In this article, I will scratch the surface of the Belarus web infrastructure, using some basic footprinting techniques
Belarus is a country in Eastern Europe. It is bordered by Russia to the east and northeast, Ukraine to the south, Poland to the west, and Lithuania and Latvia to the northwest. It has a population of 9.5 million. Minsk is the capital and largest city
Belarus had a complex history in the last century, changing hands at various times, to the Grand Duchy of Lithuania, the Polish–Lithuanian Commonwealth, and the Russian Empire. In the aftermath of the Russian Revolution in 1917, the Byelorussian SSR (Soviet Socialist Republic) became a founding constituent republic of the Soviet Union in 1922
After the Polish-Soviet War, Belarus lost almost half of its territory to Poland. Much of the borders of Belarus took their modern shape in 1939, when some lands of the Second Polish Republic were reintegrated into it after the Soviet invasion of Poland
During World War II, military operations devastated Belarus, which lost about a quarter of its population and half of its economic resources
The parliament of the republic proclaimed the sovereignty of Belarus in July 1990, and during the dissolution of the Soviet Union, Belarus declared independence in August 1991. However, Belarus kept strong ties with Russia

Following the adoption of a new constitution in 1994, Alexander Lukashenko was elected Belarus’s first president in the country’s first and only free election post-independence, serving as president ever since. Lukashenko heads an authoritarian government with a poor human rights record due to widespread abuses
Internet infrastructure
Let’s start a quick review about Internet cables providing the Internet to Belarus
The first one is the Transit Europe Asia (TEA) network, which is an international transit fiber-optic cable line passing trough Russia, and linking European countries with Asia. TEA has transmission routes on Rostelecom (Russian National Telecommunication Company : https://bit.ly/3Vwy4Vy) core networks, with extensions to Belarus
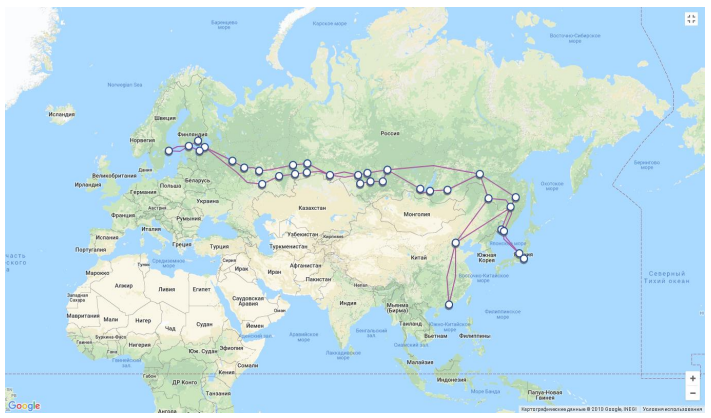
A second one is TransTeleCom (TTK), which is one of the leading Telecom operators in Russia. TTK has a partnership with the Russian Railways (https://bit.ly/3EHJv6I)
TTK is operating a large fiber-optic backbone digital communication network, which is laid along the railways of Russia and has many access points in all densely populated regions of the country, connecting the eastern and western borders of the Russian Federation
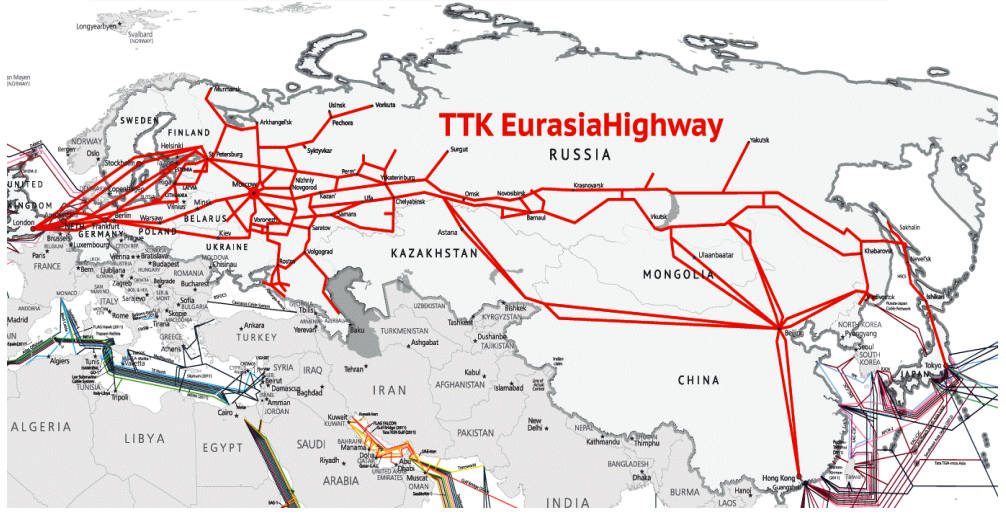
TTK Eurasia Highway has connections with communication networks of all neighboring countries with Russia, including Belarus, and is an optimal route between Europe and Asia
Belarus has its own local companies able to install underground cables and expand the Internet network. One of these is Minskkabel which is specialized in the manufacture of optical cables for an interconnected communication network between Belarus, Russia, and other neighbouring countries

