In the following articles, I will focus on Computer Forensics techniques. Instead of writing a general or theoretical article, I decided to search for test images and provide a technical walkthrough of simulated test images
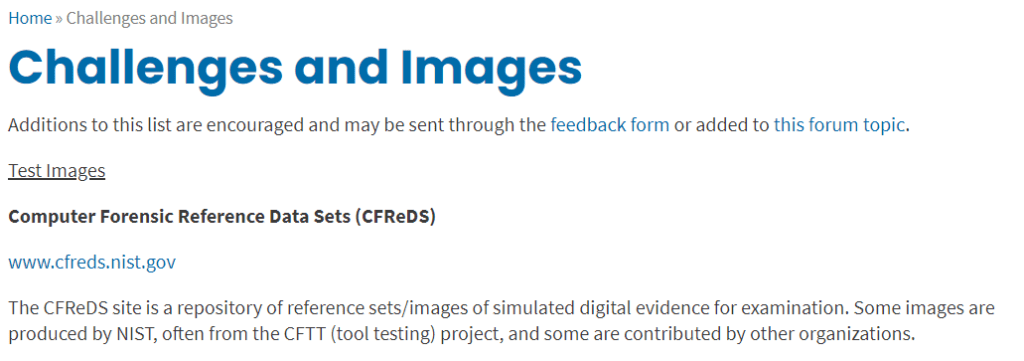
I found an excellent website for this : https://www.forensicfocus.com/challenges-and-images/, were you can practically train yourself to Computer Forensics. On the home page, please follow the link to the NIST website where you can access several test images : https://www.cfreds.nist.gov/
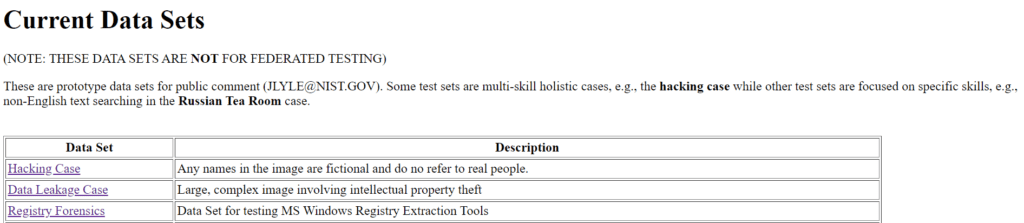
In this first article, I have taken a test image called “Hacking Case“. There has been several reviews of this case already with published solutions, so I hope that my article brings some value to you guys
The scenario is the following
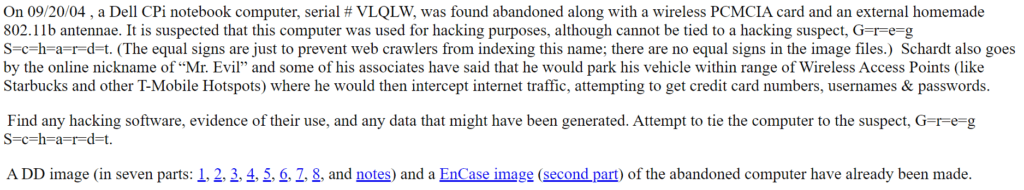
This is quite vintage…so, an old Dell CPi notebook computer has been found and it is suspected that a so called hacking suspect “Greg Schardt“, is the owner of this device. A hard drive disc image has been generated and made available to us for analysis

Where to start from ? We have a disc drive image (split in 8 parts) and also an EnCase image…what is the difference ? Should we consider both in our analysis, or choosing one of the two images is ok ?
EnCase is one of the most popular computer forensic solution available : https://www.guidancesoftware.com/encase-forensic. It has far reaching capabilities for forensic analysis. An EnCase image was obtained using the EnCase Imager software : https://www.guidancesoftware.com/document/product-brief/encase-forensic-imager
The final format of the image will be the same, either using the disc drive image or the EnCase image. It will be a file full of exotic symbols, that you can see by yourself just clicking on one of the image link : https://www.cfreds.nist.gov/images/4Dell%20Latitude%20CPi.E01
What are these symbols ? These are just Unicode representation of the raw datas encoded into the Hard Disc Drive. It’s not quite human readable, it’s not meant to be in fact…a computer program will do it for you, interpreting the raw data into a human readable format. An Hex Editor will be a first step to represent this data into HEX format, in a more structured way (that’s just an example, no need to do this step to continue reading the article)
So, as the raw images and the EnCase images are in the same format, I chose the EnCase one
I am using the Free Download Manager for this : https://www.freedownloadmanager.org/fr/ Just copy the link of the image file into this tool and it will download the data into one file for you, pretty neat
For the analysis of the image, I’m using the open source Autopsy software for Windows (no need to register to download) : https://www.autopsy.com/download/
The installation is pretty straightforward. Once it’s done, just start a new “Case” in Autopsy by loading the forensic image. You then land on the main screen of this nice software. On this home screen, you will find the image at the top left side. Just right click on it and select “View Summary Information”, and you will find some basic informations allowing to answer the first questions
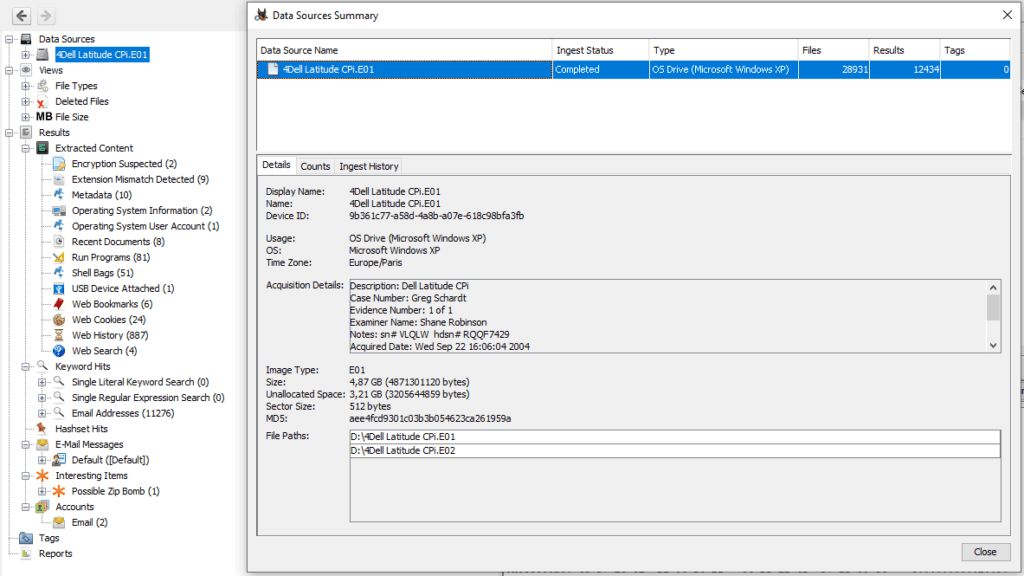
1. What is the image hash? Does the acquisition and verification hash match ?
The hash is an MD5, it’s value is AEE4FCD9301C03B3B054623CA261959A. Just to remind, this is a unique identifier coming from an MD5 algorithm calculation applied to the file content. It allows a unique identification of the source file
However, the acquisition hash is not given, so I’m not able to compare acquisition and verification hash
2. What operating system was used on the computer ?
You can see immediately that it’s a Windows XP operating system. I told you, it’s vintage !
