Here’s a trend setting prediction from Gartner that “says it all”…

I’ll focus in this article about what is a cyber security rating, how it is made, and what is the business model of cyber-rating agencies. I will also test by myself one sample, using similar techniques to the ones used by cyber agencies, to put it to the test
Cyber security rating is an index, a score (such as points, a letter,…), similar in nature to the financial rating or other available ratings in the markets (consumer credit,…). Here’s how Bitsight, the US cyber security rating leader, positions himself in comparison to others

To build the score, the agencies are collecting a bunch of data for each companies they intend to score. The datas are publicly available, and the analysis is not intrusive, but require a degree of automation to be efficient and reliable
As a starting point, the agency is taking the company name, it’s brand name and the corresponding domain names, public IP adresses, web sites, to search for the data. The point is to identify suspicious activities, traces of compromissions, basic configuration problems. Typically, the agency is going to look for two sources of informations : “fact” based, and “event” based

Facts, or factual data, will be taken from direct queries of the domain, while events, or online reputation, will be derived from threat intelligence sources, data leaks, darknets, hacking forums,…. Bitsight provides the following summary of parameters used for the rating
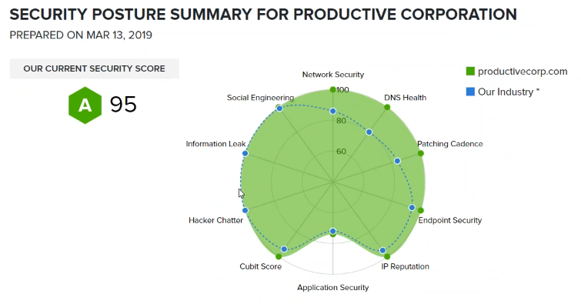
Productive Corporation, another US agency, provides a more detailed view

However, no rating agency is releasing it’s sources of informations, and core algorithm to calculate and generate the rating. Nevertheless, since the sources are said to be public, I’ll provide below potential actual sources used by rating agencies
SSL encryption : https://www.ssllabs.com/ssltest/
This is a well known site from Qualys, performing a deep analysis of the configuration of any SSL web server
Website exposure and security : https://www.immuniweb.com/websec/, https://pentest-tools.com/website-vulnerability-scanning/website-scanner
You will get subdomain discovery, GDPR/PCI DSS configuration, HTTP headers/cookies/third-party security analysis, infrastructure, and more
You can check the DNS records using this tool https://www.nslookup.io/ to find the SOA (Start Of Authority), the MX (email server) and more. Thanks @Ruurtjan for developing this tool
Note : if you would like to understand the limitations of such tools, I’ve found a good blog post about Web application finger printing and limitations at https://anantshri.info/articles/web_app_finger_printing.html#case_whatweb
Site Reputation : https://talosintelligence.com/reputation_center
Talos’ IP and Domain Data Center is one of the world’s most comprehensive real-time threat detection network. It will pop up an alert in case a domain, an IP, is known to be a threat, whatever it’s form (DDOS, spam,…)
E-mail reputation : https://senderscore.org/
From a given IP or domain used to send email, you well get an overall assessment of email reliability (spam, blacklist,…)
DNSSEC, SPF : https://gf.dev/dnssec-test
With this tool, you can check the basic configuration of Domain Name System Security Extensions, and Sender Policy Framework
DMARC : https://mxtoolbox.com/dmarc.aspx
The DMARC Record Lookup / DMARC Check is a diagnostic tool that will parse the DMARC Record for the queried domain name, display the DMARC Record, and run a series of diagnostic checks against the record. Domain-based Message Authentication, Reporting, and Conformance (DMARC) is a mechanism for policy distribution by which an organization that is the originator of an email can communicate domain-level policies and preferences for message validation, disposition, and reporting.