Now, let’s look at the Belarus country code ccTLD – Top Level Domain and corresponding DNS – Domain Name Server root zone
IANA is responsible to assign the operators of top-level domains, such as .com, and maintain their technical and administrative details
We can find the Belarus ccTLD on the IANA website with the .by country code
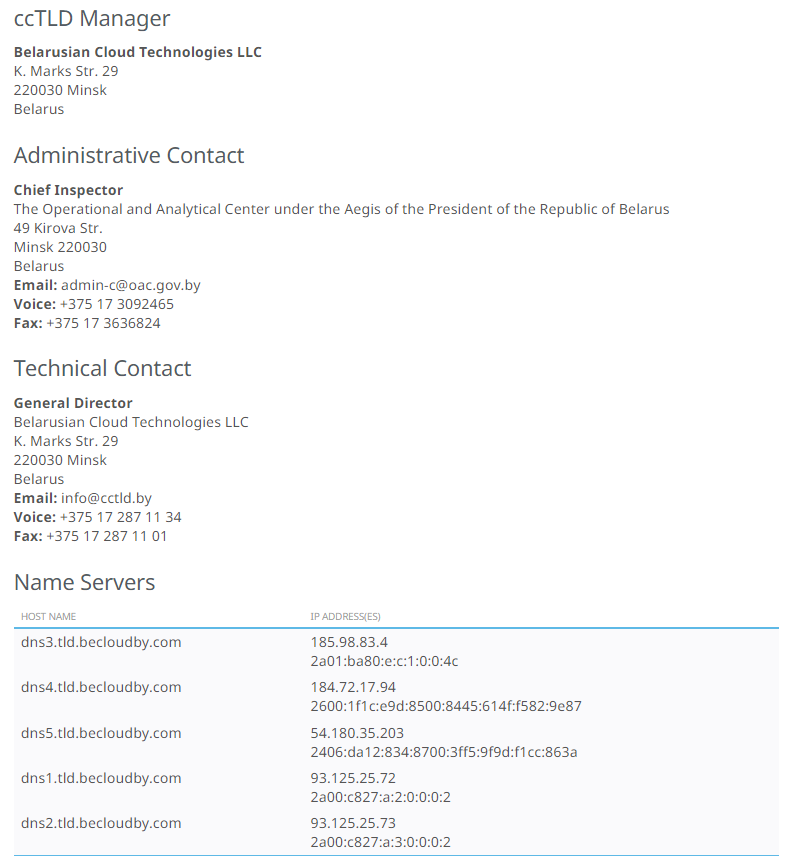
IANA is responsible for determining an appropriate trustee for each ccTLD. Administration and control are then delegated to that trustee, which is responsible for the policies and operation of the domain
In the case of Belarus, it is Belarusian Cloud Technologies LLC (beCloud). According to their website, they describe themselves as the first infrastructure operator in Belarus. Here are some key services operated by beCloud :

In the last years, Belarus has been building a sovereign Cloud ecosystem, mostly with the help of major European, US and Asian companies, such as the ones below. The international sanctions on Belarus and Russia are mainly targeted to specific individuals, and do not block necessarily these partnerships and exchange of technology

Taking into account the capital cost of construction of a network and the limited population of Belarus, it was decided to create one single infrastructure operator. beCloud operates several datacenters and has a wide network inside Belarus, and sells the bandwidth to other operators
The chief inspector of the Belarus TLD is the OAC – Operational and Analytical Center
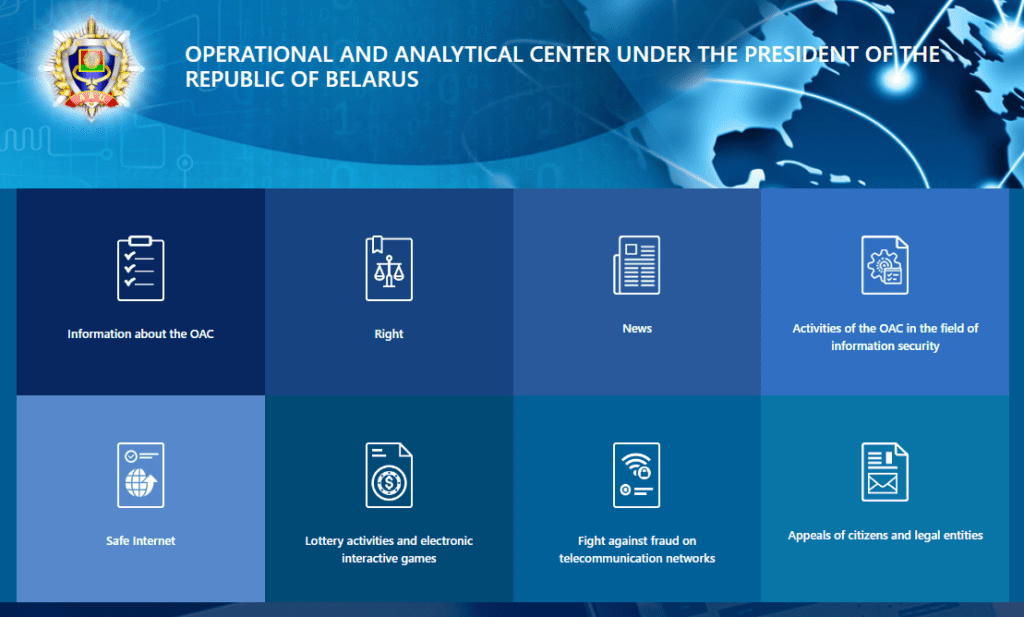
There is much controversy about this agency. A son of Lukashenko had been appointed director some years ago

Here are the main tasks of the OAC
Several agencies are subordinated to the OAC, such as the important National Traffic Exchange Center (NTEC)

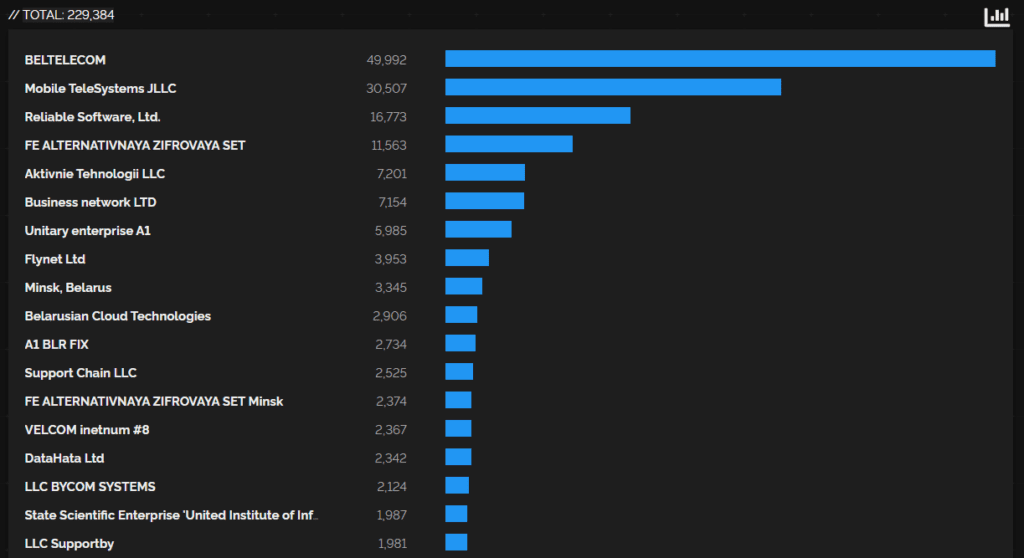
The Ministry of Telecommunications controls all telecommunications originating within the country through its carrier unitary enterprise, Beltelecom
The statistics on Shodan show us the importance of Beltelecom as the main operator of routers and switches accross Belarus
Beltelecom owns all the backbone channels that link to external networks such as the one from Rostelecom in Russia
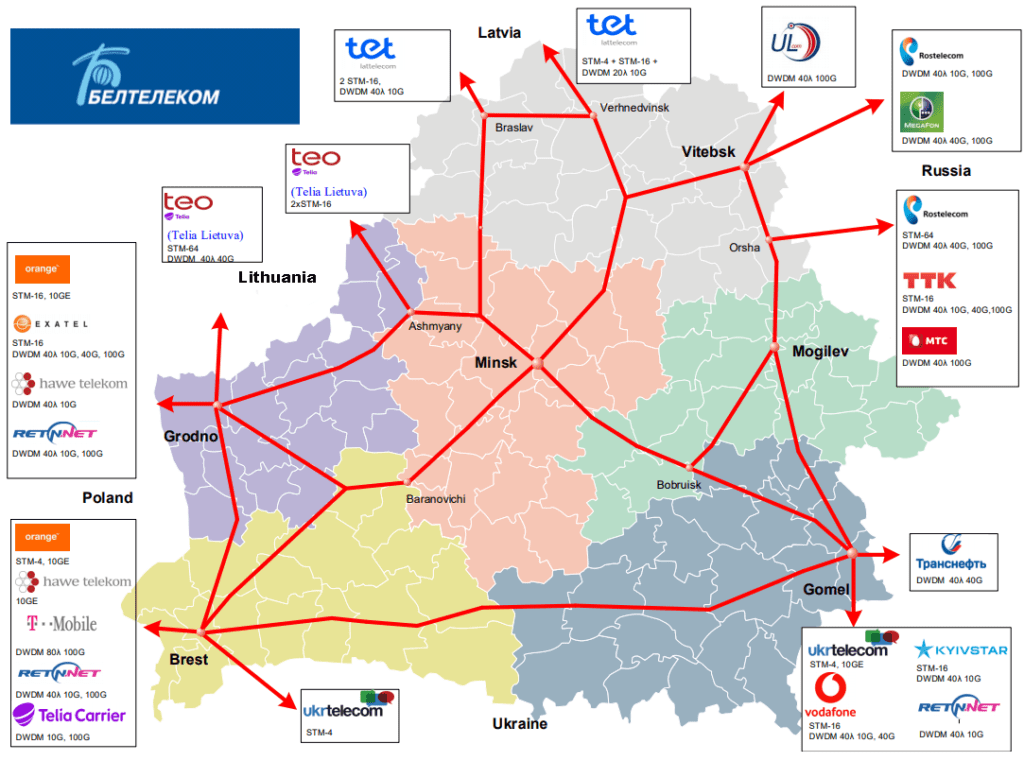
While Beltelecom is in charge of the infrastructure, NTEC is responsible for allowing the access to the international Internet, and grants this service for a fee that is paid by Telecom operators
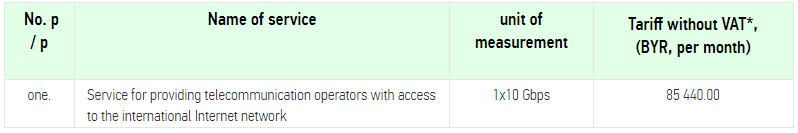
The Belarus authorities can block the internet as they did in August 2020 during the elections turmoil, as you can see on the chart below
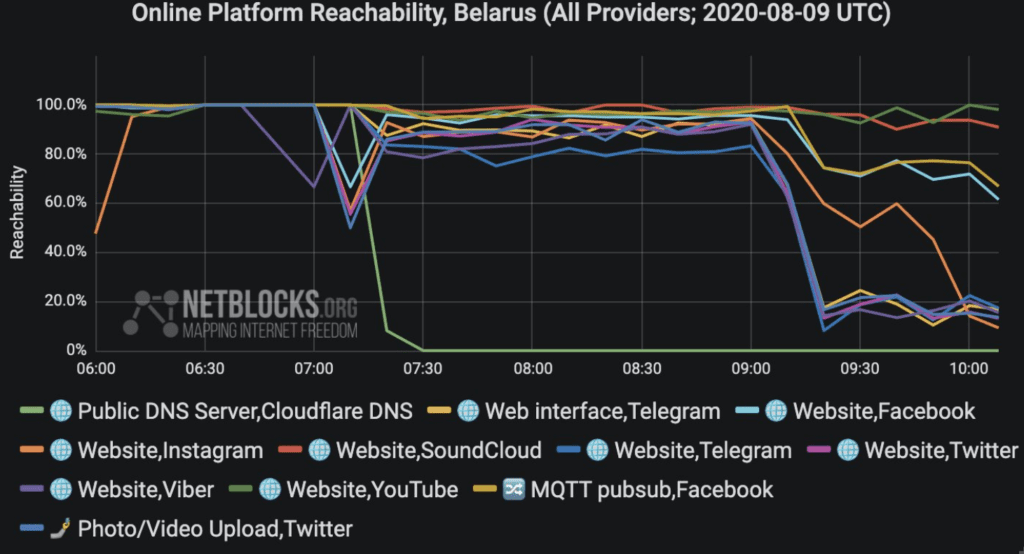
In fact, the American IT company, Sandvine (Procera), had supplied filtering equipment for normal network operations (such as traffic optimization, congestion management, cost efficiency, anti malware…) using a Deep Packet Inspection (DPI) process, with the help of resident engineers