Looking into the C:\boot.ini file, we find it’s a Professional version
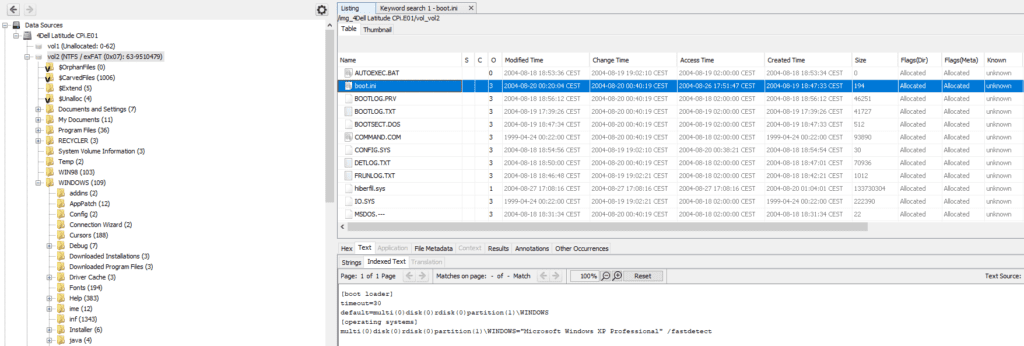
3. When was the install date ?
It seems that there was initially a Windows 98 version installed, followed by an installation of Windows XP (update process) on the 19/08/2004 at 17:35:37 time
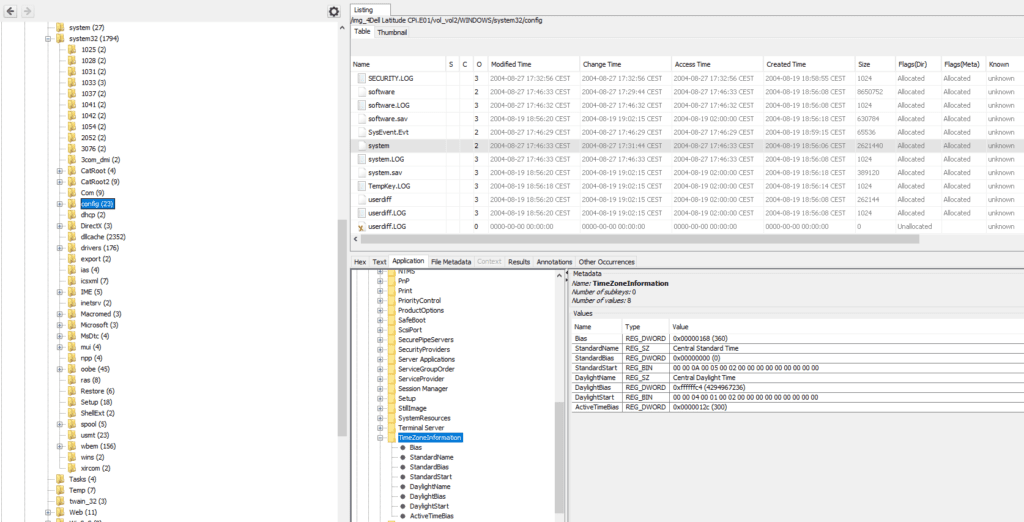
4. What is the timezone settings ?
Using Autopsy, we can navigate through the registry. It can be found in Windows\System32\Config folder. In this directory, we can navigate through the files in the top right hand window of Autopsy, which lets the registry informations unfold in the bottom right hand window. Here we go !
First, we have a system registry key set to “Central Standard Time” zone, in system\ControlSet001\Control\TimeZoneInformation :
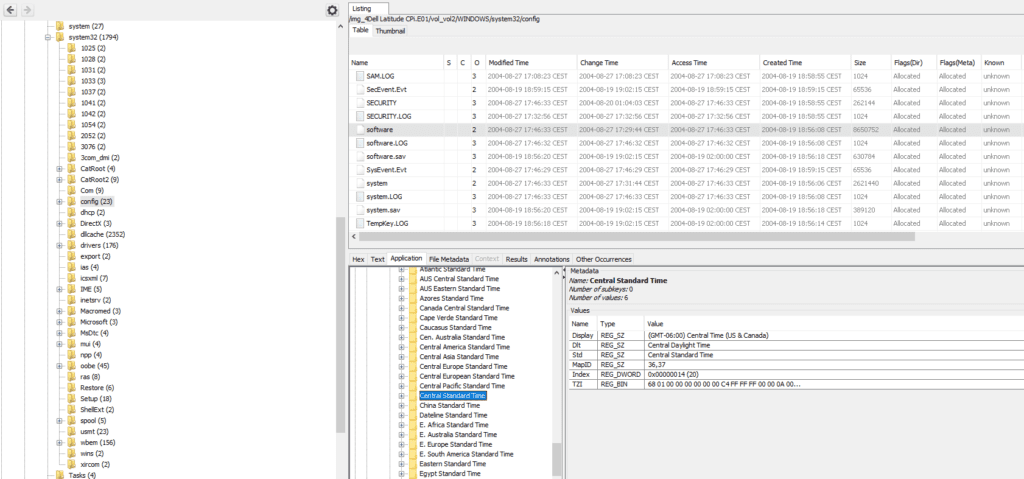
Second, we have another important registry key in software\Microsoft\Windows NT\CurrentVersion\Time Zones, which contains the exact time zone : GMT – 06:00
