit.ly/3hJDQ4F |
| 03/2009 | Syria | Malware loaded into the PC of a Syrian government official | https://bit.ly/3vapkGW |
| 11/2011 | Palestine | Control of the digital infrastructure | https://bit.ly/34gL2wZ |
| 06/2012 | Iran | Stuxnet malware | https://bit.ly/34hIOhe |
| 10/2013 | France | Hack of the Elysée | https://bit.ly/2Th6IXX |
| 10/2013 | France | Surveillance of many mobile phones | https://bit.ly/3wsDcwp |
| 12/2018 | Lebanon | Access to Lebanses mobile phones to issue warning messages | https://bit.ly/3bNbVNr |
| 11/2019 | India | Hack of opposition mobile phones during elections using NSO Pegasus | https://bit.ly/3473PuV |
| 12/2019 | Pakistan | Hack of executives mobile phones using NSO Pegasus. India suspected | https://bit.ly/3fJLN7r |
| 05/2020 | Iran | Hack of port to disrupt operations | https://nyti.ms/2SimaCC |
| 06/2020 | Morocco | Hack of opponents mobile phones using NSO Pegasus | https://bit.ly/2Rxuy15 |
| 12/2020 | Al Jazeera | Hack of journalists mobile phones using NSO Pegasus | https://bit.ly/3feTOSQ |
| 04/2021 | Iran | Hack of nuclear facility | https://bit.ly/3ubWhla |
We can conclude that Israel has some core competencies and advantages :
- Control of Web Infrastructure of Palestine
- Expertise in SIGINT
- Expertise in surveillance tools (PC, mobile phones, social networks,…)
- Capacity to design advanced malware and transplant these malware in remote locations
- Strong cooperation between secret services and cyber ecosystem
Israel has for sure used these competencies to fight against Hamas during the recent operation Wall Guardian : https://bit.ly/34aZCq0
Attacks against Israel
Israel is also the target of frequent cyber attacks. Here below a summary of some known attacks :
| Date | Initiator | Summary | Link |
|---|---|---|---|
| 11/2003 | Israeli | Israeli citizen defacing the Mossad website | https://bit.ly/3wtQIjm |
| 03/2012 | Gaza | Web sites defaced by Gaza Hacker Team | https://bit.ly/3bM1r0G |
| 08/2015 | Gaza | Intelligence gathering with malware | https://bit.ly/3uimnmq |
| 02/2016 | Hezbollah | Security camera system breach | https://bit.ly/2QNB3MO |
| 05/2017 | Gaza | Molerats threat group | https://bit.ly/3fAxt0O |
| 07/2018 | Hamas | Hack soldiers through world cup phone app | https://bit.ly/3yAU0mG |
| 08/2018 | Hamas | Attempt to hack Israelis with fake rocket warning app | https://bit.ly/3bOJxum |
| 03/2019 | Iran | Hack of the mobile phone of PM candidate Benny Gantz | https://bit.ly/3wqi4XK |
| 05/2019 | Hamas | Eurovision hack | https://bit.ly/2Te33Kn |
| 02/2020 | Unknown | Massive data leak of Israeli | https://bit.ly/2QK5G5D |
| 02/2020 | Hamas | Soldiers attracted to download a malicious app with fake photos of women | https://bit.ly/3wsbHTJ |
| 05/2020 | Iran | Attempted cyber attack on water and sewage system | https://bit.ly/3wrsshL |
| 10/2020 | Unknown | Hack against executives of the Crypto industry | https://bit.ly/2RwKssx |
| 12/2020 | Iran | Breach of Israel Aerospace industry | https://bit.ly/3viwEjK |
| 01/20201 | Hezbollah | Malware attack over industries and countries | https://bit.ly/34aAGz2 |
| 05/2021 | Iran | Breach into H&M computers | https://bit.ly/3oQ5aji |
We can conclude that despite its strong cyber competence, Israel has some hard time blocking hackers and preventing damages
Let’s keep in mind that Israel is highly exposed, as many Israeli have access to the Internet, are using social networks and mobile phones
It is very difficult to stop such attacks. We will surely see more data breaches, ransomware, malicious apps targeting Israeli
Conclusion
Let’s conclude this article. Israel has a unique and complexe strategic position, and Cyber has long been at the heart of Israel defense and attack tactics. It shall continue !
Here is a prospective study, highlighting what could be facing Israel in the next two decades : https://brook.gs/3eNHeZ5
Here below an excerpt :

Israel will have to continue defending the country and the people, keeping a technological advantage
The Information Warfare will be important, and Israel will use its cyber capabilities to inform, fight fake news, deter, and more
They had better do it, and do it well, as the opponents of Israel are also using Internet for their needs. International opinions will be strongly influenced by the right propaganda
In my opinion, Israel can lead the information warfare, not only because of technology, but also with an Ethical behaviour. This will probably be key to persuade international opinions that Israel does the right things and takes legitimate actions