The Sandvine equipement had been used by Belarus authorities to block legitimate traffic and switch off the Internet
Further to this, Sandvine decided to terminate the contract with Belarus : https://bit.ly/3VxIfcg
In Belarus, the state body BelGIE is responsible to manage the list of restricted IPs and traffic : https://belgie.by/en/home
Let’s check the Name Servers provided for the .by Belarus ccTLD (remind that a lot of domains in the world have multiple nameservers to increase reliability)
| Name Server | IP | Identity | Location | Traceroute |
|---|---|---|---|---|
| dns1.tld.becloudby.com | 93.125.25.72 | beCloud | Belarus | UTG RETN NTEC beCloud |
| dns2.tld.becloudby.com | 93.125.25.73 | beCloud | Belarus | UTG RETN NTEC beCloud |
| dns3.tld.becloudby.com | 185.98.83.4 | Dataline | Russia | UTG RETN Dataline |
| dns4.tld.becloudby.com | 184.72.17.94 | Amazon AWS | USA | AWS |
| dns5.tld.becloudby.com | 54.180.35.203 | Amazon Technologies | USA | AWS |
The main Name Servers n°1 and n°2 are hosted by beCloud in Belarus
Ukrainian Telecommunications Group (UTG) is a major Ukrainian operator, enabling some part of the traffic towards Belarus. RETN is a major international network operator headquartered in UK and managing Eurasian cables going through Ukraine and Russia
The National Traffic Exchange Center (NTEC) has been seen above already, and we can confirm that the NTEC is at the center of the Internet communication from abroad Belarus
Dataline is an IT company located in Russia with cloud capabilities. It’s interesting to see that some backup Belarus Name Servers are hosted in Russia (Dataline) and USA (AWS)
Here below are the main ISP (Internet Service Providers) of Belarus :
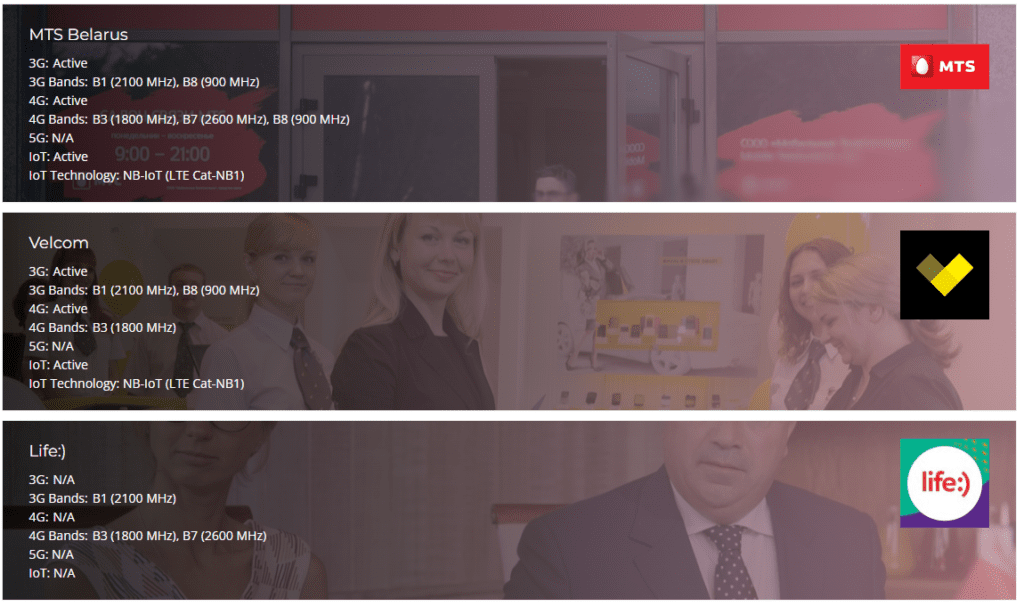
Internet usage in Belarus is about 82%, as we can find here : https://bit.ly/3CjOKqz. It is similar as the one of France
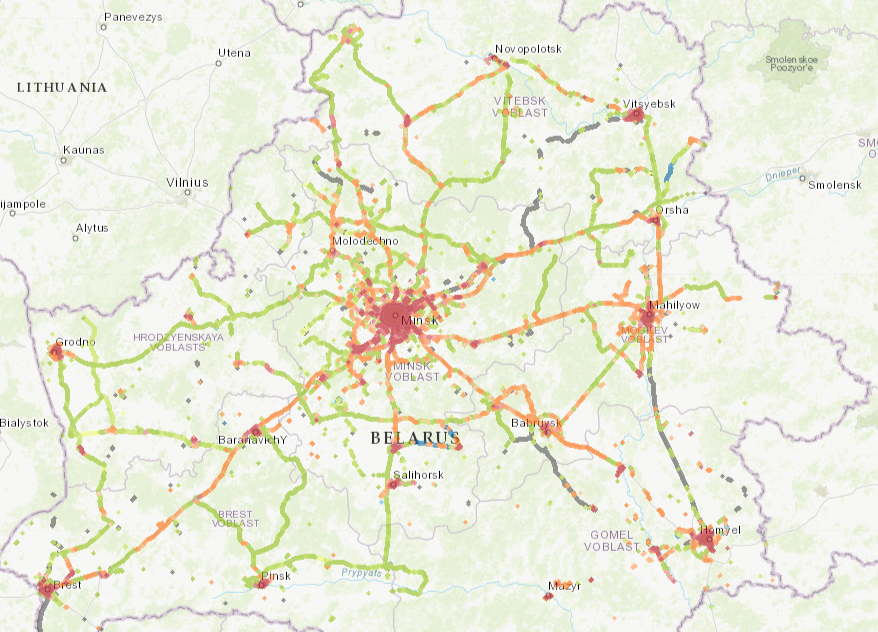
The mobile networks 2G/3G/4G are quite widespread, with a stronger concentration of these networks around major cities
The mobile network 5G is not yet deployed, but activities are on-going to implement this latest standard
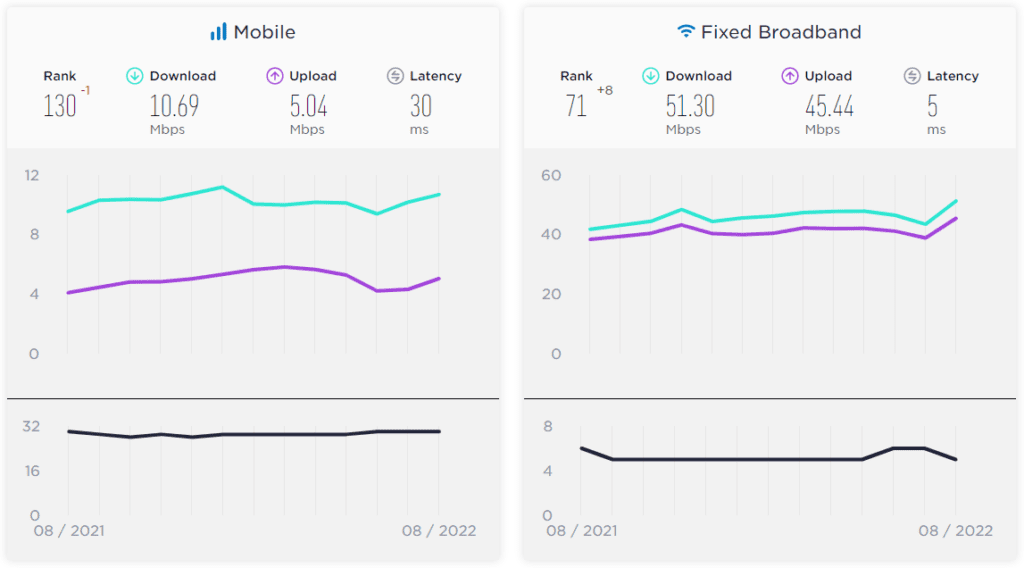
The overall efficiency of the Belarus network is not that great, probably due to a lower coverage in rural areas
Operational and Analytical Center
Let’s go deeper on the OAC – chief inspector of the Belarus TLD – that we have seen above : https://bit.ly/3gVNzGH
First of all, you shall know that the OAC is entitled by Law to restrict internet, in case of threats to National Security : https://bit.ly/3TrZaei
We can use several footprinting and recon tools for that. Let’s go through the findings using some of these tools
urlscan.io : https://bit.ly/3sG0S0m
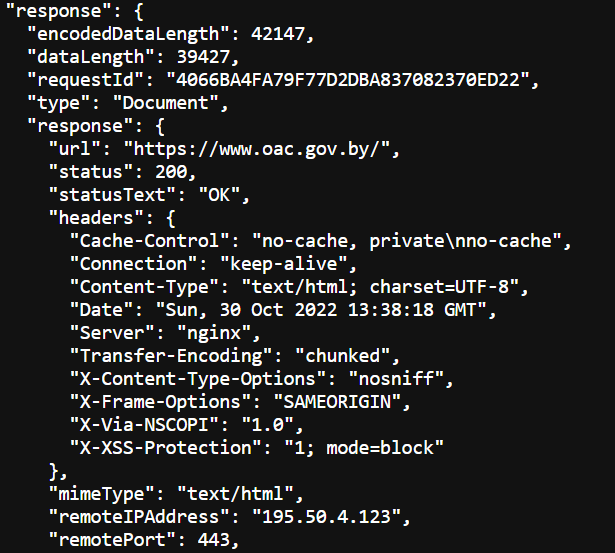