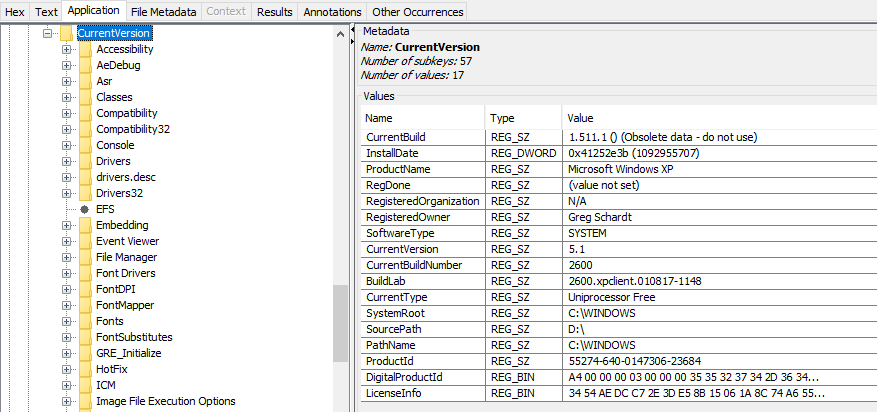
5. Who is the registered owner ?
In software\Microsoft\Windows NT\CurrentVersion, we find that the registered owner is Greg Schardt