Pwn : https://haveibeenpwned.com/
This is the famous site from Troy Hunt, a security blogger. You can check if the evaluated company E-mail has been pwned
Data leak : https://cracked.to/Forum-Databases
From these cracking and hacking forums, you may be able to find some leaked and hacked data. There are many sources like this on the Dark Web (I will write an article about this one day…)
Reporting
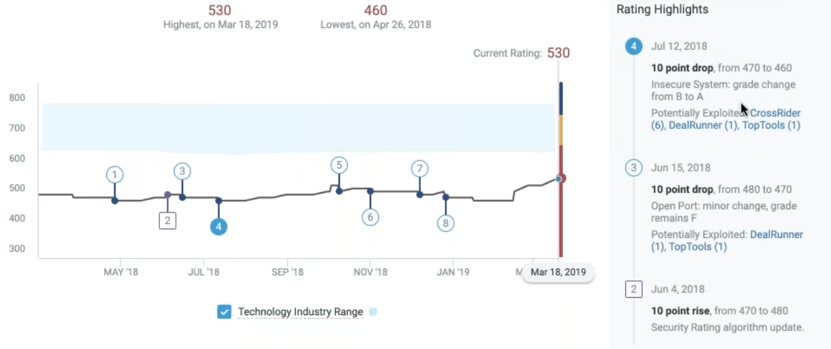
Most rating agencies have been able to develop a user friendly, business intelligence style, reporting system. Once can easily display charts of historical data such as this
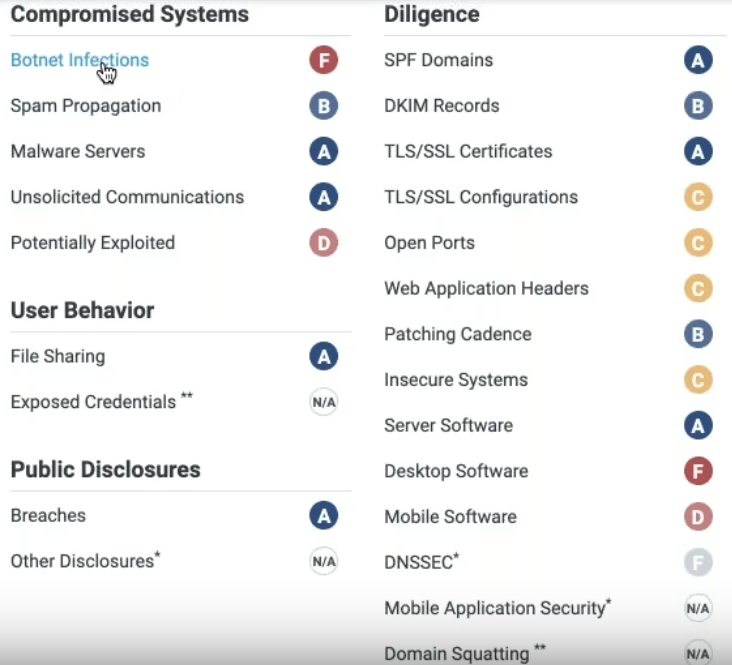
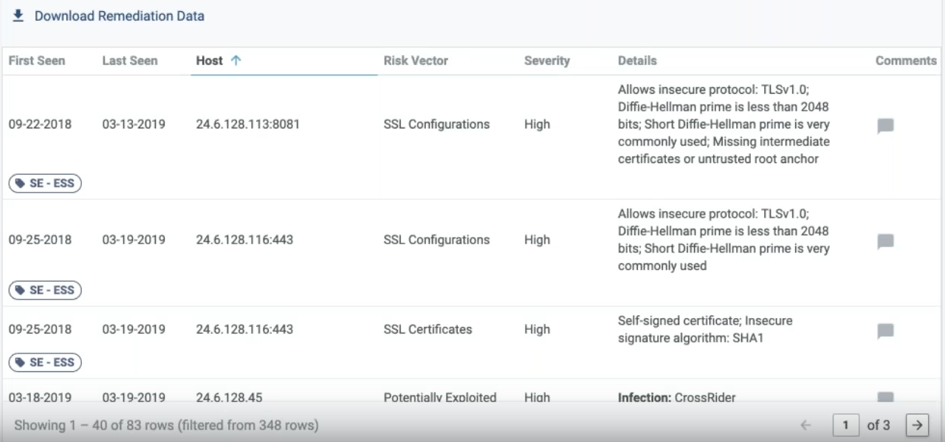
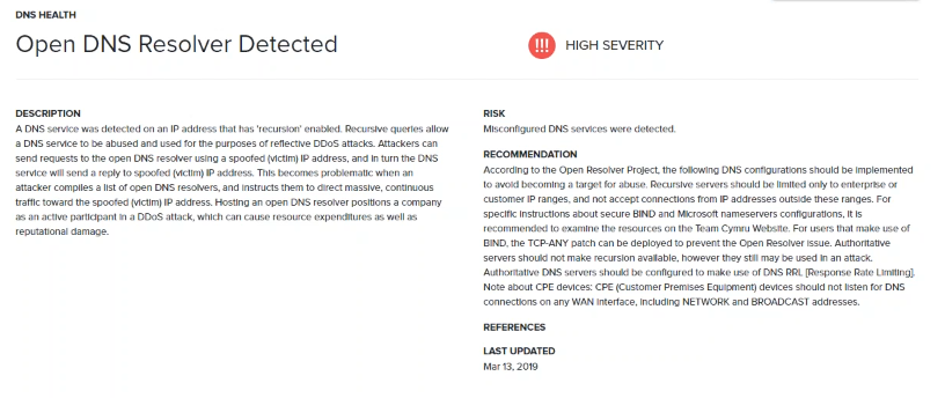
Also, one can access to the detailed risk vectors, observables, together with recommended mitigation actions
Last but not least, you can get a summary of the overall security posture, by area
API
It’s critical for the rating agency, to ensure an efficient access to datas, to integrate in its platform, the relevant API. Here is an example of an API documentation of an SSL scanning tool from Immuniweb, necessary to import the live data https://www.immuniweb.com/ssl/API_documentation.pdf
Is a cyber rating relevant to evaluate the cybersecurity of a company ?
Although there are many critics as the rating looks superfical, just scratching the external surface of a company cyberdefense, I consider it is highly relevant, as a good rating will take into account the speed with which a company is updating it’s key technical assets, has little to none signs of compromissions, and has a solid configuration policy of it’s exposed assets. This would denote and correlate with good internal policies regarding cybersecurity. Other way round, a loose policy will be immediately visible to the external world with much probably low scores on each rated items
We have seen in the past years, that data leaks, compromissions, are often due to third parties, who have little cyber security awareness, leading big companies to suffer a major security breach. Therefore it will be even more critical to assess your suppliers, your partners, your IT vendors and so on. Panorays sums it up…