The main IP is 195.50.4.123, located in Minsk, and belongs to BCTBY-AS, which is Belarusian Cloud Technologies, as seen above. The site takes advantage of the Google web tracking technologies, helping the webmaster to perform analytics
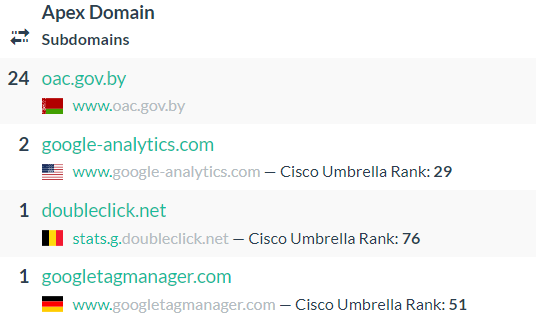
Google Tag Manager (GTM) has been interesting for hackers, as JavaScript can be embedded inside GTM containers and is executed when a browser loads the link to a container : https://bit.ly/3Nihfd4
Doubleclick (https://bit.ly/3sGfQn9) now belongs to Google and is part of the Google Marketing tools
With all these Google technology embedded inside their website, the admin have a good way to track user navigation on their website
We can read the Javascript global variables, here below
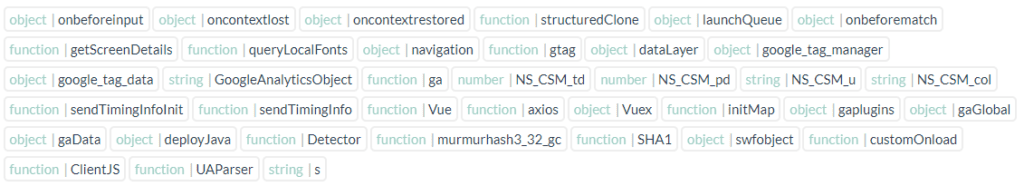
Apart from usual Javascript events, we can confirm the Google analytics and tag manager, already mentioned above. In addition, we find the NS_CSM, which are Citrix variables standing for Client Side Measurement
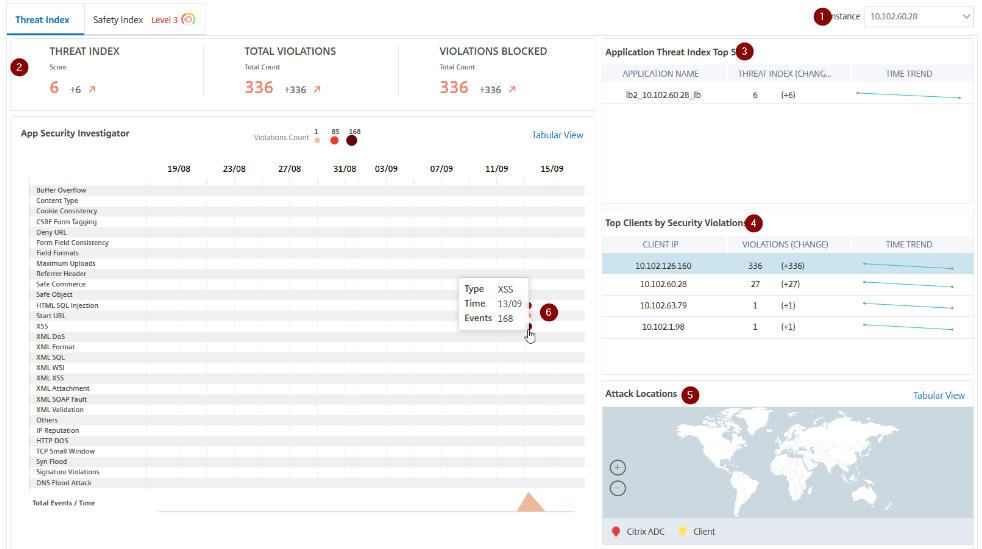
The CSM is the console included in the Citrix WAF (Web Application Firewall), allowing the Admin to monitor any security events. Here a sample screenshot of the interface
Basically, the Citrix WAF works as follows
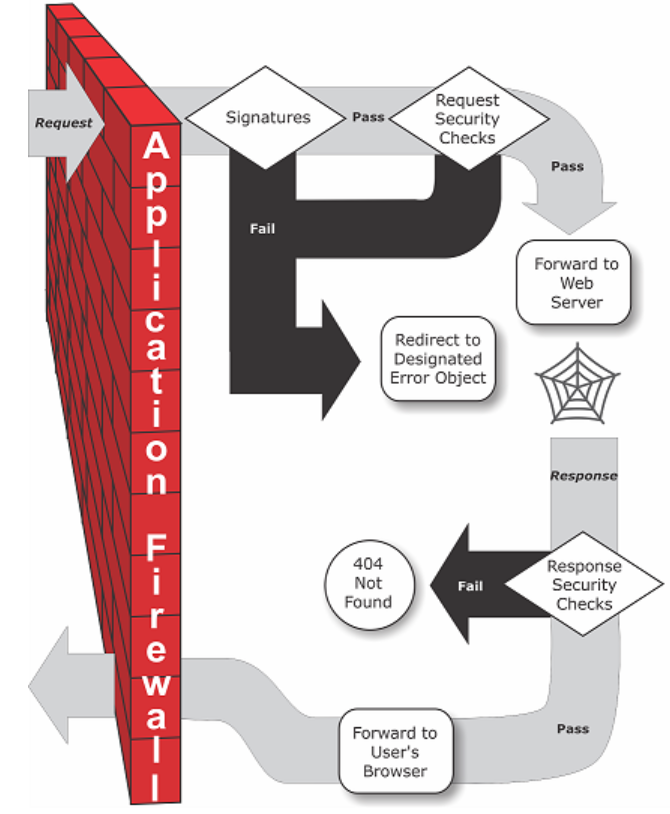
The Citrix WAF is based upon a cookie derived from the web client session : citrix_ns_id
In fact, to maintain the state of the session, the Citrix Web App Firewall generates its own session cookie, and passes it only between the web browser and the Citrix Web Application Firewall, and not to the web server
This will ensure that if any hacker tries to modify the session cookie, the WAF will drop the current session, and the WAF will keep the information of the URLs and forms visited by the client
Here further details about how this Citrix WAF is working : https://bit.ly/3UeJ4p7
Here below all cookies generated by the website :
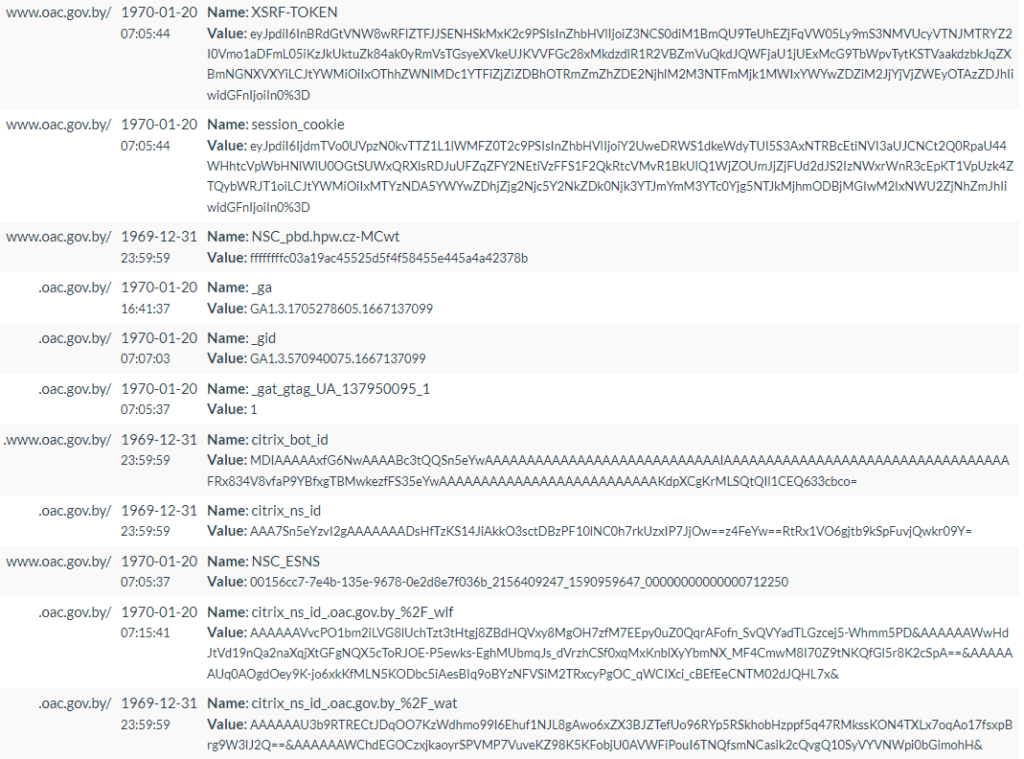
Beyond the citrix_ns_id, we find the citrix_bot_id cookie. This allows the Admin to implement Bot management policies, to block malicious bots : https://bit.ly/3U62hd3
We also see the XSRF token (see here a definition : https://bit.ly/3DIOz9Y), which will help protect against web sites forgeries
Beyond these cookies, we can see some basic web hacking protections

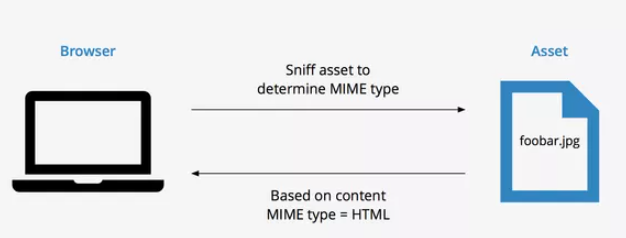
nosniff will help protect against MIME sniffing
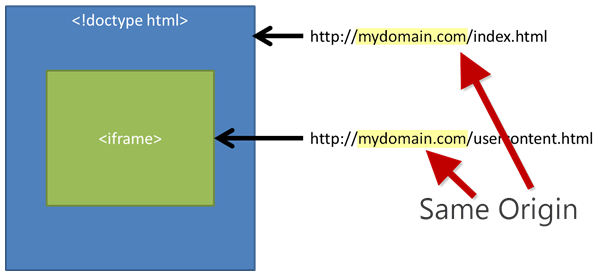
SAMEORIGIN will block iframe inclusions that are not from the same web site origin
1; mode=block will prevent XSS attacks
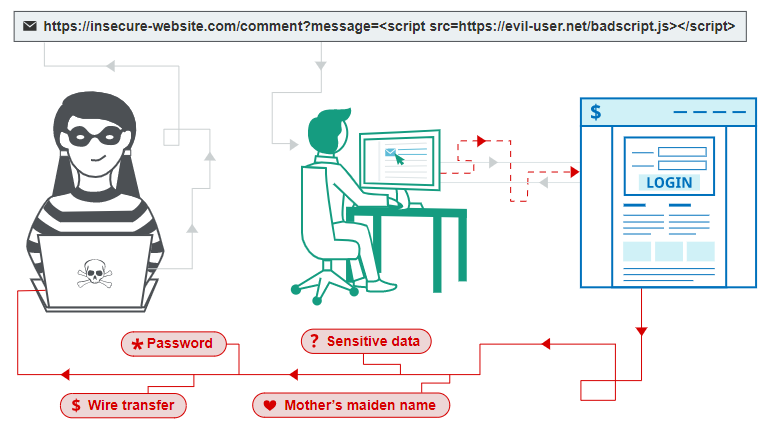
Created for browsers equipped with XSS filters, this non-standard header was intended as a way to control the filtering functionality. Since modern browsers no longer use XSS filtering, this header is now deprecated
We can see that the server is an nginx dealing http requests on the port 443 (as expected)
The website is protected by TLS1.3 and AES256