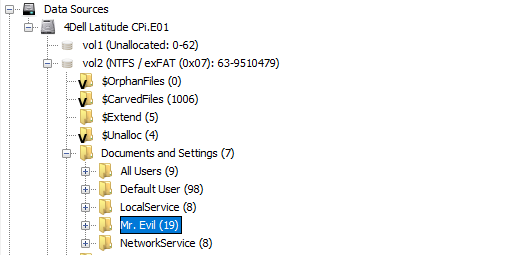
6. What is the computer account name ?
It can be found in Documents and Settings : Mr. Evil
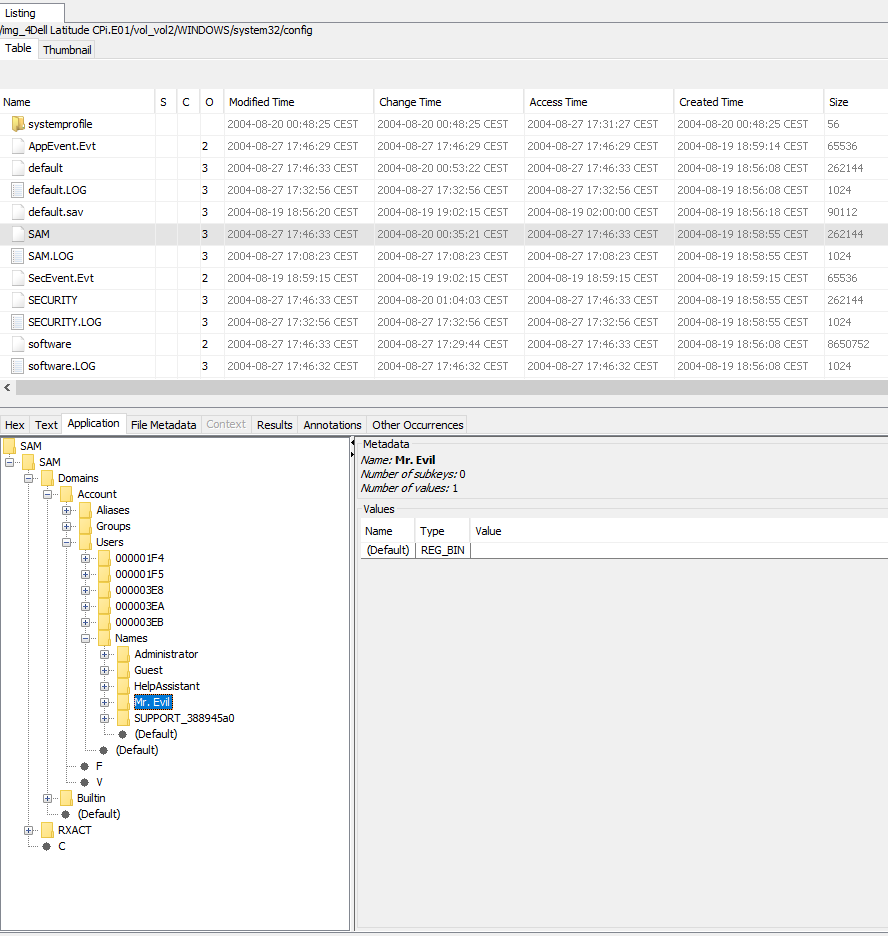
or, it can be found also in the registry, in the SAM file
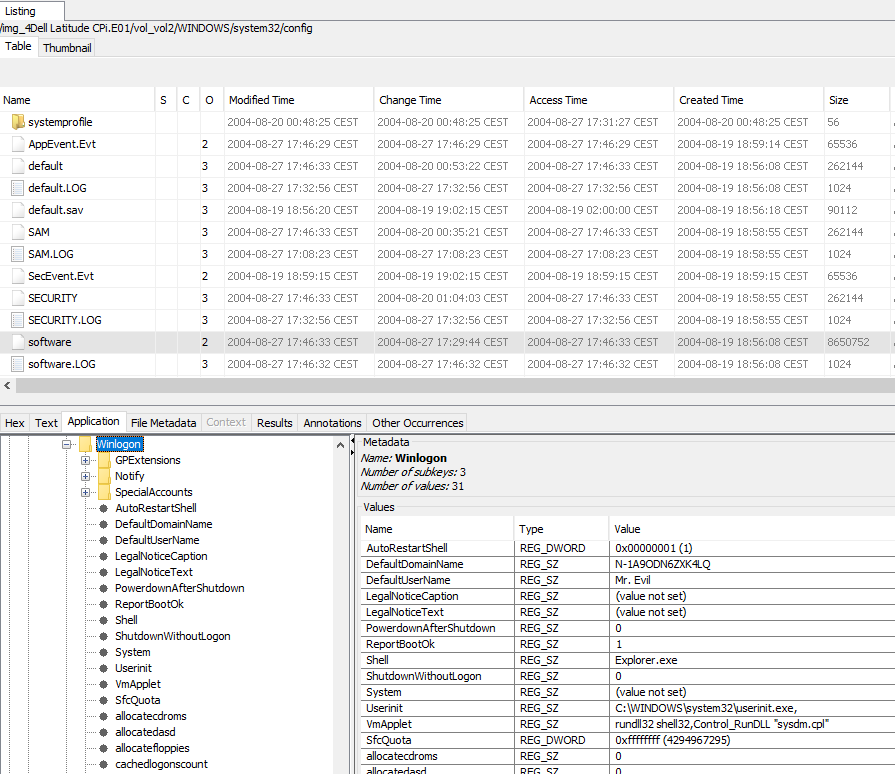
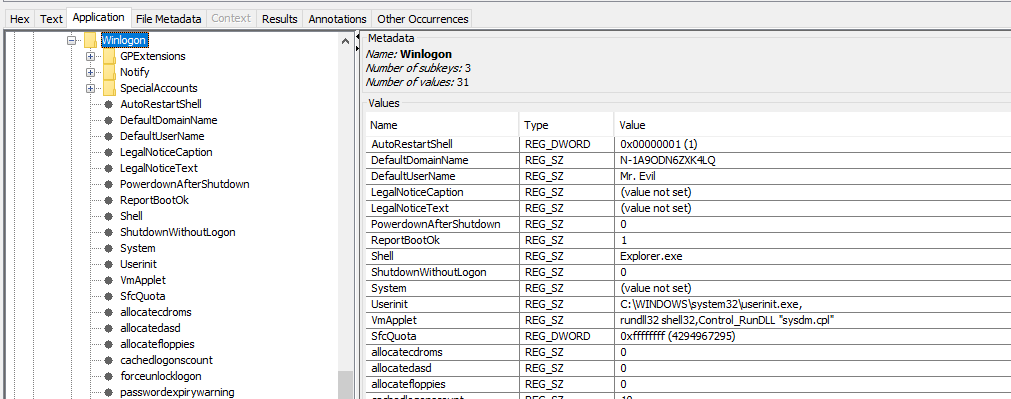
7. What is the primary domain name ?
It is N-1A9ODN6ZXK4LQ, which can be found in software\Microsoft\Windows NT\CurrentVersion\Winlogon
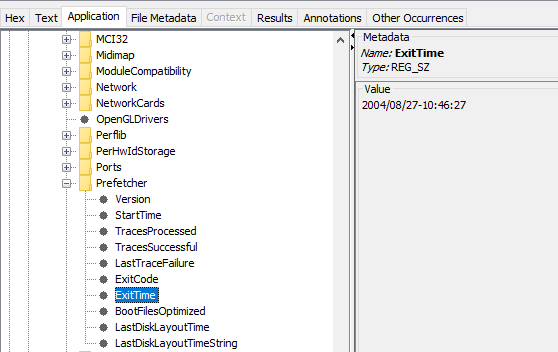
8. When was the last recorded computer shutdown date/time ?
To find this, we go to the below registry key : software\Microsoft\WindowNT\CurrentVersion\Prefetcher\ExitTime
We find a shutdown date/time of 27/08/2004–10:46:27
9. How many accounts are recorded (total number) ?
In question 6, we had found already the 5 user names : Administrator, Guest, HelpAssistant, Mr. Evil, SUPPORT_388945a0
10. What is the account name of the user who mostly uses the computer ?
Mr. Evil is the only real user of this computer, as can be seen in Operating System User Account (1)
11. Who was the last user to logon to the computer ?
The name of the last user who logged on successfully appears in the key DefaultUserName in software\Microsoft\Windows NT\CurrentVersion\Winlogon : it’s Mr. Evil !
12. A search for the name of “Greg Schardt” reveals multiple hits. One of these proves that Greg Schardt is Mr. Evil and is also the administrator of this computer. What file is it? What software program does this file relate to ?
We have seen that Greg Schardt is the registered owner of the device, while Mr. Evil is the only user of the system. We therefore can believe this is the same person
The search for the name Greg Schardt brings us to this result :
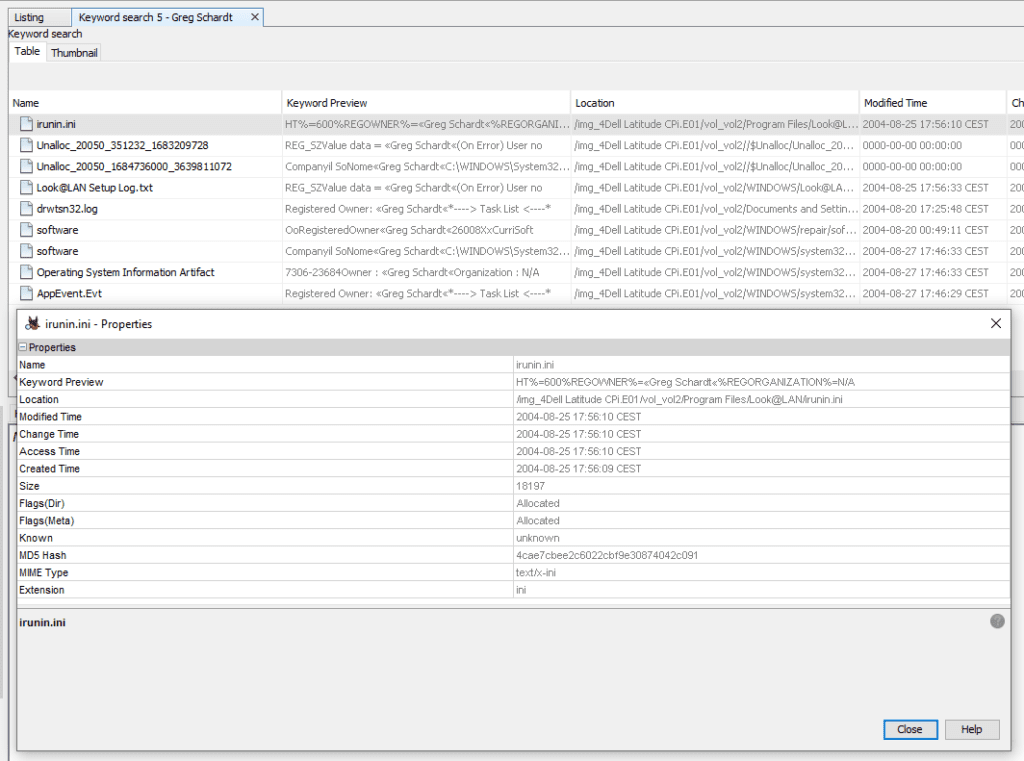
We can see, in Program Files, a program called Look@LAN. It’s a portable application that allows a user to monitor which clients are connected to a local network (LAN = Local Area Network) : https://www.majorgeeks.com/files/details/looklan.html
The Program Files Look@LANirunin.ini ties us to Mr. Evil as a LAN user, which proves us the link with Greg Schardt !
13. List the network cards used by this computer
There are 2 network cards in use in software\Microsoft\Windows NT\CurrentVersion\NetworkCards :
Compaq WL110 Wireless LAN PC Card

Xircom CardBus Ethernet 100 + Modem 56 (Ethernet Interface)