What’s remarkable is how many organizations don’t make an effort to view their public online assets as the rest of the world sees them — until it’s too late…
However, a rating is not sufficient to thoroughly assess the cybersecurity position of a given company. It would require security scans, pentest, organization audit, and more
Who are the main actors ?
US based agencies are the biggest in size and the more mature actors
- Bitsight (USA), which is the leader, having managed to attract investors and raise capital over the years
- UpGuard (USA)
- Productive Corporation – Security ScoreCard (USA) – The rating agency Moody’s has invested here
- Panorays (Israël) – startup
- Cyrating (France) – startup
- Provadys (France)
Business model considerations
By nature, cyber rating agencies main goal is to make money from selling ratings to Companies. They are going to seek a lean internal process, to rate as many companies as possible. Therefore a key success factor is to have an automatized and accurate rating process, simple and quick, without impact on the rated companies
Since the rating is based on facts but also on events, it is critical for the rating agency to have access to good and comprehensive sources of informations, such as historical data regarding security incidents and Threat Intelligence. Therefore, US based companies certainly have a competitive edge as bank of datas are more widely available (CERT-US, ITRC,…) on such a big and cyber regulated country as the USA, while there are much more leading Threat Intelligence companies here
Bitsight has its own Threat Intelligence subsidiary which collects lots of data to support the rating process (see below)
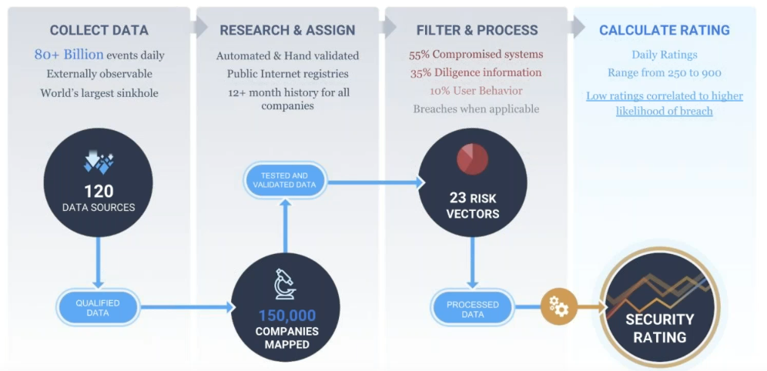
As we can see, the key success factor, again, is to be able to exploit in a smart way, a lot of data scatered all over the place, thanks to a lot of connectors, API, big data technology