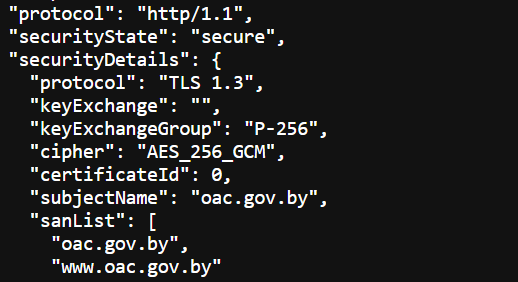
The website has an encryption certificate delivered by Let’s Encrypt
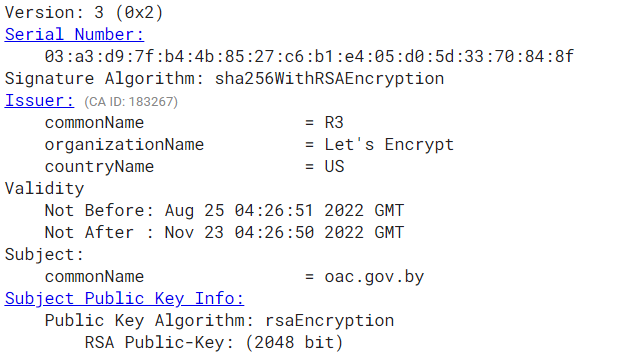
Some people have criticized the fact that Let’s Encrypt provides CERT services to Belarus. But in fact, they validate only that the server has the proven control over the domain name you are visiting. And beyond that, blocking US CERT would probably push Belarus to implement Russian government Certificate of Authority, with all potential risks for the end users : https://bit.ly/3U8wA2i
For the following analysis, check this reminder about DNS here : https://bit.ly/3E0FmtV, and also here : https://bit.ly/3FOpETN
BuiltWith Technology Profiler : https://bit.ly/3hB2JBy
We can find more details about the front-end, mainly the use of Javascript Framework
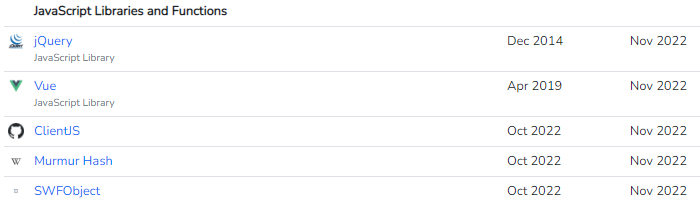
We can also find more details about the back-end server
It seems that the server is probably built using PHP version 7 or above (but this has not been detected since 2021 so it may have been replaced by another)
The server has a Sender Policy Framework (SPF), which enables receiving mail servers to authenticate whether an email message was sent from an authorized mail server (spam and spoofing protection)
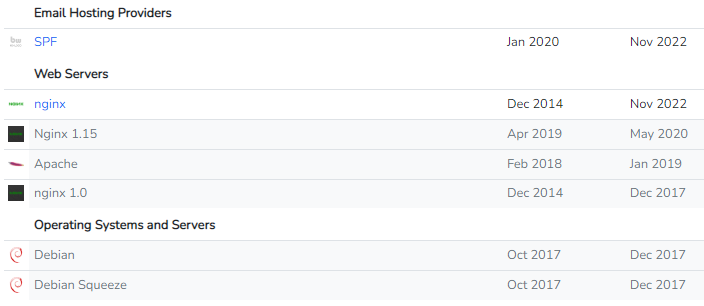
The server is based upon Nginx. Previously, it was based upon Apache (year 2019), and the OS was Debian (year 2017)
We will see below that it’s now probably running FreeBSD (https://bit.ly/3AbZqaf)
whois
Let’s run a whois against the IP address 195.50.4.123
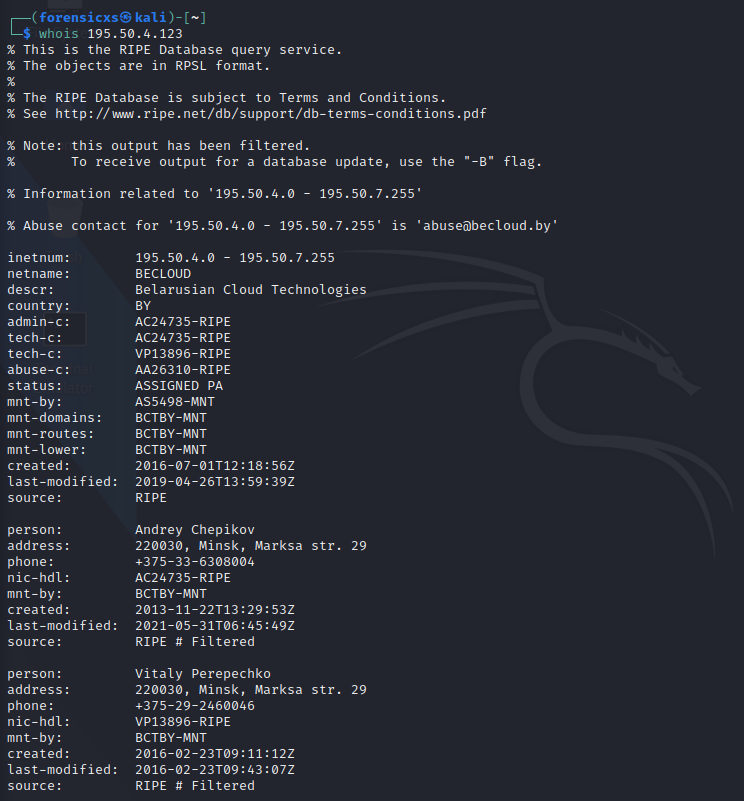
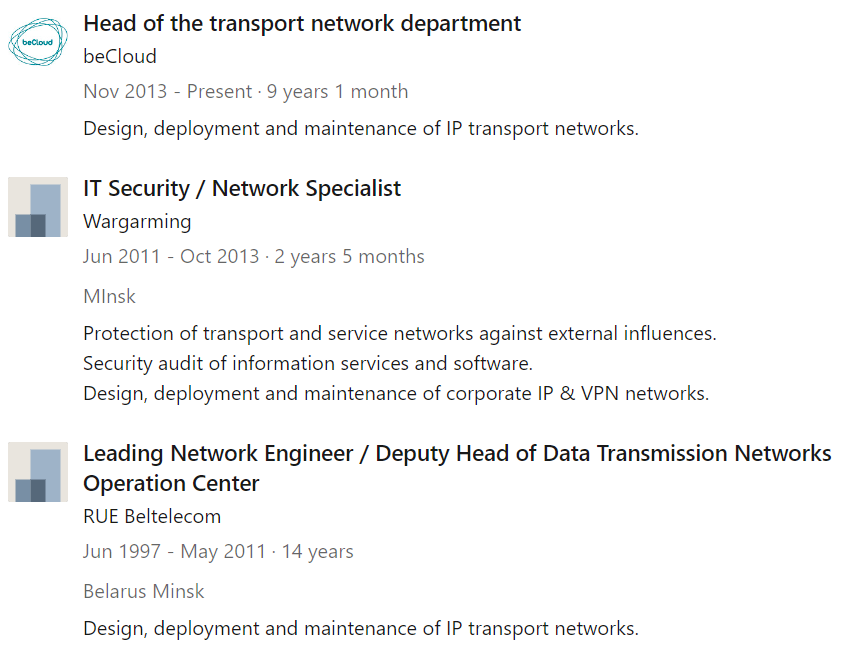
We confirm that the IP is owned by Belarusian Cloud Technologies LLC, as seen above. There are two contact people, that we can cross check on social networks. We find the Linkedin profile of Andrey Chepikov, which states an experience at “protection of networks against external influences“
dnsrecon : https://bit.ly/3sN1txp
This tool does a DNS enumeration. We find the basic informations about the domain oac.gov.by (MX : Mail Server, A : IP address, TXT : Text record). The Sender Policy Framework (SPF) is configured (v=spf1 -all) , so that only this server can send emails on behalf of the domain
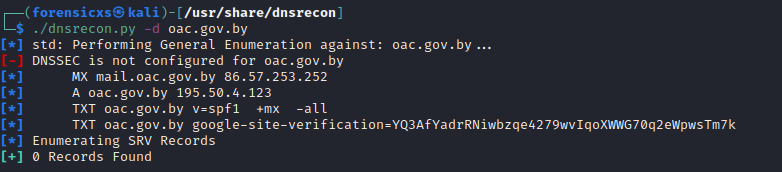
To use Google Analytics, you need to prove that you own the domain. That’s why the Admin added a TXT record to prove this, with google-site-verification. Here is how you can confirm your domain ownership : https://bit.ly/3NE66DR
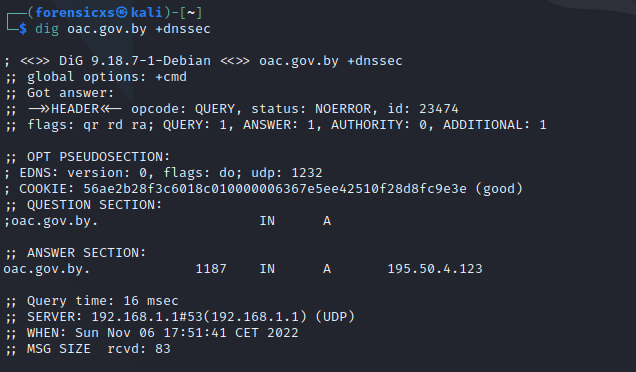
dig : https://bit.ly/3FTE3hT
We can check if the domain has DNSSEC implemented. In this case, it is not enabled
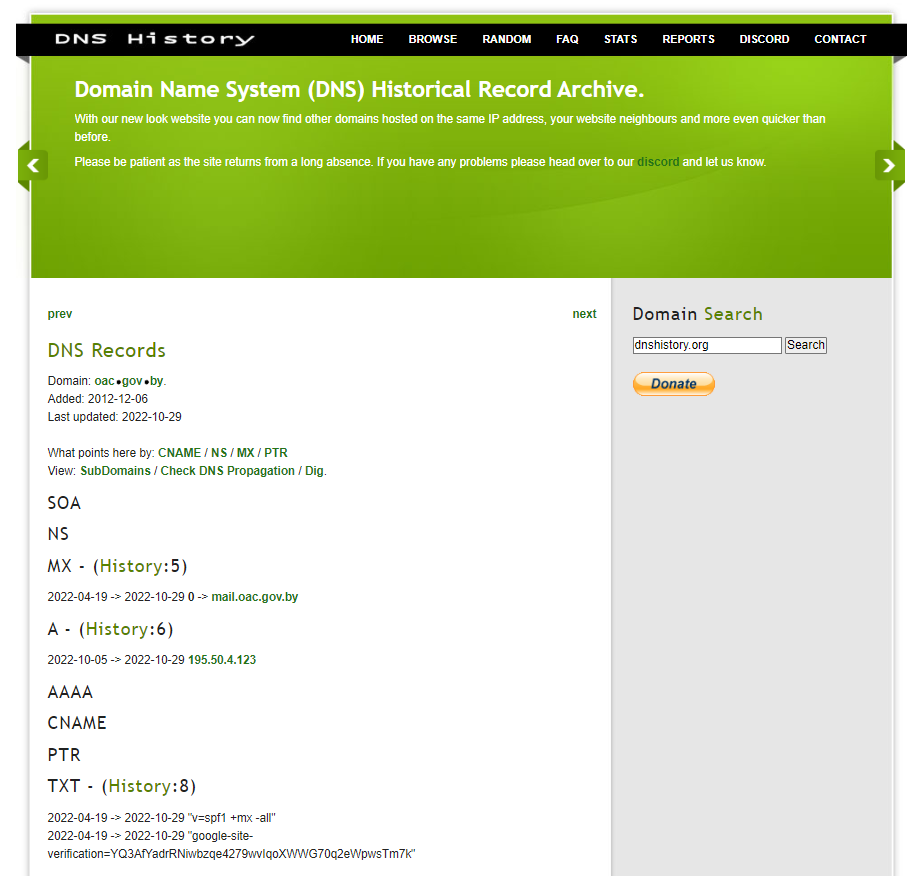
dnshistory : https://bit.ly/3SPbxkc
We can see that the domain has historical records dating from December 2012
We can find some interesting informations on this social network, such as technologies that the OAC may be actively using :