14. This same file reports the IP address and MAC address of the computer. What are they ?
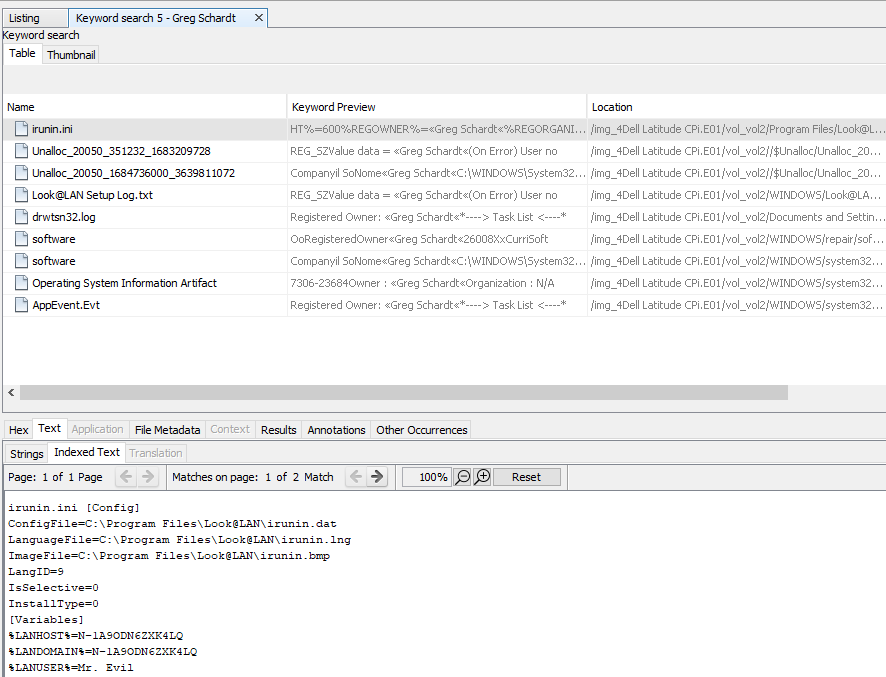
The question is not immediately clear, but you get the idea when considering the software Look@LAN monitors the clients connected to the local network. To search again for the file we already opened in question 12, just type in the top right search bar, the file name irinin.ini
Inside this file, you will easily find the following :
%LANIP%=192.168.1.111 -> usually this IP identifies a PC on a local network (so it makes sense to find this IP !)
%LANNIC%=0010a4933e09 -> a simple MAC adress lookup tool such as https://rst.im/oui/, will confirm this is a Xircom adress. It makes sense with question 13 !
15. An internet search for vendor name/model of NIC cards by MAC address can be used to find out which network interface was used. In the above answer, the first 3 hex characters of the MAC address report the vendor of the card. Which NIC card was used during the installation and set-up for LOOK@LAN ?
The configuration file of LOOK@LAN is irunin.ini. Let’s open again this file. We find the below informations inside this file :
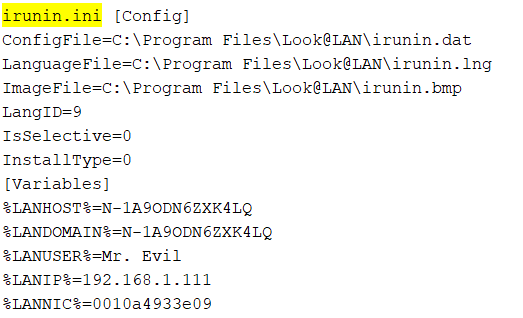
So, it’s clear that the NIC – Network Interface Card used during the installation and setup, is the card with the MAC adresss 0010a4933e09, that is the Xircom CardBus Ethernet 100 + Modem 56 (Ethernet Interface)
16. Find 6 installed programs that may be used for hacking
Looking into the Program Files, it’s pretty easy to find the following programs :
123WASP : https://www.techspot.com/downloads/107-123-write-all-stored-passwords.html
Anonymizer : https://news.hitb.org/content/anonymizer-launches-free-anonymizer-privacy-tool-ms-ie-browser
Cain : https://myhackingworld.com/cain-and-abel/
Ethereal : https://hackersonlineclub.com/what-is-ethereal-hacking/
(NB : since that time, it has been renamed into Wireshark, the famous network packet sniffing tool https://www.wireshark.org/download.html)
Look@LAN : https://www.techspot.com/community/topics/look-lan.64758/
NetStumbler : https://dudehackingtricks.wordpress.com/2014/08/14/netstumbler-hack-wifi-password/
17. What is the SMTP email address for Mr. Evil ?
To find this information, you could look into the AGENT.INI file. See more about this file in previous versions of Windows :
https://groups.google.com/forum/#!topic/alt.usenet.offline-reader.forte-agent/23uh0mRbq88
The file is located in Program Files\Agent\Data\AGENT.INI
We find the email adress of Mr. Evil : whoknowsme@sbcglobal.net
18. What are the NNTP (news server) settings for Mr. Evil ?
NNTP stands for Network News Transfer Protocol (Newsgroup / Usenet) : https://ccnatutorials.in/application-layer-of-tcp-ip/nntp-network-news-transfer-protocol/
Again, a search in the AGENT.INI file will let you find the information
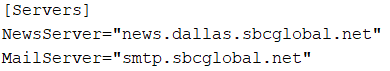
19. What two installed programs show this information ?
We need to look for mail client and/or Usenet client. One source to look into this is NTUSER.DAT, which is a well known Forensic source
We find that MS Outlook Express reveals the email adress of Mr. Evil. To find this, you need to look into NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\UnreadMail
Just type in NTUSER.DAT in the search bar, and navigate in the file structure
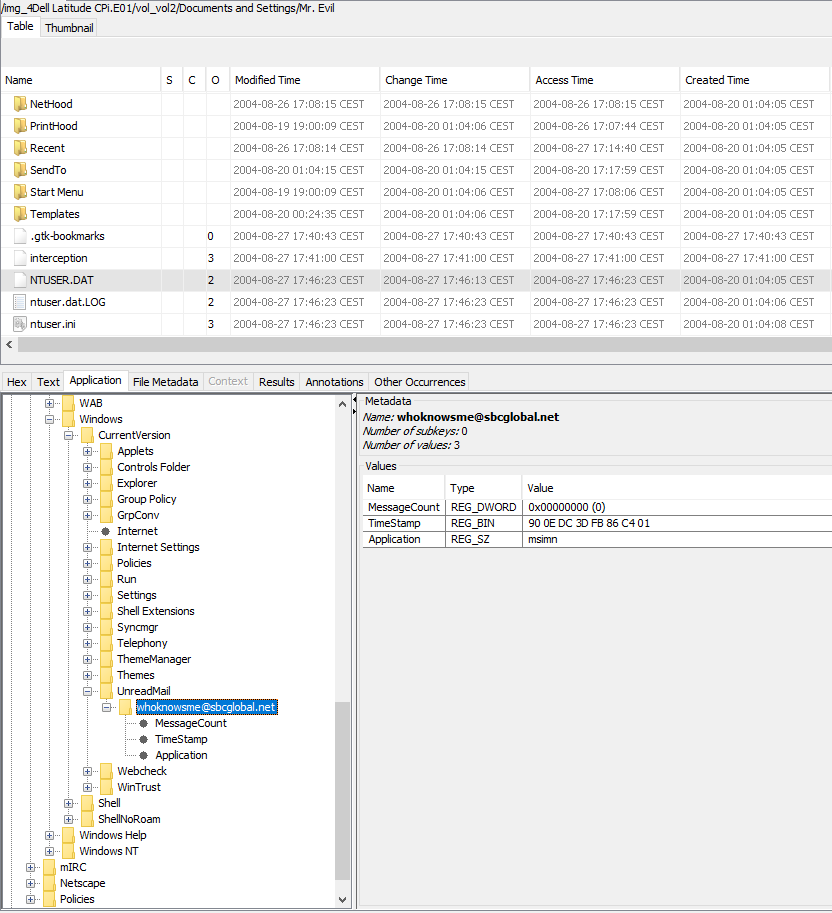
At this moment, I’m not able to find the second program revealing the same information…if you find it, please put it in the comment section !