Another key success factor is the ability to create its own “market place” of company ratings, and attract companies to subscribe to the service. Even with a very efficient rating process, the rating agency will be nothing if they can’t attract many companies to subscribe to their “market place” and be part of the same community, where each one can compare and benchmark it’s rating to the others. A critical mass is therefore necessary with a wide portfolio of rated companies, and the rating agency had better reach it very quickly, otherwise failure is to be expected
Several rating agencies are proposing, beyond the basic rating, additional services for a premium (on premise assessment by an expert, on site audit,…), to make the rating more accurate and actionable and be able to sell more service and increase customer retention
Pricing
Rating agencies have pricing models whereby the price of a single rating will typically be in the thousands dollars, while you would spend a few hundred dollars per rating to buy thousands. It looks pretty expensive…but rating agencies advocate that this is going to be a fraction of the cost of a cyber audit
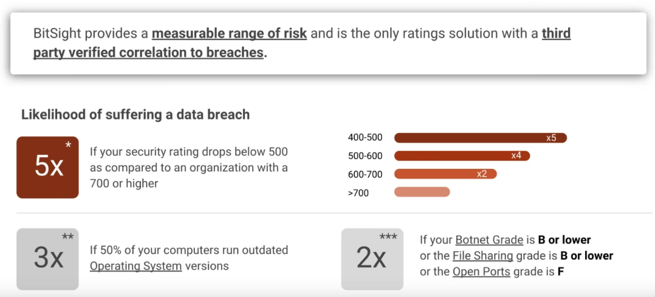
Correlation to data breaches
Bitsight claims there is a proven correlation between cyber ratings and data breaches. They provide a range matrix as follows
The CEO point of view
Unless you are very literate in cybersecurity, it is most of the time very hard to understand for a novice. Cyber rating provides the ability to translate complex cybersecurity issues into simple business context, allowing to simplify the approach for Management teams, economical actors, therefore providing decision makers a good way to anticipate risks and make decisions
Cyber rating and sovereignty
That’s a key issue as the growth of these agencies, mainly US based, gathering millions of data for their ratings, will allow them to handle a lot of sensitive informations regarding non US companies. Beyond external and public data, companies will be probably encouraged to provide more internal datas to support a good rating, thereby exposing them. Cyber rating could therefore be another tool to a US commercial domination
Let’s practice !