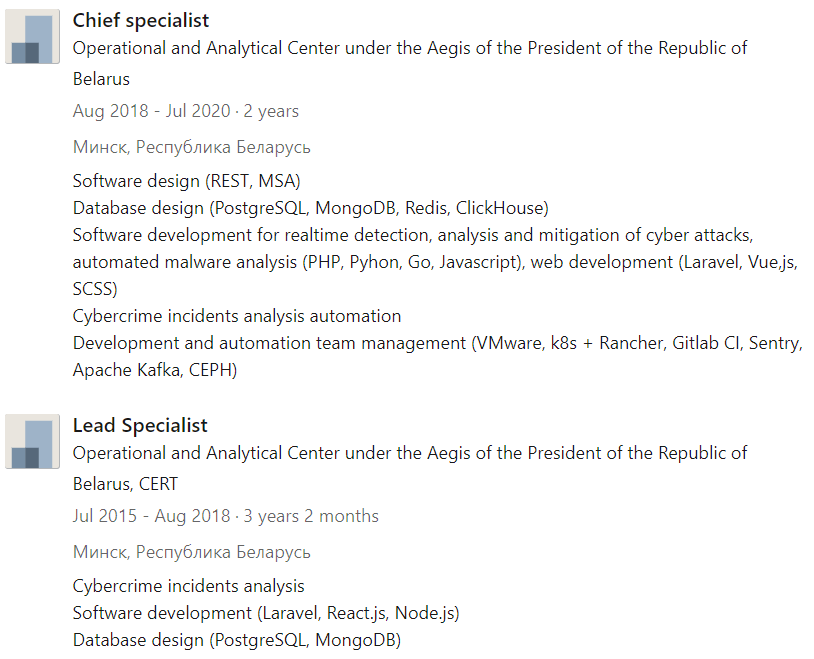
We can therefore correlate some technical evidences we had found in the previous sections, which increases the probability that the OAC actually uses these technologies
We can therefore assume the following architecture :
- Javascript Vue.js Frameworks for the Front-End
- PHP Laravel, Node.js, React.js Frameworks for the Back-End
- PostgreSQL, MongoDB for the database management
The softwares and services are probably based upon a Cloud Native architecture :
- VMware (Virtual Machines)
- Kubernetes k8s (to manage containerized applications across multiple hosts)
- Gitlab CI (Continuous Integration)
- CEPH as a distributed storage system (https://bit.ly/3Emillf)
p0f : https://bit.ly/3AbaEMb
p0f – passive operating system fingerprinting – can be used to detect the server Operating System (OS). It will detect how the OS implements the TCP/IP stack
In our case, I find that the server machine is based upon Windows XP
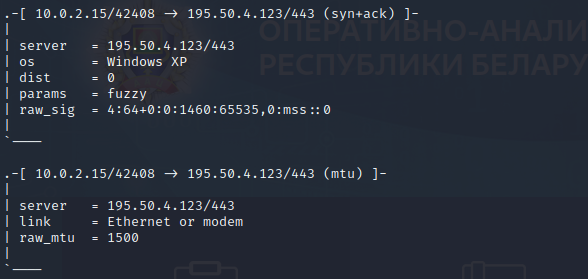
Is it weird to find such an outdated version of Windows ? Not quite. Some organizations are still using XP nowadays. For example, the Belarus railway system is using Windows XP, as it was shown to the world during the invasion of Russia into Ukraine (https://bit.ly/3GbVrhG)
In addition, Microsoft has decided to block new Windows licence to Belarus and Russia (https://bit.ly/3Trb5Ja), this will not help Belarus to move to more recent versions
Zenmap
We are going to find additional informations with Zenmap (in fact, it is a GUI version of nmap : https://bit.ly/2Hlfc7P)
The first one is the TCP Sequence Prediction (difficulty = 251 in our case), which is a measure of the risk that a TCP connection can be hijacked by an attacker, predicting the sequence number and preparing a faked packet (you can learn more about sequence number here https://bit.ly/3G9JPMb and also here https://bit.ly/3EsStUZ)
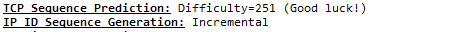
We find the open Ports and more technical informations about hardware used
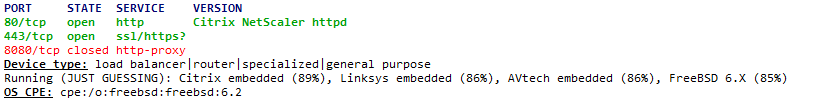
The open Ports 80 (HTTP) and 443 (HTTPS) are typical for a Web Server
We find a Citrix NetScaler, which is an Application Delivery Controller (ADC) created to optimize, manage, and secure network traffic : https://bit.ly/3X1Coww. This includes the Citrix WAF we have seen earlier
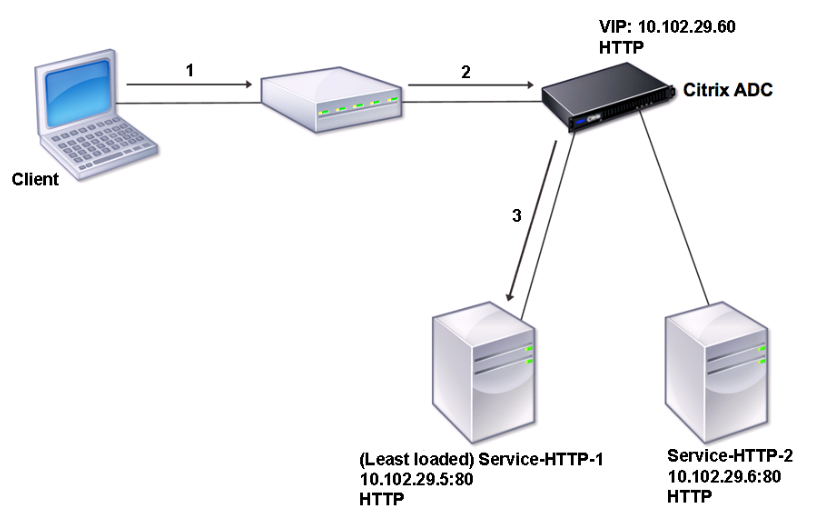
It is also probable that this ADC is acting as a Citrix VPX Load Balancer. A typical network topology would be as follows (VIP = virtual server IP), with internal machines hidden behind the Citrix ADC :
Zenmap provides probable infrastructure informations (with % of probability) :
- Citrix NetScaler VPX load balancer (89%) : as seen above
- Linksys BEFSR41 EtherFast router (86%) : it’s a basic network router
- AVtech Room Alert 26W environmental monitor (86%) : server room real time monitoring of temperature, humidity,…