20. List 5 newsgroups that Mr. Evil has subscribed to ?
There is a good article to understand Outlook Express forensics : https://www.mailxaminer.com/blog/outlook-express-email-forensics/
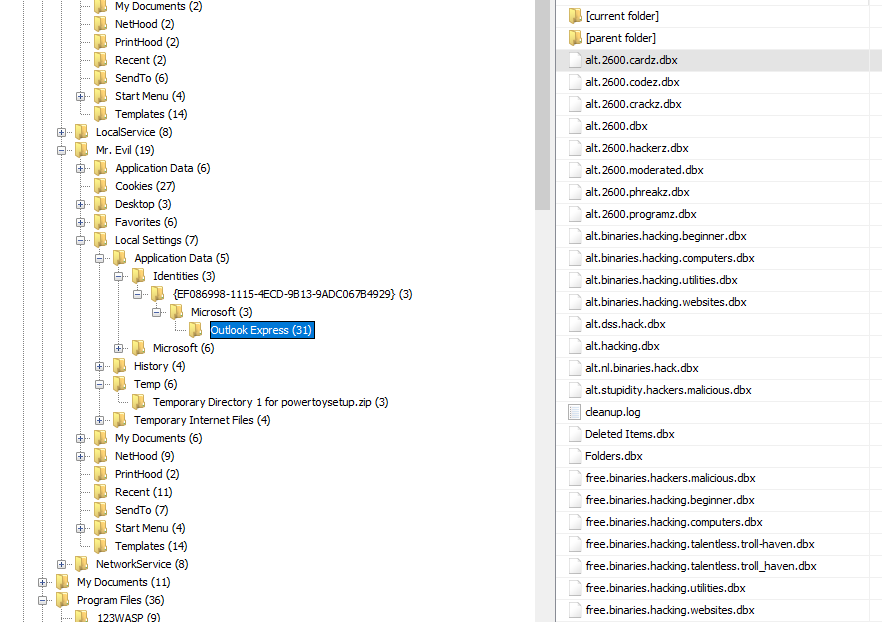
All the Outlook Express email folders and messages, local IMAP folders and settings are stored in one folder. The location of this directory is :
Documents and Settings\user_name\Local Settings\Application Data\Identities\Microsoft\Outlook Express
We find many newsgroup to which Mr. Evil has suscribed !
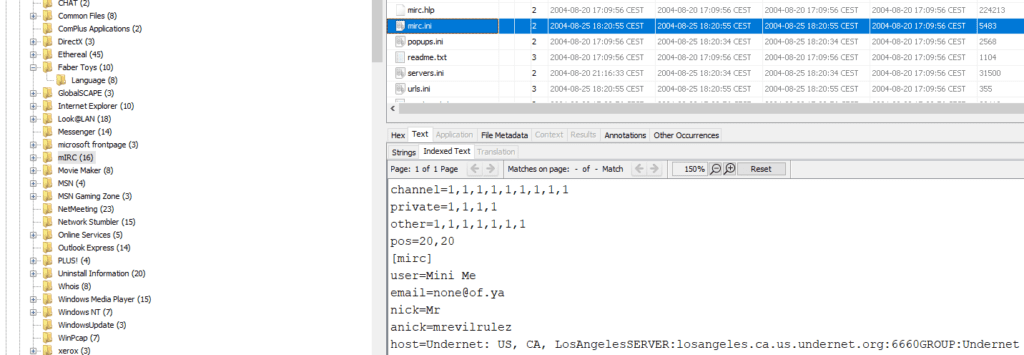
21. A popular IRC (Internet Relay Chat) program called MIRC was installed. What are
the user settings that was shown when the user was online and in a chat channel ?
The mIRC program (https://www.mirc.com/) can be found in the Program Files
Just open and check through the mirc.ini and you will get the requested information
user=Mini Me
email=none@of.ya
nick=Mr
anick=mrevilrulez
22. This IRC program has the capability to log chat sessions. List 3 IRC channels that the
user of this computer accessed
The log section if mIRC in the Program Files section, reveals their is a “logs” directory. The chat sessions immediately appear here
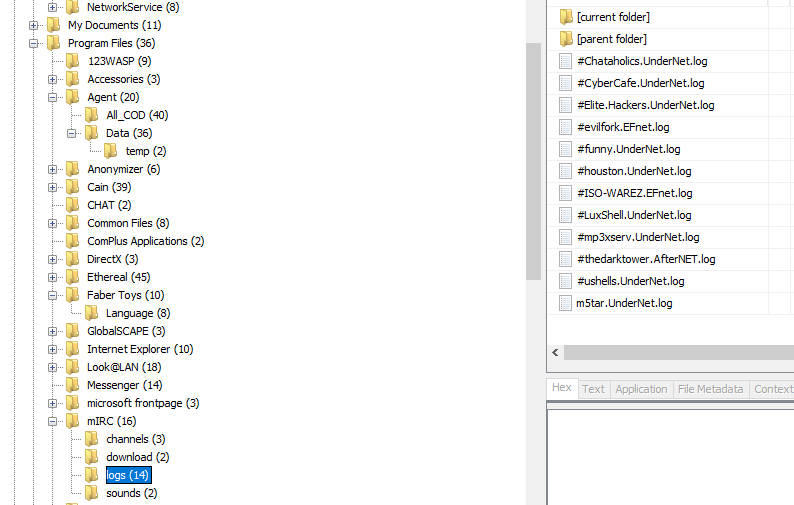
23. Ethereal, a popular “sniffing” program that can be used to intercept wired and
wireless internet packets was also found to be installed. When TCP packets are collected
and re-assembled, the default save directory is that users \My Documents directory. What is the name of the file that contains the intercepted data ?