I’m not going to build a rating as it would be a complex endeavour, but I’m going to gather as much public data about a given domain, an evaluate how it’s cybersecurity posture look like, thus taking the first steps to a rating
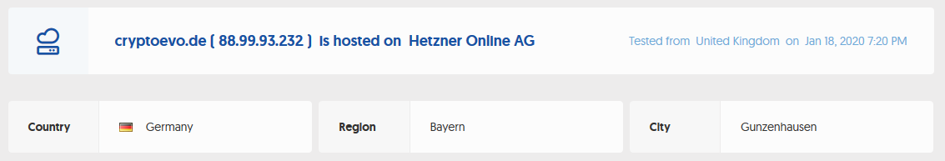
I’ve chosen the domain https://cryptoevo.de/, a German based cryptocurrency community. I would expect such a domain to be exemplary, as cryptocurrencies are supposed to back secure financial transactions…(although there has been many security flaws in cryptoasset marketplaces in the recent years). Here is a Whois snapshot
In terms of technology, this website runs the following server, programs, API and frameworks
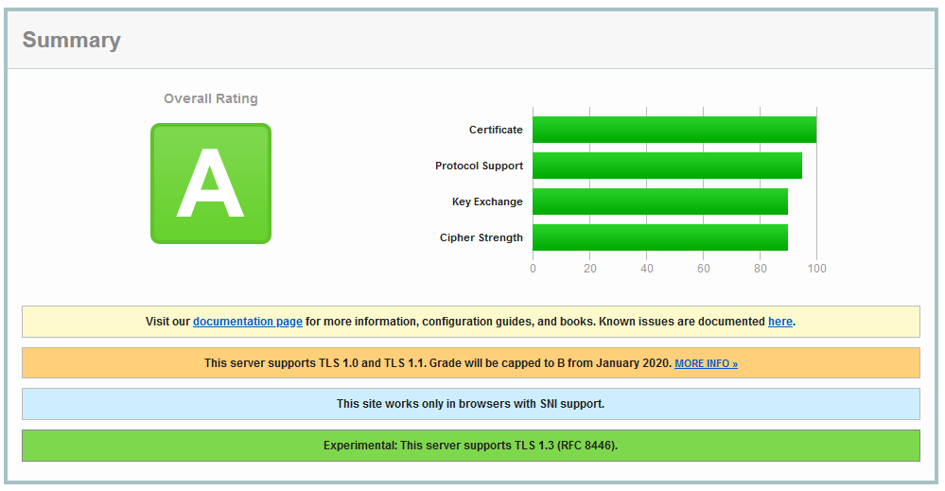
SSL Labs / TLS configuration ( https://www.ssllabs.com/sslt )
The domain gets the highest rating “A”. Notice that the website still supports TLS1.0 – for maximum compatibility -, which is going to be deprecated this January 2020
Website exposure and security
Here is the rating out of https://www.immuniweb.com

and this is the one from https://pentest-tools.com/website-vulnerability-scanning/website-scanner
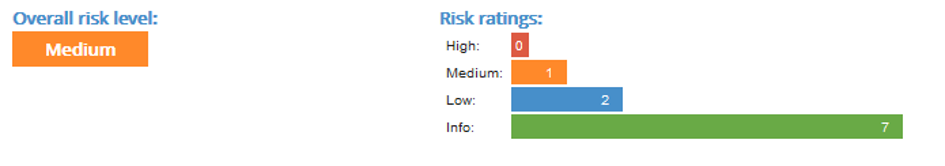
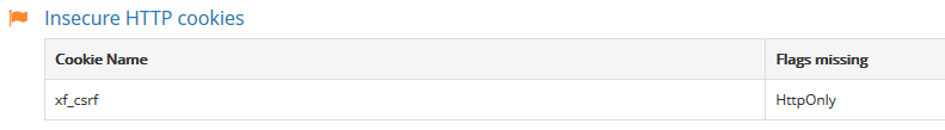
There are a number of additional configurations available to increase the rating to the maximum possible
Missing HttpOnly flag on cookies : when a cookie doesn’t have an HttpOnly flag, it can be accessed through JavaScript, which means that an XSS could lead to cookies being stolen. These cookies include, but are not limited to, CSRF tokens and client sessions that can make it easier to achieve account/session takeover. A configuration line on the server can help solve this (see more details here https://support.detectify.com/customer/portal/articles/1969826-missing-httponly-flag-on-cookies)
The HTTP X -XSS-Protection response header is a feature of Internet Explorer, Chrome and Safari that stops pages from loading when they detect reflected cross-site scripting (XSS) attacks. Although these protections are largely unnecessary in modern browsers when sites implement a strong Content Security Policy that disables the use of inline JavaScript ('unsafe-inline'), they can still provide protections for users of older web browsers that don’t yet support Content Security Policy
Strict Transport Security not enforced : the application fails to prevent users from connecting to it over unencrypted connections. An attacker able to modify a legitimate user’s network traffic could bypass the application’s use of SSL/TLS encryption, and use the application as a platform for attacks against its users. This attack is performed by rewriting HTTPS links as HTTP, so that if a targeted user follows a link to the site from an HTTP page, their browser never attempts to use an encrypted connection
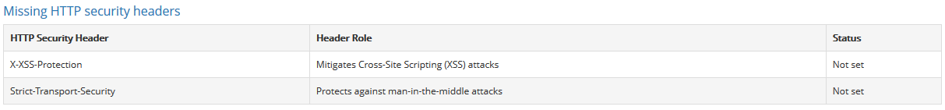