- FreeBSD 6.2-Release (85%) : it’s probable that the server is based upon FreeBSD 6.2. If true, this is quite an outdated version. We can check the version 6.3 release notes to get an overview of the bugs in 6.2 : https://bit.ly/3UQUhMH
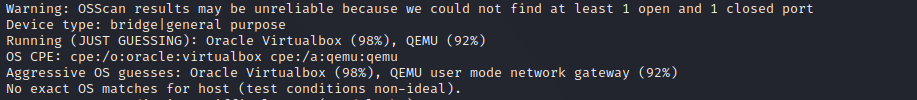
Let’s compare with a direct OS discover using nmap
nmap provides us with a probable guess, that FreeBSD 6.2 is based upon the Virtual Machine Oracle Virtualbox
Web security
We can dig a bit deeper if the web site is well protected, using a vulnerability scanner, such as Wapiti : https://bit.ly/3VxDZss
We get the following report :
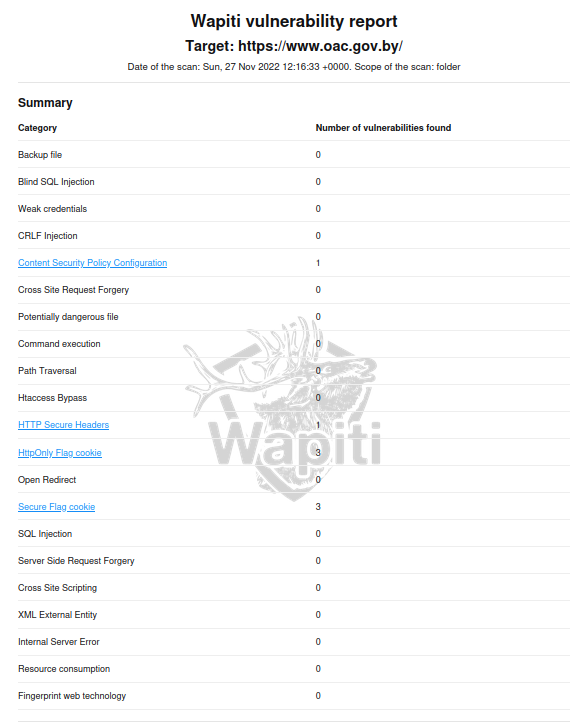
Let’s go through the results :
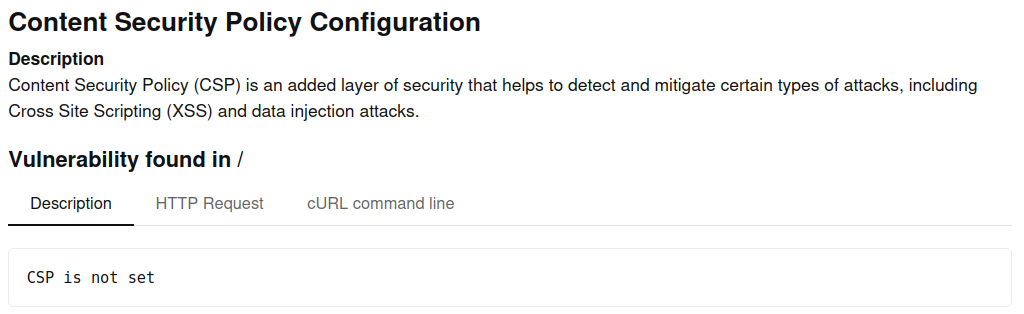
The Content Security Policy header (CSP) lets you precisely control permitted content sources and many other content parameters, and is a recommended way to protect your websites and applications against XSS attacks. A basic CSP header to allow only assets from the local origin is :
Content-Security-Policy: default-src 'self'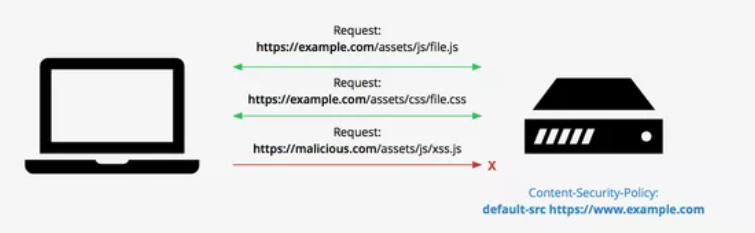
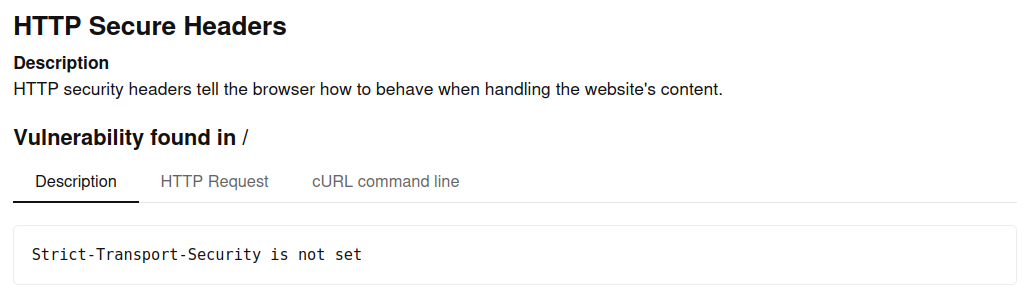
When enabled on the server, the HTTP Strict Transport Security header (HSTS) enforces the use of encrypted HTTPS connections instead of plain-text HTTP communication. A typical HSTS header might look like this:
Strict-Transport-Security: max-age=63072000; includeSubDomains; preloadThis informs any visiting web browser that the site and all its subdomains uses only SSL/TLS communication, and that the browser should default to accessing it over HTTPS for the next two years (the max-age value in seconds)
The preload directive indicates that the site is present on a global list of HTTPS-only sites. The purpose of preloading is to speed up page loads and eliminate the risk of man-in-the-middle (MITM) attacks when a site is visited for the first time
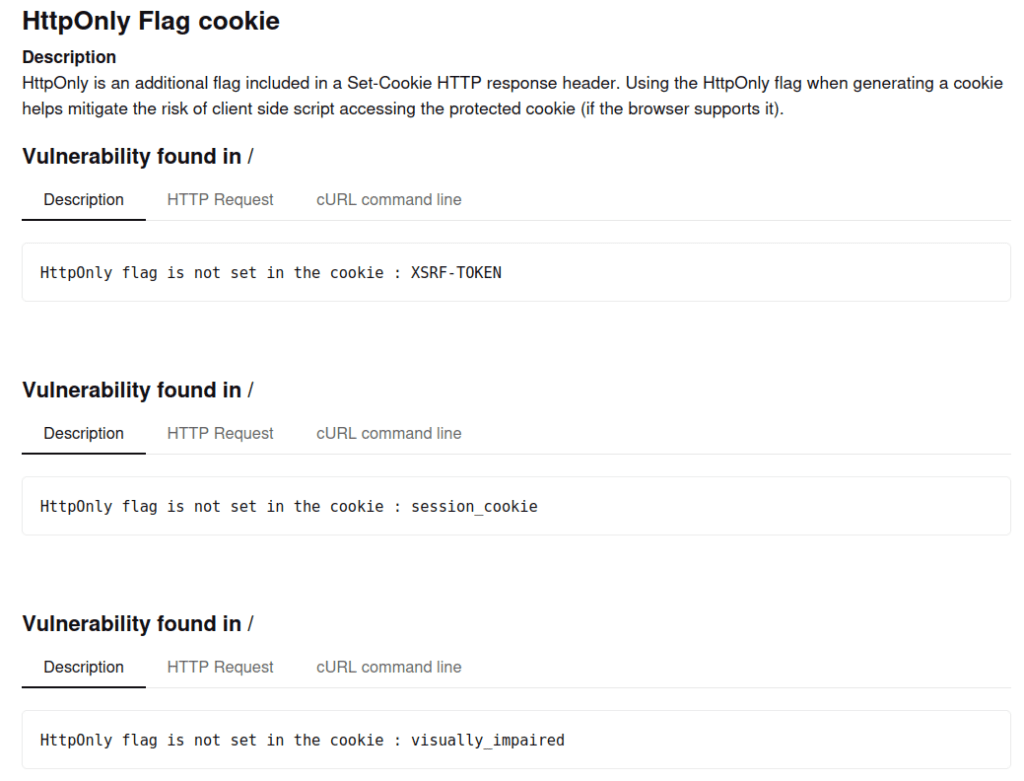
An HttpOnly Cookie is a tag added to a browser cookie, that prevents client-side scripts from accessing data. Using the HttpOnly tag when generating a cookie helps mitigate the risk of client-side scripts accessing the protected cookie, thus making these cookies more secure.
The example below shows the syntax used within the HTTP response header :
Set-Cookie: =“[; “=“] [; expires=“][; domain=“] [; path=“][; secure][; HttpOnly]
If the HttpOnly flag is included in the HTTP response header, the cookie cannot be accessed through the client-side script. As a result, even if a cross-site scripting (XSS) flaw exists, and a user accidentally accesses a link that exploits the flaw, the browser will not reveal the cookie to the third-party
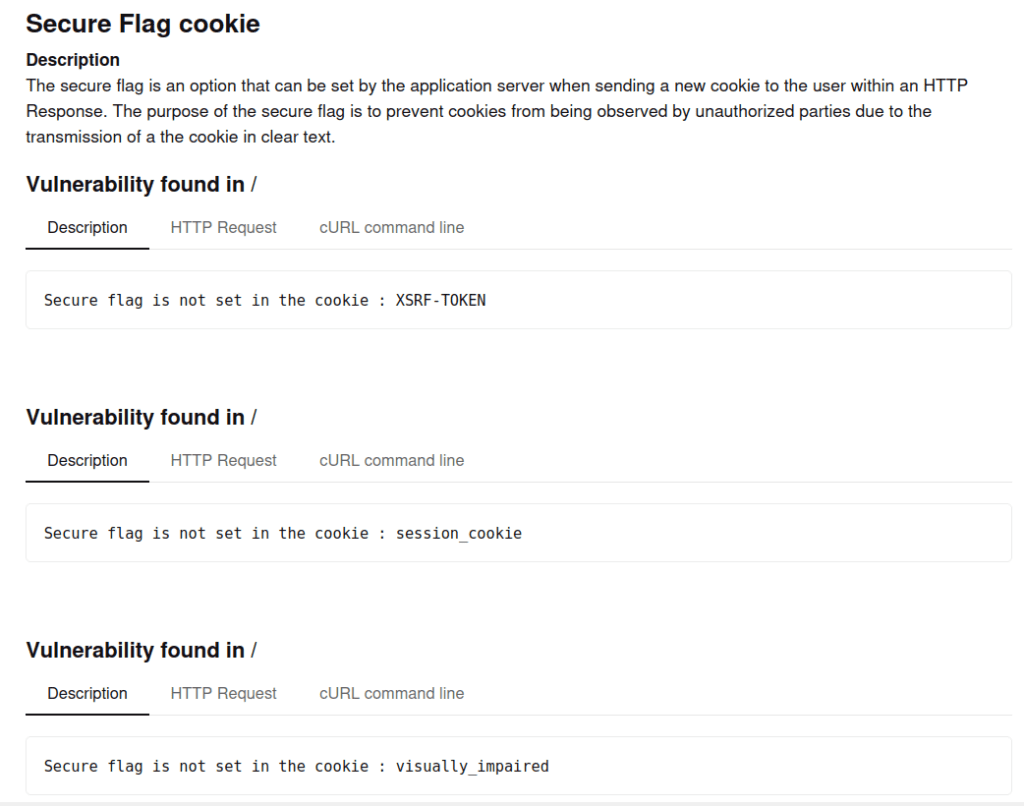
The Secure flag is used to declare that the cookie may only be transmitted using a secure connection (SSL/HTTPS). If this cookie is set, the browser will never send the cookie if the connection is HTTP. This flag prevents cookie theft via man-in-the-middle attacks