Searching into the Ethereal directory, we find a “recent” file. Open this file reveals the requested information “interception“
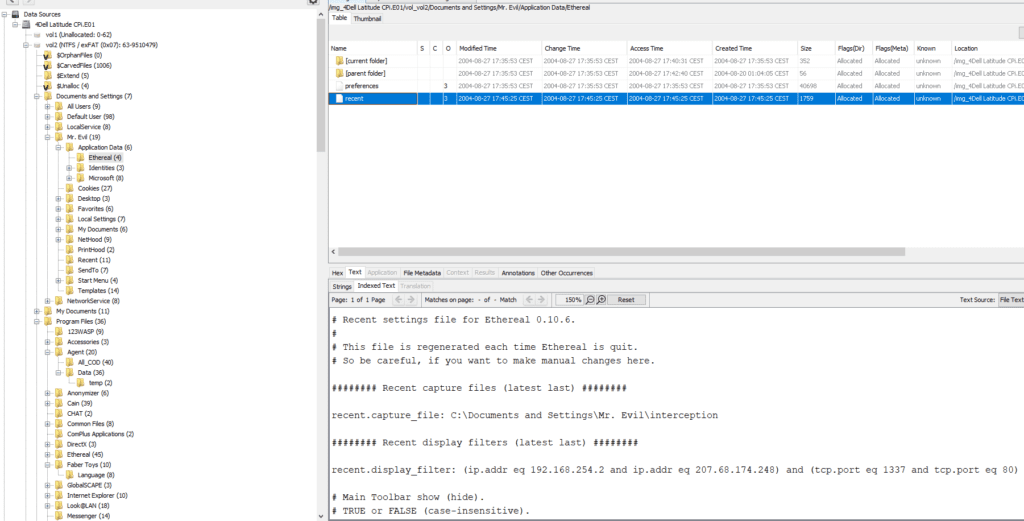
24. Viewing the file in a text format reveals much information about who and what was
intercepted. What type of wireless computer was the victim (person who had his internet
surfing recorded) using ?
The interception file can be found typing “interception” in the search bar on the top right of the home screen
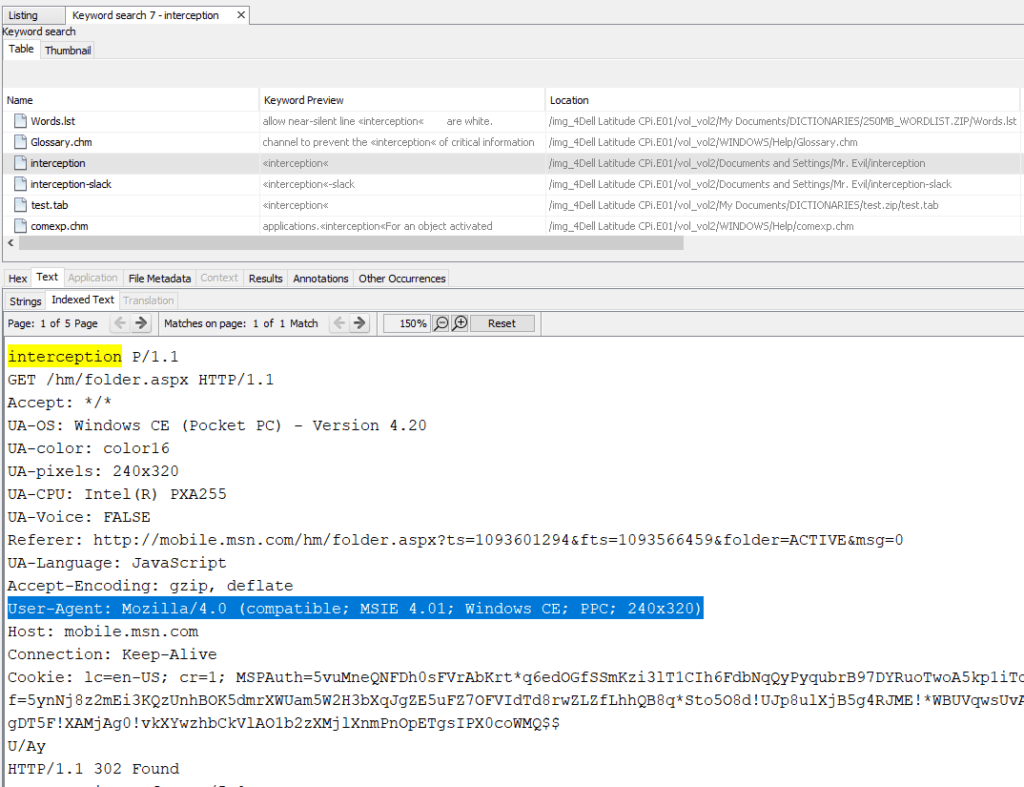
The user agent is a Microsoft Internet Explorer 4.01 using a Pocket PC with Windows CE, screen resolution 240×320. I told you, it’s vintage !
25. What websites was the victim accessing ?
The victim was accessing mobile.msn.com, as can be seen in the interception file. We can see down below that the victim was also using MSN hotmail (email)