Content Security Policy not enforced : Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross Site Scripting (XSS) and data injection attacks. These attacks are used for everything from data theft to site defacement to distribution of malware

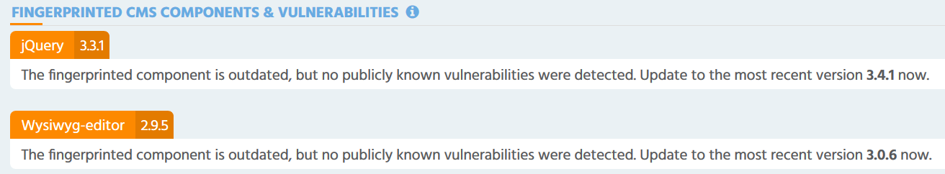
In addition, the Javascript library jQuery and the HTML framework editor Wysiwyg deserve an update. However, one should balance the pros and cons before doing this (see this blog for more explanatations https://www.sjoerdlangkemper.nl/2018/10/24/should-you-update-jquery/)
Site Reputation
There is nothing to be found on https://talosintelligence.com/reputation_center regarding the domain cryptoevo.de (this is what I expected from such a site)
E-mail reputation
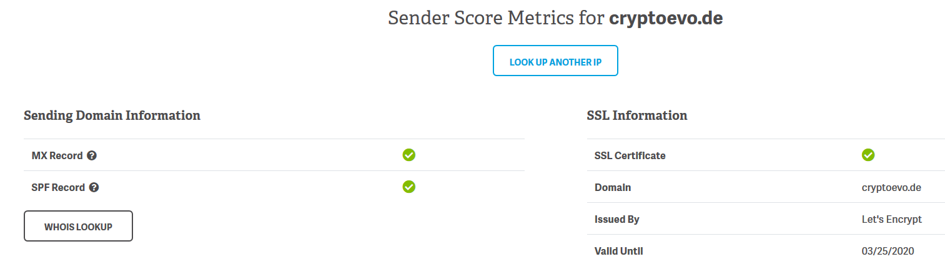
Here is the result with the domain cryptoevo.de from https://senderscore.org/, all is clear
DNSSEC
From https://gf.dev/dnssec-te , we learn that the domain cryptoevo.de has not configured DNSSEC. Is that an issue ?
DNSSEC adds two important features to the DNS protocol:
- Data origin authentication allows a resolver to cryptographically verify that the data it received actually came from the zone where it believes the data originated
- Data integrity protection allows the resolver to know that the data hasn’t been modified in transit since it was originally signed by the zone owner with the zone’s private key
In order for the Internet to have widespread security, DNSSEC needs to be widely deployed. DNSSEC is not automatic : right now it needs to be specifically enabled by network operators at their recursive resolvers and also by domain name owners at their zone’s authoritative servers
Therefore it’s recommended to implement DNSSEC
SPF
It’s Ok as shown by the online test https://gf.dev/spf-record-test
Conclusion : overall, the results obtained on the domain cryptoevo.de give us an overall good situation. There are some potential improvements on the web configuration although these are probably due to compatibility requirements. I would still recommend actions to be taken. DNSSEC could be configured without major difficulty. In terms of rating, such a site would get quite a high score, but still fall below the best ones
Overall, cyber security rating is still quite a new business. It’s certainly due to grow and expand as more regulations are introduced and customer monitoring requirements get higher. Rating agencies will compete even more to build an attractive marketplace and “occupy the web”. A rating agency had better be unavoidable as it’s probable only 2 or 3 will be major players at the end of the day

Thanks for the shoutout to nslookup.io ! I’ve been building it in the weekends for the past year, slowly improving it over time. For now, it only contains DNS specific tools, but if you’d like to see any other tools added, you can reach me over Twitter DM 🙂
Hi Ruurtjan, thanks for your feedback 🙂
Your site https://www.nslookup.io/ is really a good endeavour, thanks for sharing it on my blog !