It would be good practice to enable the above security flags, thus complying with the OWASP recommendations. However, I assume that the OAC is not so concerned, as the website does not include many rich content, and a powerfull WAF is already implemented
Belarus web infrastructure in summary
Let’s summarize the infrastructure that we have seen above
| Entity | Key observation | Comment |
|---|---|---|
| Belarus TLD | Name Servers are hosted in several countries | Belarus (beCloud), Russia (Dataline), USA (AWS) |
| beCloud | Sovereign Cloud and Internet infrastructure | Built with the support of many international corporations |
| oac.gov.by | IP owned by Belarusian Cloud Technologies | State owned Beltelecom has control over most of the Internet infrastructure |
| oac.gov.by | Chief inspector of the Belarus TLD | Entitled by Law to restrict internet, in case of threats to National Security |
| BelGIE | Responsible to optimize the traffic and filter IP addresses as per the need | DPI (Deep Packet Inspection) as per the need. Got support from Sandvine in the past for traffic optimization (including filtering) |
| oac.gov.by | Performs analytics using Google web tracking | Google Tag Manager, Doubleclick |
| oac.gov.by | WAF and Load Balancer implemented using Citrix | Citrix NetScaler Citrix VPX Load Balancer |
| oac.gov.by | Encryption of the website using TLS1.3 and AES256 | Certificate issued by Let’s Encrypt |
| oac.gov.by | Web server machine | The web server may use a Windows XP machine, with an nginx server |
oac.gov.by | Web server OS | Managed by a FreeBSD controller, built upon an Oracle VM Virtual Box |
| oac.gov.by | Web security | Some usual basic security flags are missing, but the website is protected using a WAF |
Conclusion
In this short preview of the Belarus web infrastructure, we have seen the following items, using footprinting methods :
- Belarus has built a sovereign cloud to manage its web infrastructure, with the help of international corporations (US, Europe, Asia,..)
- The Belarus Name Server is backed-up by AWS (USA) and Dataline (Russia)
- The Belarus authorities have a strong degree of control over access points and can block any IP traffic if necessary (such as during the August 2020 elections turmoil)
- The Operational and Analytical Center (OAC) is the chief inspector of the Belarus Top Level Domain (TLD)
- The OAC website performs analytics using Google web tracking technology
- The OAC website is protected with the use of Citrix technology (WAF, Load Balancer), and its root certificate is issued by Let’s Encrypt
- The OAC web server may be based upon an obsolete version of Windows (XP) and does not comply with all the basic OWASP recommendations
- The restrictions applied to Belarus by some US corporations such as Microsoft will limit their ability to implement security patches and updates
- Linkedin profiles are always a good way to learn more about the technologies used by a target