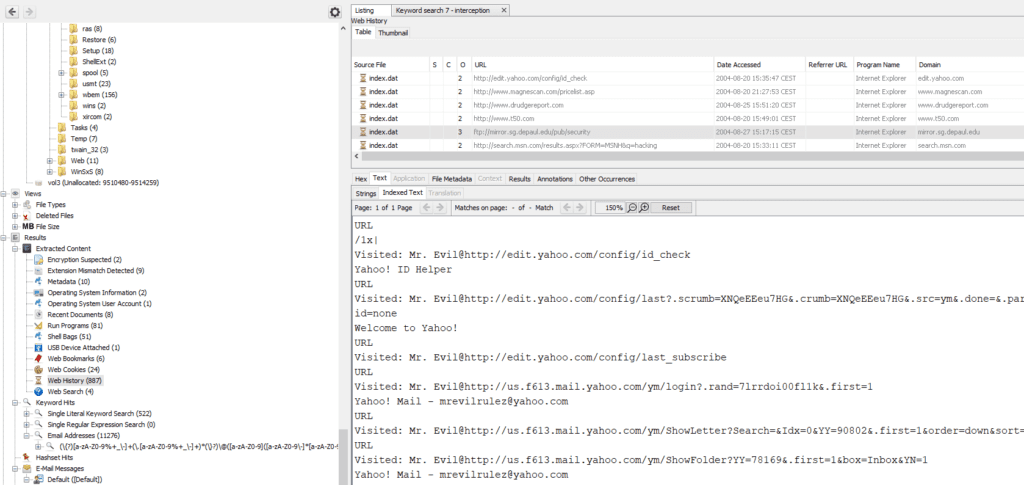
26. Search for the main users web based email address. What is it ?
In the Extracted content web history, you can find many historical browsing files. Searching through these files, you can see some instances were the user had to login. It reveals the email adress mrevilrulez@yahoo.com (we already found this name in question 21)
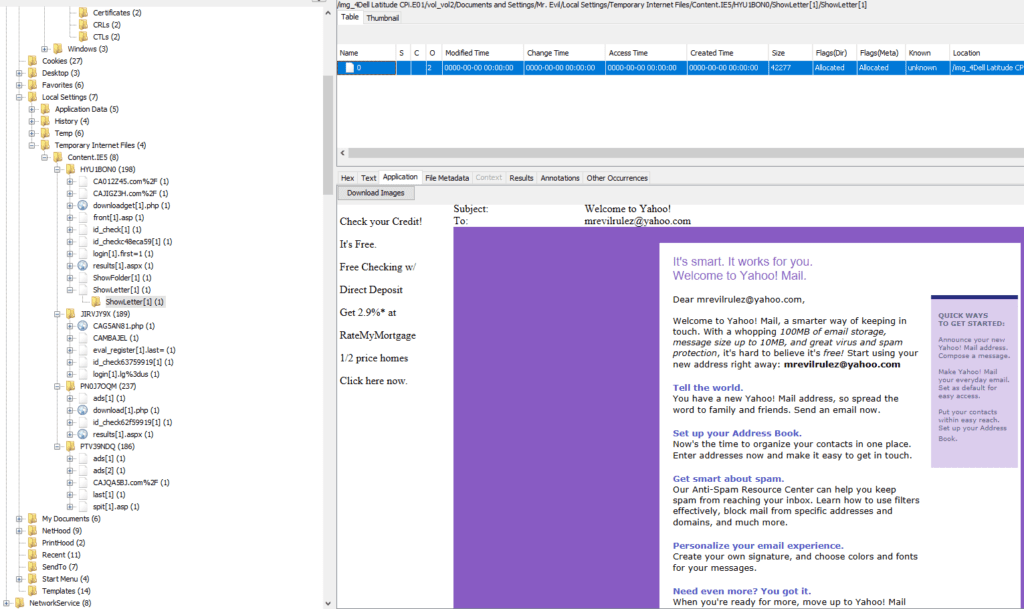
27. Yahoo mail, a popular web based email service, saves copies of the email under what
file name ?
The Yahoo emails are stored under “ShowLetter[1]“
We can confirm the email adress used by Mr. Evil
28. How many executable files are in the recycle bin ?
There are 4 executables in the recycle bin
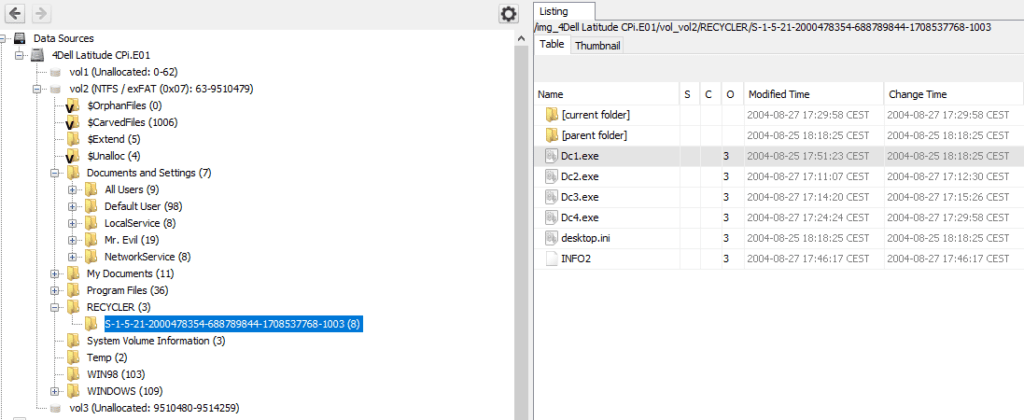
29. Are these files really deleted ?
No, they are just moved to the recycle bin and not deleted…!
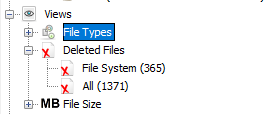
30. How many files are actually reported to be deleted by the file system ?
It is pretty easy. Just browse to “View” and you will find the counter “All” -> 1 371 files were deleted. Thanks to “bobo” for the tip !
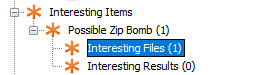
31. Perform an Anti-Virus check. Are there any viruses on the computer ?
Yes, there is a zip bomb present, unix_hack.tgz
It’s found in the “Interesting Items” section
This is what Wikipedia says about zip bombs
Here is an example of a famous zip bomb (try with caution !) : https://www.unforgettable.dk/
Conclusion :
After this writeup, it is clear now that Greg Schardt and Mr. Evil are just one single person. The seized laptop is including hacking software that was used to sniff data from victims, chat on hackers newsgroup and IRC, contain a zip bomb. So, all suspicions about Greg Schardt were true !
One can only be amazed by the power of forensic tools such as Autopsy. It’s quite amazing all the data stored in your PC, that can be recovered by someone knowing were to look at. Be carefull with your data ! Don’t think you can hide on Internet !
Additional note :
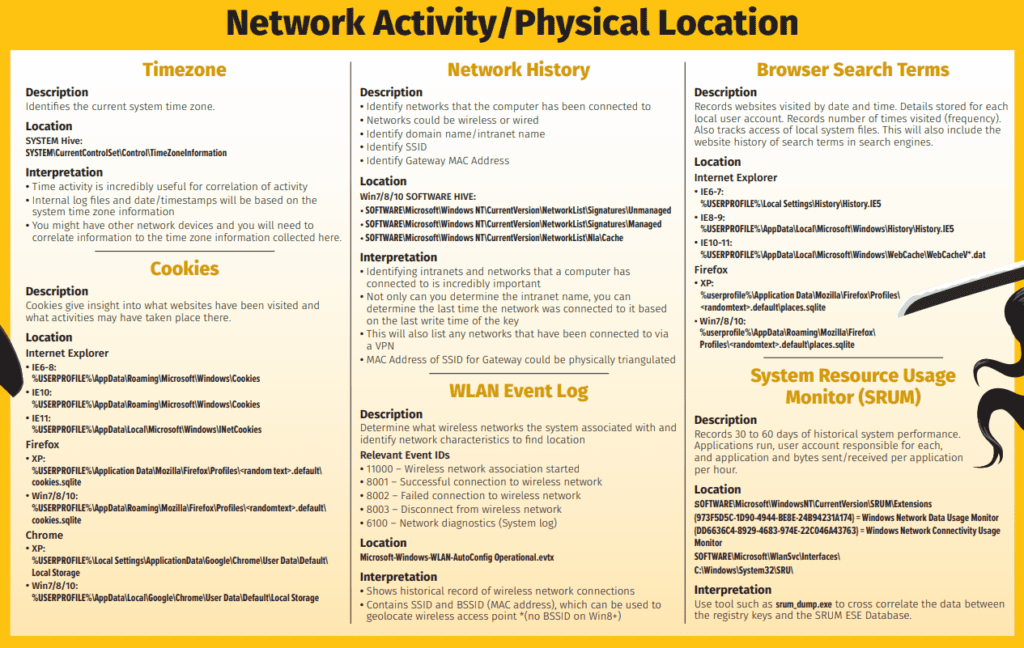
I would like to share an excellent ressource I found from the DFIR – Digital Forensics and Incident Response (SANS training and certification institute). It helped me a lot to walk through this challenge. You can download an excellent PDF on this page : https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
See below an example of the sections you find in this PDF. It’s a very helpfull checklist !